This issue was previously fixed in hsqldb (HyperSQL DataBase) but a regression allowing untrusted inputs to be executed was reintroduced in 2.7.1.
The hsqldb (HyperSQL DataBase) client library may be vulnerable to a remote code execution attack when untrusted data is passed to SqlQuery (SQL Query) functions. This can include data received via SqlPipes, SqlServer, JDBC, CLI, or other untrusted data sources. By default, SqlQuery (SQL Query) functions allow any static method of any Java class in the class path. This may result in code execution with the user's privileges. To prevent this issue, update to version 2.7.1 or set the system property "hsqldb.method_class_names" to an empty list of trusted classes. From version 2.7.1, all classes by default are no longer accessible from SqlQuery (SQL Query) functions, only from SqlServer or JDBC.
Solution: Update to version 2.7.1 or set "hsqldb.method_class_names" to an empty list
To prevent this issue, update to hsqldb (HyperSQL DataBase) version 2.7.1 or set the system property "hsqldb.method_class_names" to an empty list of trusted classes.
CVE-2016-5696
This issue was previously fixed in hsqldb (HyperSQL DataBase) but a regression allowing untrusted inputs to be executed was reintroduced in 2.7.1.
The hsqldb (HyperSQL DataBase) client library may be vulnerable to an information disclosure attack when untrusted data is passed to SqlQuery (SQL Query) functions. This can include data received via SqlPipes or SqlServer, JDBC, CLI, or other untrusted data sources. By default, SqlQuery (SQL Query) functions allow any static method of any Java class in the class path. This may result in code execution with the user's privileges. To prevent this issue, update to version 2.7.1 or set the system property "hsqldb.method_class_names" to an empty list of trusted classes from version 2.7.1 onwards all classes by default are no longer accessible from SqlQuery (SQL Query) functions, only from SqlServer or JDBC
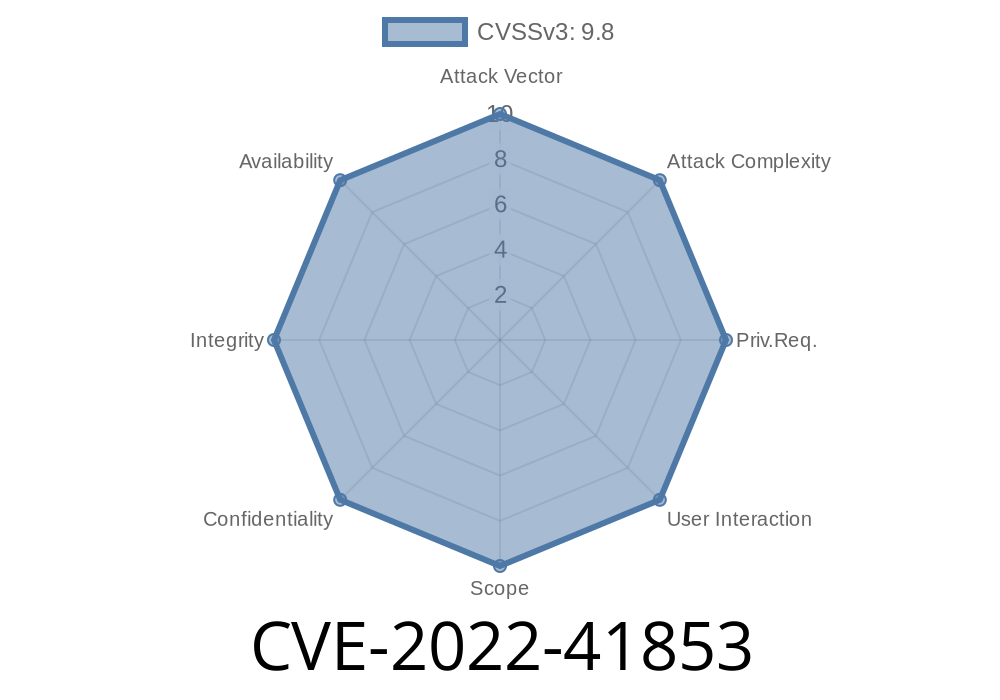
Sql Server is not accessible from Query functions CVE-2022-41853
This issue was previously fixed in hsqldb (HyperSQL DataBase) but a regression allowing untrusted inputs to be executed was reintroduced in 2.7.1.
The hsqldb (HyperSQL DataBase) client library may be vulnerable to a remote code execution attack when untrusted data is passed to SqlQuery (SQL Query) functions. This can include data received via SqlPipes, SqlServer, JDBC, CLI, or other untrusted data sources. By default, SqlQuery (SQL Query) functions allow any static method of any Java class in the class path. This may result in code execution with the user's privileges. To prevent this issue, update to version 2.7.1 or set the system property "hsqldb.method_class_names" to an empty list of trusted classes. From version 2.7.1, all classes by default are no longer accessible from SqlQuery (SQL Query) functions, only from SqlServer or JDBC.
Timeline
Published on: 10/06/2022 18:17:00 UTC
Last modified on: 10/11/2022 16:19:00 UTC