While running in VE, an attacker may be able to access iControl REST endpoints with an unauthenticated user, bypassing VE restrictions. Exploits of VE, like these in BIG-IP, have been published, allowing user privilege escalation. While running in iControl REST VE, an attacker may be able to access iControl REST endpoints with an unauthenticated user, bypassing VE restrictions. Exploits of VE, like these in BIG-IP, have been published, allowing user privilege escalation. RESET BIG-IP Configuration in VE Users can access the RESET BIG-IP Configuration REST endpoint, with an unauthenticated user, bypassing VE restrictions. Exploits of VE, like these in BIG-IP, have been published, allowing user privilege escalation. While running in iControl REST VE, an attacker may be able to access iControl REST endpoints with an unauthenticated user, bypassing VE restrictions. Exploits of VE, like these in BIG-IP, have been published, allowing user privilege escalation. While running in iControl REST VE, an attacker may be able to access iControl REST endpoints with an unauthenticated user, bypassing VE restrictions. Exploits of VE, like these in BIG-IP, have been published, allowing user privilege escalation. While running in iControl REST VE, an attacker may be able to access i
iControl REST VE Configuration Vulnerabilities
The iControl REST VE Configuration endpoint is an end point that allows users to access configuration and other settings for BIG-IP. In BIG-IP, this endpoint can be exploited by malicious actors using the REST API to get past VE restrictions and gain unauthorized access to configuration settings. When the user account is not authenticated, they are able to bypass VE restrictions without going through authentication checks. The attacker may then configure systems with elevated privileges if they have sufficient permissions granted via the vulnerability.
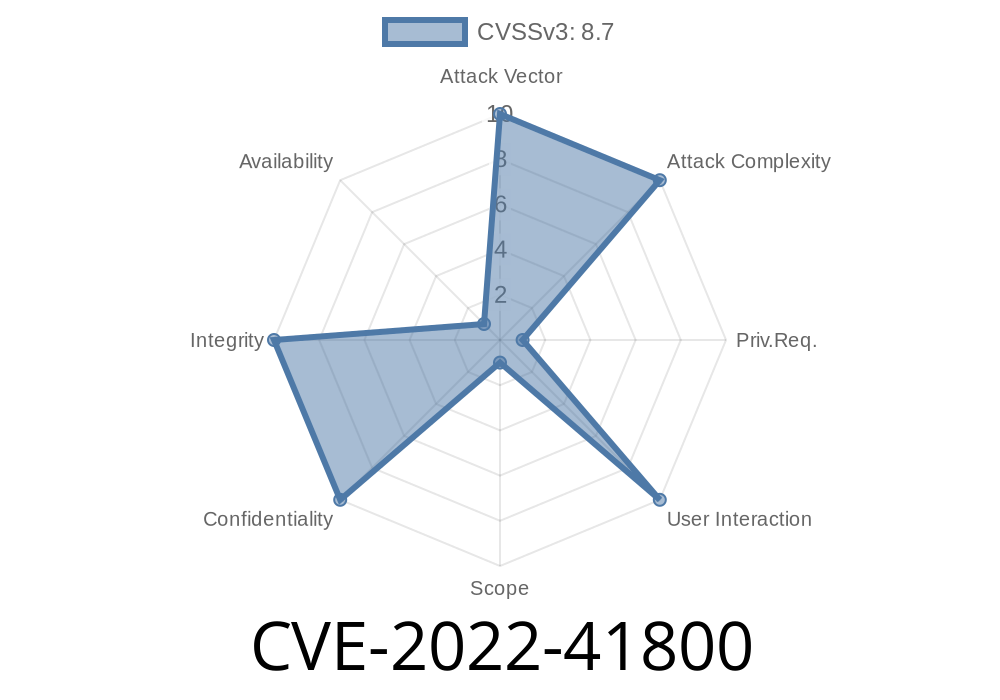
Vulnerability Summary
A vulnerability in the BIG-IP system has been discovered that allows an unauthenticated user to access iControl REST endpoints with an unauthenticated user, bypassing VE restrictions. Exploits of VE, like these in BIG-IP, have been published, allowing user privilege escalation.
Exploits of BIG-IP
, like these in iControl REST
Exploits of BIG-IP, like these in iControl REST, have been published, allowing user privilege escalation.
Timeline
Published on: 12/07/2022 04:15:00 UTC
Last modified on: 12/12/2022 15:25:00 UTC