With the update, an attacker can no longer exploit the vulnerability by sending specially crafted JSON messages. Optica users are advised to update the software immediately. Pivotal recommends using the following update mechanism: Through the web interface: https://www.pivotal.io/jira
Through the command-line interface: $ curl -X PATCH https://www.pivotal.io/jira/patch -o /dev/stdout $ dc pv:optica-server-{VERSION} -p {PIVOTAL_PASSWORD} When upgrading through the command-line interface, the server must be restarted for the upgrade to take effect. Optica users are advised to upgrade to the latest version as soon as possible.
Intrusion Detection
The latest Optica release includes a new mechanism for detecting an intrusion. Optica now contains a new plugin that can be configured to trigger on the following events:
- The user connects to the application after the first connection and before login.
- A new cookie is set from a domain other than optica.io or optica-pivotal.com
- A newly loaded page contains data that does not match its previous content
Visit the website for further information
Visit the website for further information.
https://www.pivotal.io/optica/security-updates
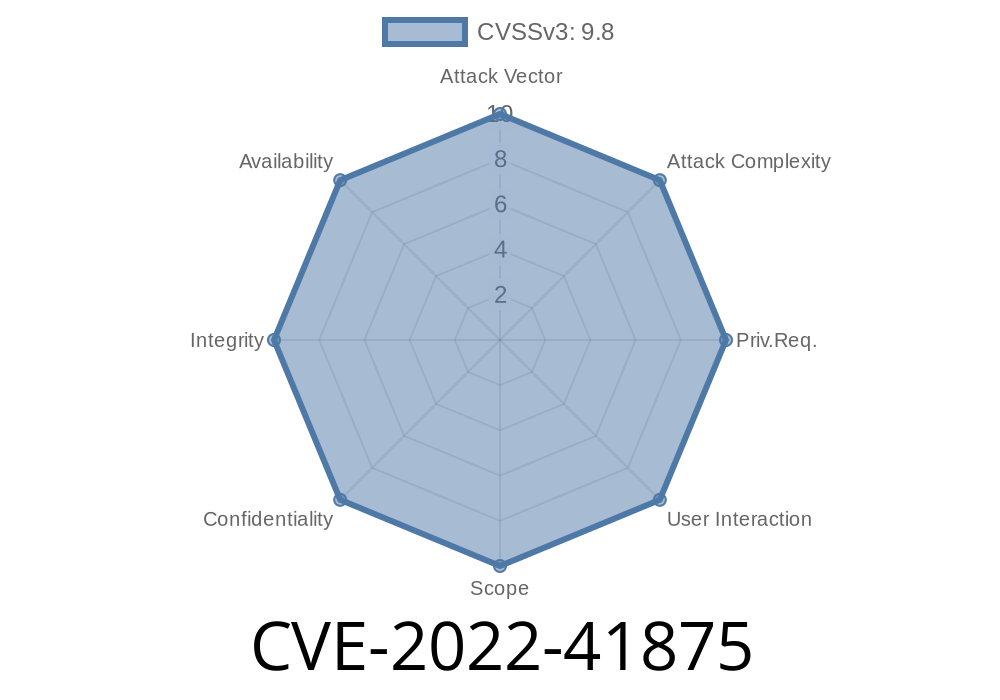
Optica Vulnerability Summary
A vulnerability has been discovered in Optica, a library for communicating with Apache Kafka. The vulnerability was introduced in version 2.9.0, and allows an attacker to exploit the JSON parser of Optica to tamper with any user's messages sent to Apache Kafka.
Optica users are advised to update their software immediately.
Timeline
Published on: 11/23/2022 19:15:00 UTC
Last modified on: 11/30/2022 16:07:00 UTC