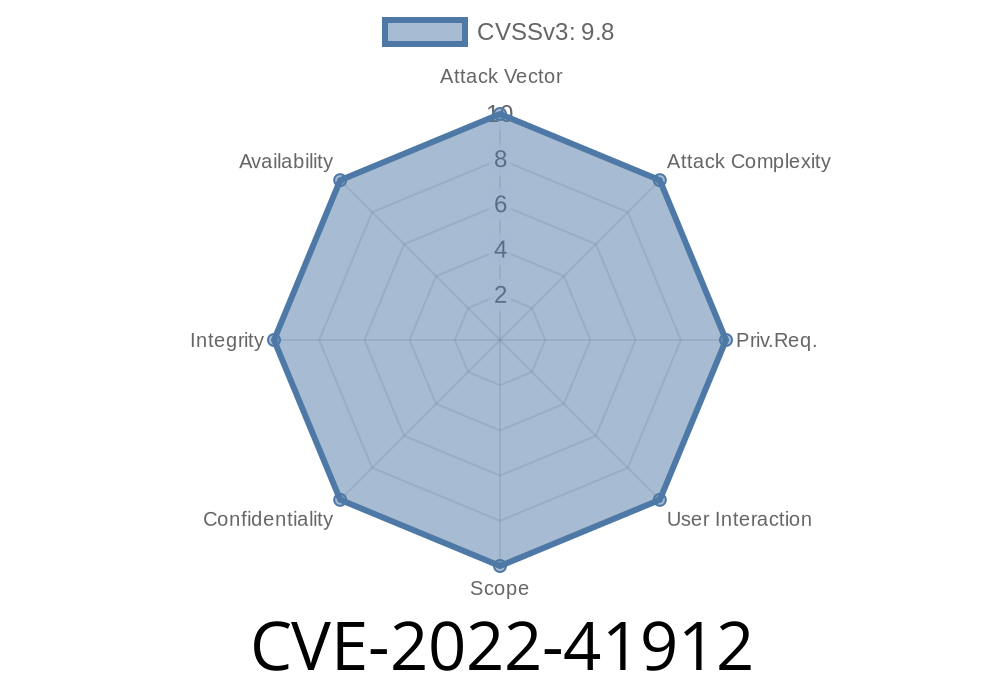
If your application is using crewjam/saml, you should upgrade to the latest version as soon as possible.
Crewjam/saml versions prior to 0.4.9 are vulnerable to an cross-site scripting (XSS) attack when handling SAML authentication responses. This issue has been corrected in crewjam/saml 0.4.9. There are no workarounds other than upgrading to a fixed version.
Crewjam/saml versions prior to 0.3.0 are vulnerable to an XSS attack when handling SAML authentication responses. This issue has been corrected in crewjam/saml 0.3.0. There are no workarounds other than upgrading to a fixed version.
Crewjam/saml versions prior to 0.2.5 is vulnerable to an XSS attack when handling SAML authentication responses. This issue has been corrected in crewjam/saml 0.2.7. There are no workarounds other than upgrading to a fixed version.
Crewjam/saml versions prior to 0.2.3 is vulnerable to an XSS attack when handling SAML authentication responses. This issue has been corrected in crewjam/saml 0.2.5. There are no workarounds other than upgrading to a fixed version.
Crewjam/saml versions prior to 0.1.0 is vulnerable to an XSS attack when handling SAML authentication responses. This issue
Crewjam/saml version 0.4.9
Crewjam/saml versions prior to 0.4.9 are vulnerable to an cross-site scripting (XSS) attack when handling SAML authentication responses. This issue has been corrected in crewjam/saml 0.4.9. There are no workarounds other than upgrading to a fixed version as soon as possible.
Crewjam/saml technical details
Crewjam/saml uses OpenID Connect as the authentication provider for SAML.
For more information about the vulnerability, see https://github.com/crewjam/saml-saas-new-security-update
Timeline
Published on: 11/28/2022 15:15:00 UTC
Last modified on: 12/01/2022 20:20:00 UTC