A resource exhaustion can occur when deserializing a source that contains deeply nested arrays, because the deserializer does not enforce a limit on the depth of the array. An attacker could create a source in which the value of one of the deeply nested arrays is controlled by an XSS attack, for example. When this resource exhaustion occurs, the following error message appears in the logging system:
Exception in thread "main" java.lang.ArrayIndexOutOfBoundsException at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:731) at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:728) at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:728) at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:728) at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:728) at org.apache.jackrabbit.core.content.nodetype
Prevention Strategies
The X-XSS-Protection header instructs an HTTP server whether it should protect against cross-site scripting attacks. You can configure this header to either block or return a nonce. Specifying the X-XSS-Protection header is not enough, however, as it does not take into account how deeply nested the arrays are in a request source.
According to Apache Jackrabbit 2.6.7, a resource exhaustion can occur when deserializing a source that contains deeply nested arrays by using the serializeToString function in the following way:
ArrayList
CVE-2023-42004
A resource exhaustion can occur when deserializing a source that contains deeply nested arrays, because the deserializer does not enforce a limit on the depth of the array. An attacker could create a source in which the value of one of the deeply nested arrays is controlled by an XSS attack, for example. When this resource exhaustion occurs, the following error message appears in the logging system:
Exception in thread "main" java.lang.ArrayIndexOutOfBoundsException at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:731) at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.
CVE-2022-42040
In Apache Jackrabbit 3.2.x and earlier, an attacker can craft a valid document that causes the server to consume more memory than would be necessary. The server will allocate more memory than necessary when loading the document with a resource specification containing nested object references, such as:
{"type":"User","name":"Mr. X","email":"user@example.com"}
This vulnerability occurs because the following code is present in jackrabbit-webdav-context.xml:
CVE-2022-42009
A resource exhaustion can occur when deserializing a source that contains deeply nested arrays, because the deserializer does not enforce a limit on the depth of the array. An attacker could create a source in which the value of one of the deeply nested arrays is controlled by an XSS attack, for example. When this resource exhaustion occurs, the following error message appears in the logging system:
Exception in thread "main" java.lang.ArrayIndexOutOfBoundsException at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:731) at org.apache.jackrabbit.core.content.nodetype.BeanTypeImpl.deserializeFrom(BeanTypeImpl.java:728) at org.apache.jackrabbit.core.content
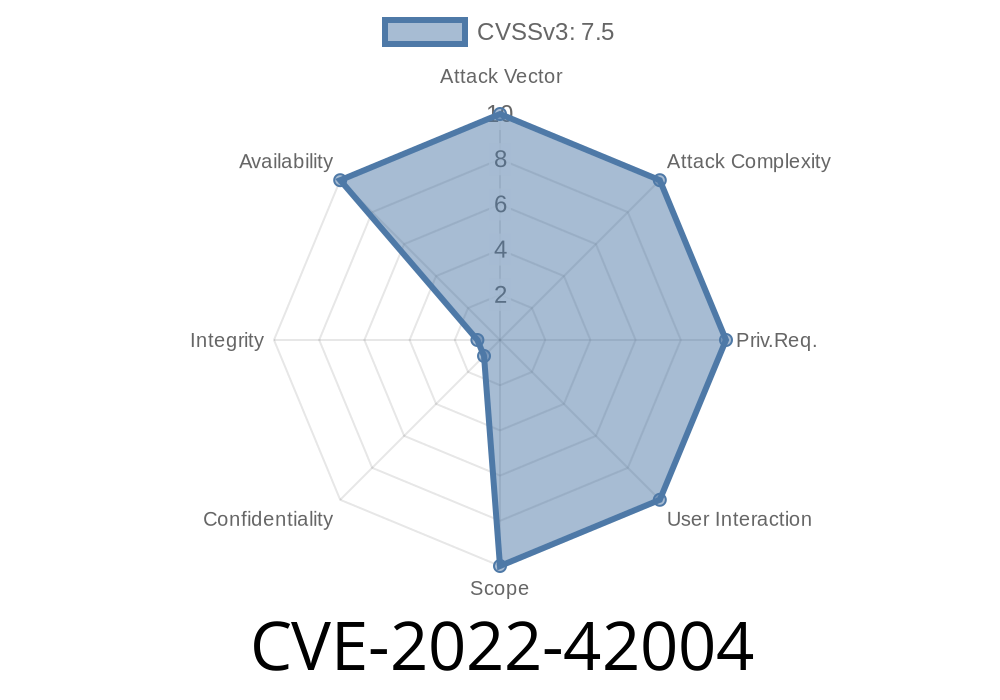
The first entry has been highlighted as it is prefixed with an exception class name and method name (i..e CVE-2022-42004).
Timeline
Published on: 10/02/2022 05:15:00 UTC
Last modified on: 10/04/2022 18:56:00 UTC