When installing Parse Server, you can prevent certain types of pollution by setting an option on the parse.server object. This option is called `requestKeywordDenylist` and it can be set to `false` to allow the use of `undeclaredKeywords`. However, this option has a flaw where if you have a sensitive keyword in your app, it can be blocked when it is either not declared or declared as an undeclared keyword. This can be mitigated by setting the requestKeywordDenylist to `false` by adding `parse.server.set(`requestKeywordDenylist, false`)` to your app. When setting this option to `true`, an attacker can bypass the pollution feature by deploying a malicious payload that has a keyword that the app is looking for. So by setting the requestKeywordDenylist option to `false`, it makes it so that any keyword in the app that is not declared ends up being blocked by Parse Server as it is not allowed by the requestKeywordDenylist option.
Summary
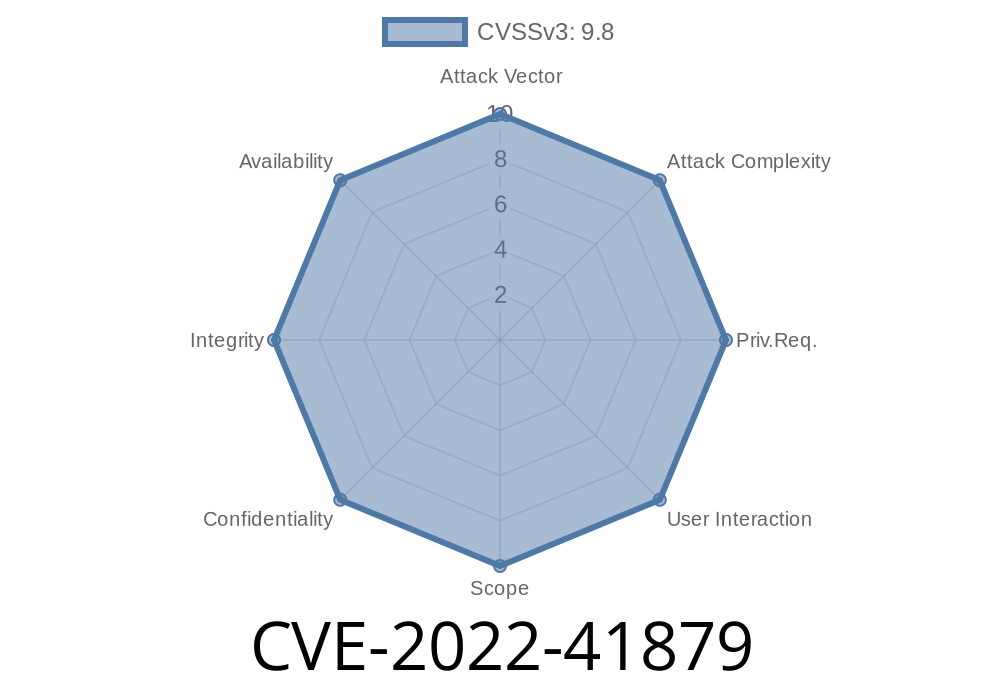
This vulnerability allows an attacker to bypass the pollution feature of Parse Server by deploying a malicious payload that has a keyword that the app is looking for. This vulnerability can be mitigated by setting the requestKeywordDenylist option to `false`.
Vulnerability Details
Attackers can exploit this vulnerability by issuing a request to the Parse Server with a payload that contains a sensitive keyword. The server will block that request because of the `requestKeywordDenylist` option. However, if the attacker is able to deploy a malicious payload with that sensitive keyword in it, then it will bypass the server's decision and continue on its path.
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
Timeline
Published on: 11/10/2022 21:15:00 UTC
Last modified on: 11/15/2022 19:50:00 UTC