Arches is a popular open-source web platform used by researchers, governments, and heritage organizations to create, manage, and visualize geospatial data—think important digital maps and data about historic buildings or archaeological sites.
For everyone who uses Arches, *there’s something you need to know*: if you're running certain older versions, your data may be at serious risk because of a known SQL Injection vulnerability CVE-2022-41892. Here, I’ll break down what this vulnerability is, how it can be exploited, and what you need to do to keep your system safe.
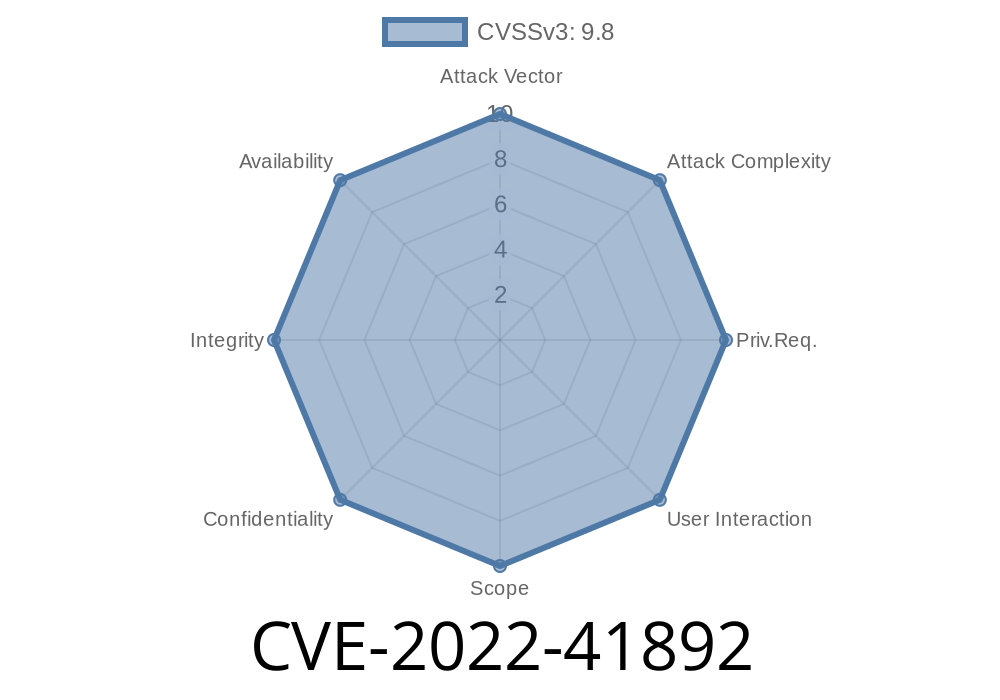
What is CVE-2022-41892?
CVE-2022-41892 is a SQL Injection vulnerability found in Arches versions before 6.1.2, 6.2.1, and 7.1.2. Specifically, attackers can inject malicious SQL queries via specially crafted web requests. This means a remote, unauthenticated attacker could manipulate or read sensitive data in your Arches database.
7.1.2 and above
There are currently no official workarounds aside from upgrading.
How Does the Exploit Work?
An attacker sends a specially crafted request to the Arches web server, targeting a vulnerable endpoint. If your instance isn’t patched, the system passes attacker-controlled input directly to a SQL query—a classic and dangerous mistake.
Example Attack Flow
1. The attacker identifies your Arches endpoint (like /resources/search).
Example Exploit Code Snippet
Let’s say the vulnerable endpoint was expecting a resource search query parameter. (Note: This is a generic illustration for educational purposes only!)
Suppose the API expected
GET /resources/search?q=old%20bridge
The server-side code (pseudo-Python) might look like
# BAD: Vulnerable to SQL Injection!
def search_resources(request):
q = request.GET.get('q')
cursor.execute(f"SELECT * FROM resources WHERE name LIKE '%{q}%'")
results = cursor.fetchall()
return results
An attacker could craft a request like
GET /resources/search?q=bridge'%20OR%201=1--
This would modify the query to
SELECT * FROM resources WHERE name LIKE '%bridge' OR 1=1--%'
This OR 1=1 always evaluates true, so the attacker can dump the entire resources table or pull additional data.
Curl Example of Exploitation
curl "https://target-arches.com/resources/search?q='; OR 1=1--"
That request can force the backend to perform actions it should never do.
What Damage Could Happen?
- Data theft: Attackers could extract sensitive map data, user information, or confidential research.
Data tampering: Attackers could alter, corrupt, or delete existing records.
- Potential remote code execution: Advanced attackers might chain this vulnerability to gain deeper access.
Timeline and References
- Advisory Published: https://github.com/archesproject/arches/security/advisories/GHSA-p5g8-ff65-ww2r
- See NVD Listing: https://nvd.nist.gov/vuln/detail/CVE-2022-41892
- Patch Commit: https://github.com/archesproject/arches/commit/71fb3972c7fd8c6f98e1e9a384ec387d7e899471
No Workaround, Only One Solution: Upgrade ASAP
There are no mitigations, no workaround, and no quick fixes—if you’re running a vulnerable version, you must upgrade right now:
TL;DR
- CVE-2022-41892 is a dangerous SQL Injection in Arches (prior to 6.1.2/6.2.1/7.1.2)
Original References
- GitHub Security Advisory for CVE-2022-41892
- NVD: CVE-2022-41892
- Arches Project Repository
Final Advice
Don’t wait: check your Arches version today, and patch if needed. The risk is real—SQL Injection is one of the most serious vulnerabilities for any database-driven web service.
If you need help or have questions, head over to the Arches Project Community.
Timeline
Published on: 11/11/2022 04:15:00 UTC
Last modified on: 11/16/2022 02:35:00 UTC