---
Introduction
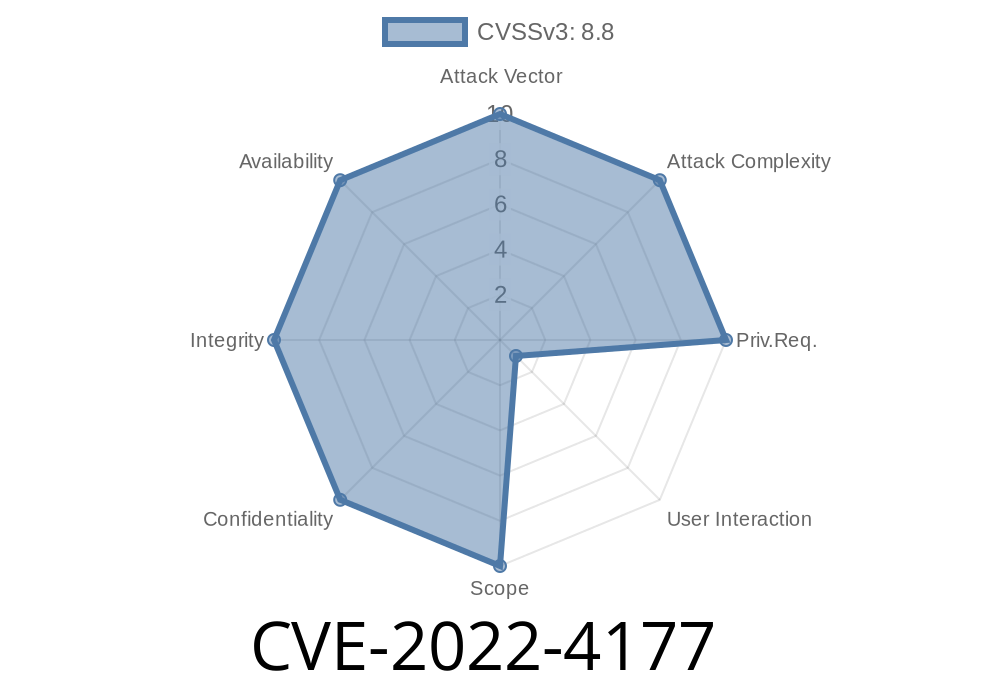
The web browser is a doorway to the internet, and Google Chrome is one of the most popular today. Unfortunately, that makes it an attractive target for hackers. In late 2022, a security flaw was discovered in Chrome’s extension system that could let attackers take over a user’s browser if exploited correctly. This vulnerability—CVE-2022-4177—was categorized as High Severity by the Chromium team and patched in Chrome version 108..5359.71.
In this post, we’ll break down what went wrong, how an attacker might have exploited the bug, check out some code to illustrate the issue, and share how to stay protected.
What is “Use-After-Free”?
“Use-after-free” bugs happen when a program uses memory after it has already given it back, or freed it. Imagine you lease an apartment, hand back the keys, and then someone tries to walk inside—you don't know what’s inside anymore. In code, this can lead to unpredictable behavior or even allow attackers to run malicious code.
Where Did the Bug Occur?
This flaw was found in Chrome's Extensions component specifically in how Chrome handled the lifecycle of extension objects. If an extension was crafted in a tricky way, and the user interacted with the UI (like clicking buttons), the attacker could trigger this memory mismanagement and corrupt Chrome’s heap memory.
Bug type: Use-after-free
- Chromium Issue: Chromium bug 1374923
How Could Attackers Exploit It?
The attacker had to convince you to install a malicious extension. Then, a specific user action in the UI—say, clicking a button or interacting with a popup—would trigger the bug. Malicious code in the extension could make Chrome read or write to memory that was already freed. This break from normal flow could let the attacker execute their own code (“remote code execution”) or crash Chrome.
Here's a simplified (not actual Chrome) example to demonstrate the concept
// C++ Pseudocode
class ExtensionObject {
public:
void doSomething() {
// Data manipulation...
}
};
void onUIClick(ExtensionObject* obj) {
delete obj; // Free memory
obj->doSomething(); // Use after free: BAD!
}
In the above, after deleting obj, calling doSomething() is unsafe: the memory is no longer valid.
Step 1: Create a Malicious Extension
- The attacker writes a Chrome extension that tricks Chrome into freeing an object during a UI action, but then continues to interact with it.
Step 4: Gain Control
- The extension exploits the corrupted memory, potentially allowing arbitrary code execution in the context of the user's browser.
What Makes This Vulnerability Serious?
Heap corruption is unpredictable. Sometimes, it just makes Chrome crash. Other times, skilled attackers can craft their exploits carefully and run their own code on your machine! Chrome extensions run with broad access, so when combined with this vulnerability, the impact can be significant.
References and Further Reading
- Chrome Release Notes (v108..5359.71)
- Chromium Security Advisory for CVE-2022-4177
- Original Chromium Issue #1374923
- Common Vulnerabilities and Exposures (CVE) Details for CVE-2022-4177
- Understanding Use-After-Free Exploits
How Was It Fixed?
The Chromium team patched the extension code to ensure that extension objects couldn't be used after being freed from memory. This fixed the problem and closed the attack window.
How to Stay Safe
- Update Chrome: Always keep your browser up-to-date. The fix has been shipped since version 108..5359.71.
- Be Careful With Extensions: Only install extensions from trusted developers and the official Chrome Web Store.
Conclusion
CVE-2022-4177 is a classic example of how even tiny mistakes in complex software like Chrome's extension system can be leveraged by attackers. If you keep your software updated and are careful with which extensions you install, you’ll be much safer online.
Timeline
Published on: 11/30/2022 00:15:00 UTC
Last modified on: 05/03/2023 12:16:00 UTC