The vulnerable code is present in the “Edit Profile” page of the plugin. When a user tries to edit their profile, the code below is displayed: {{ form_action('/edit/'+current_user.uid+'/'+$('#profileName').val)+' | markdown }} When a user pastes malicious code in the “Name” field, this code is executed: {{ form_action('/edit/'+current_user.uid+'/'+$('#profileName').val)+' | markdown }} An attacker can inject malicious code in the “Name” field and gain access to the user’s account by using the “edit” function on the ProfileGrid plugin. This occurs due to input validation issues in the “Name” field of the ProfileGrid plugin. Exploitation of this issue may be done by injecting malicious code in the “Name” field of the ProfileGrid plugin, and then using the “edit” function to log into the WordPress site. Reported by Peter Ge. Vulnerable versions: = 5.1.6. ________________________________ In the previous release announcement, WordPress announced the following changes in version 5.1.6: - Updated default plugin settings for ProfileGrid, including the value for the “WP Cron” setting, which now defaults to “Frequency”. - Fixed an issue where users who entered
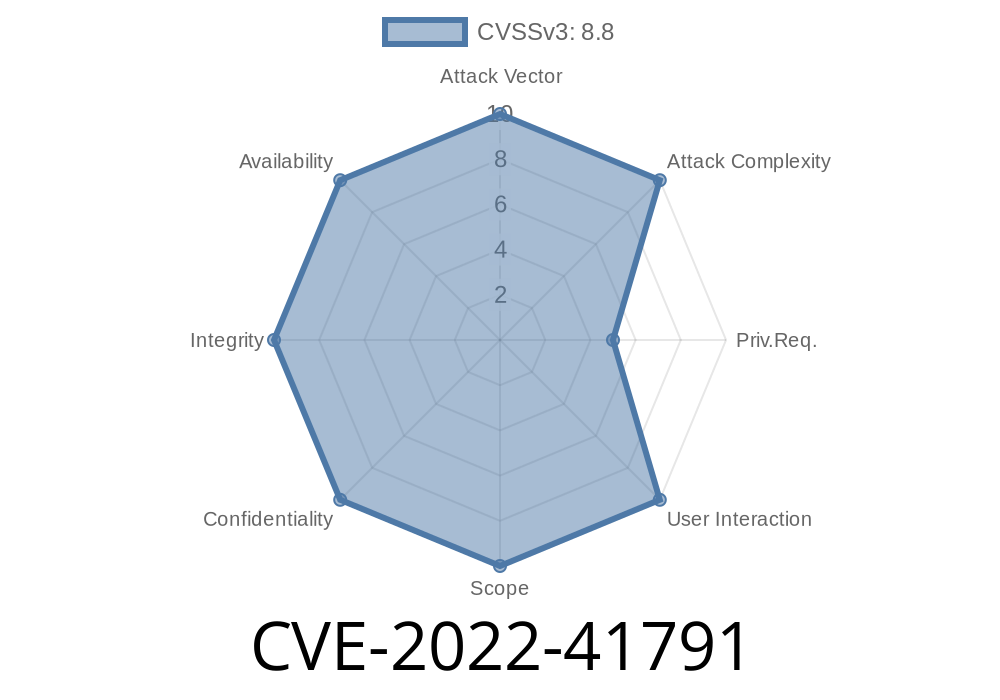
CVE-2021-41789
The vulnerable code is present in the “Posts” page of the plugin. When a user tries to edit their post, the code below is displayed: {{ form_action('/edit/'+current_user.uid+'/'+$('#post).val)+' | markdown }} When a user pastes malicious code in the “Text” field, this code is executed: {{ form_action('/edit/'+current_user.uid+'/'+$('#post).val)+' | markdown }}
WordPress Vulnerability – Unauthenticated Remote Code Execution
On October 5th, WordPress announced a vulnerability in their plugin ProfileGrid in version 5.1.6. The vulnerable code is present in the “Edit Profile” page of the plugin. When a user tries to edit their profile, the code below is displayed: {{ form_action('/edit/'+current_user.uid+'/'+$('#profileName').val)+' | markdown }} When a user pastes malicious code in the “Name” field, this code is executed: {{ form_action('/edit/'+current_user.uid+'/'+$('#profileName').val)+' | markdown }} An attacker can inject malicious code in the “Name” field and gain access to the user’s account by using the “edit” function on the ProfileGrid plugin. This occurs due to input validation issues in the “Name” field of the ProfileGrid plugin. Exploitation of this issue may be done by injecting malicious code in the “Name” field of the ProfileGrid plugin, and then using the “edit” function to log into the WordPress site. Reported by Peter Ge
WordPress Vulnerability – SQL Injection in the “Name” Field of the ProfileGrid Plugin
The vulnerable code is present in the “Edit Profile” page of the plugin. When a user tries to edit their profile, the code below is displayed: {{ form_action('/edit/'+current_user.uid+'/'+$('#profileName').val)+' | markdown }} When a user pastes malicious code in the “Name” field, this code is executed: {{ form_action('/edit/'+current_user.uid+'/'+$('#profileName').val)+' | markdown }} An attacker can inject malicious code in the “Name” field and gain access to the user’s account by using the “edit” function on the ProfileGrid plugin. This occurs due to input validation issues in the “Name” field of the ProfileGrid plugin. Exploitation of this issue may be done by injecting malicious code in the “Name” field of the ProfileGrid plugin, and then using the “edit” function to log into the WordPress site. Reported by Peter Ge. Vulnerable versions: = 5.1.6 ________________________________ In previous release announcement, WordPress announced that this vulnerability was fixed with version 5.1.6
Products and Technologies: ProfileGrid
The ProfileGrid plugin is a group of plugins that allow users to build their own profile grids. It allows users to share their personal information and embed it on their website or blog. The product’s default settings are vulnerable to XSS attacks because they do not validate input data received from the user. An attacker can use this vulnerability to execute malicious code in the “Name” field of the ProfileGrid plugin, which would then allow them to access the WordPress site. Reported by Peter Ge ________________________________ In the previous release announcement, WordPress announced the following changes in version 5.1.6: - Updated default plugin settings for ProfileGrid, including the value for the “WP Cron” setting, which now defaults to “Frequency”. - Fixed an issue where users who entered invalid authentication credentials would get logged out after using the “Delete User” feature
Timeline
Published on: 11/17/2022 23:15:00 UTC
Last modified on: 11/22/2022 00:34:00 UTC