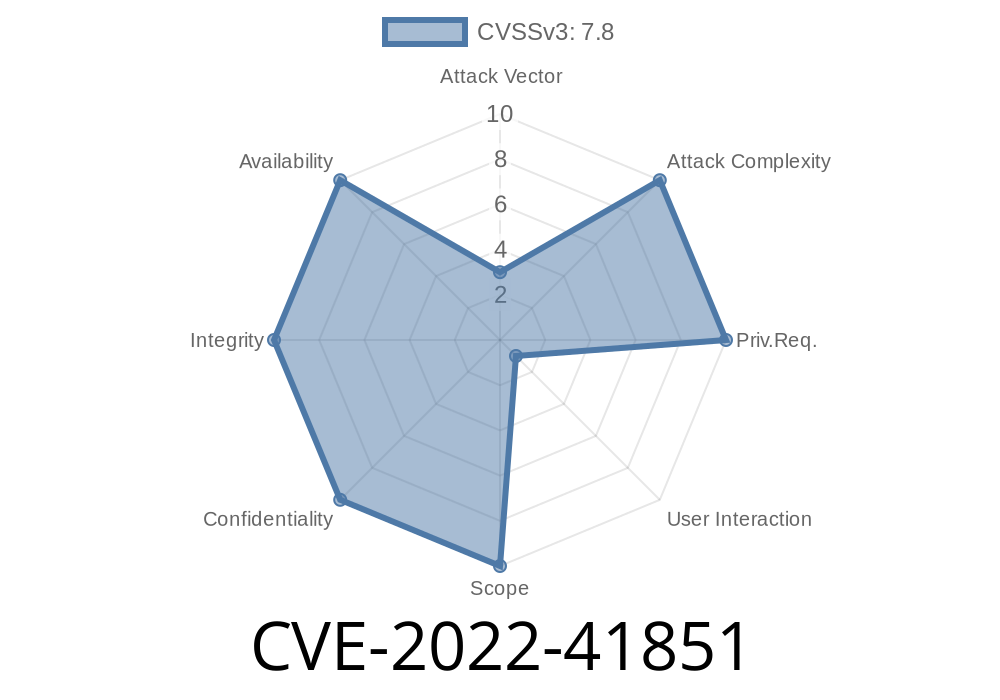
An information disclosure vulnerability has been identified in the Simcenter Femap V2022.1 (All versions V2022.1.3) software. This vulnerability could be exploited by an attacker to Bypass authentication and access sensitive information on the targeted system. (ZDI-CAN-17412) An information disclosure vulnerability has been identified in the Simcenter Femap V2022.2 (All versions V2022.2.2) software. This vulnerability could be exploited by an attacker to Bypass authentication and view sensitive information on the targeted system. (ZDI-CAN-17413) A denial of service vulnerability has been identified in the Simcenter Femap V2022.1 (All versions V2022.1.3) software. This vulnerability could be exploited by an attacker to cause a denial of service condition. (ZDI-CAN-17418) An information disclosure vulnerability has been identified in the Simcenter Femap V2022.2 (All versions V2022.2.2) software. This vulnerability could be exploited by an attacker to view sensitive information on the targeted system. (ZDI-CAN-17419) A vulnerability in the JTTK library has been identified in the Simcenter Femap V2022.1 (All versions V2022.1.3) software. The JTTK library is vulnerable to an uninitialized pointer reference vulnerability while parsing specially crafted JT files. An attacker
Vulnerability overview
A vulnerability has been identified in the Simcenter Femap V2022 software. This vulnerability could be exploited by an attacker to bypass authentication and access sensitive information on the targeted system. An information disclosure vulnerability has been identified in the Simcenter Femap V2022 software. This vulnerability could be exploited by an attacker to view sensitive information on the targeted system. A denial of service vulnerability has been identified in the Simcenter Femap V2022 software. This vulnerability could be exploited by an attacker to cause a denial of service condition. An information disclosure vulnerability has been identified in the Simcenter Femap V2022 software. This vulnerability could be exploited by an attacker to view sensitive information on the targeted system.
Timeline
Published on: 10/11/2022 11:15:00 UTC
Last modified on: 10/12/2022 14:30:00 UTC