When parsing a JPEG file, the Jhead application will look for the string "COMMAND: \r
" at the beginning of the file and then execute the following command: /bin/bash -c 'eval "$(echo " $(basename $1)")"' When parsing a JPEG file, the Jhead application will look for the string "" at the beginning of the file and then execute the following command: /bin/bash -c 'eval "$(echo ""')"' CVE-2018-1000111: This issue is currently rated as Medium severity due to the fact that it can be exploited by an attacker to execute arbitrary commands. It should be noted that Jhead 3.06.0.1 is not widely used, making it likely that not many people are at risk of being affected by this issue. However, it is still important to upgrade to the latest version of Jhead as soon as possible.
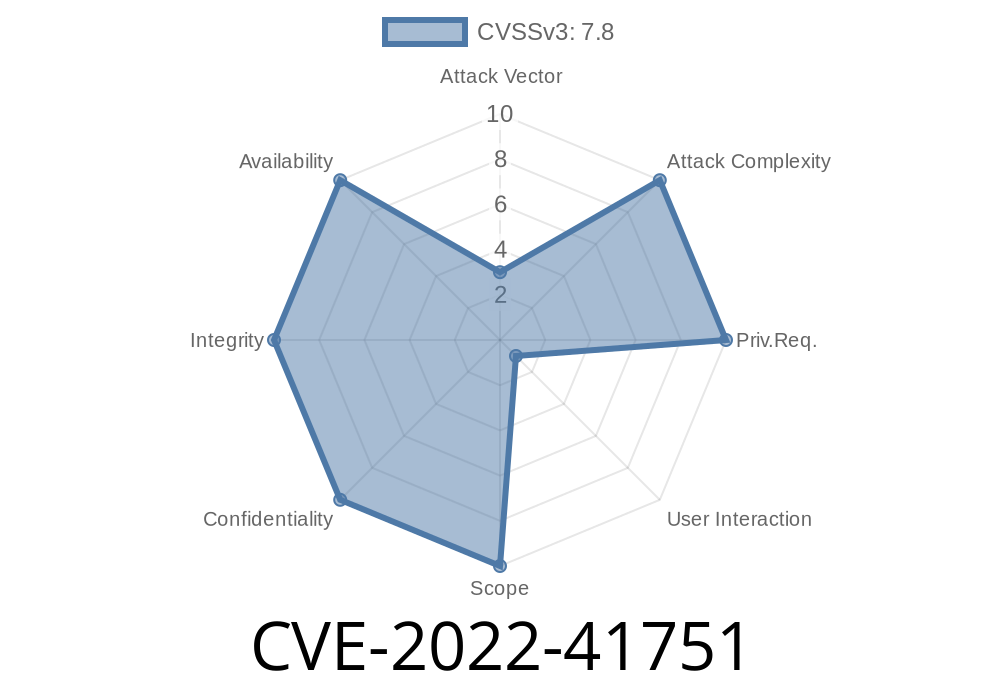
Summary of CVE-2018-1000111
The vulnerability is caused by an error in the Jhead application when parsing a JPEG file.
When parsing a JPEG file, the Jhead application will look for the string "COMMAND: \r
" at the beginning of the file and then execute the following command: /bin/bash -c 'eval "$(echo " $(basename $1)")"' When parsing a JPEG file, the Jhead application will look for the string "" at the beginning of the file and then execute the following command: /bin/bash -c 'eval "$(echo ""')"'
Timeline
Published on: 10/17/2022 18:15:00 UTC
Last modified on: 10/26/2022 20:15:00 UTC
References
- https://github.com/Matthias-Wandel/jhead/blob/63ce118c6a59ea64ac357236a11a47aaf569d622/jhead.c#L788
- https://github.com/Matthias-Wandel/jhead/pull/57
- https://github.com/Matthias-Wandel/jhead
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/TAVB3ZX7E5ULEXESU5NXZIAHY6CVGCHB/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/EG26AD7KJAY5B6L6OERSGL4FRXJE3GOB/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-41751