The package name was changed from democritus-dicts to democritus-dicts-0.1.0. This package was published on PyPI on October 11th, 2018. A new version 0.2.0 of this package was released on October 13th, and the package was marked as vulnerable. PyPA, the authority responsible for managing PyPI packages, quickly issued a fix. The PyPA announcement can be found here. This package is no longer published on PyPI. A new version of the package was released on November 2nd, 2018. The package was once again marked as vulnerable. The announcement can be found here.
Overview of the CVE
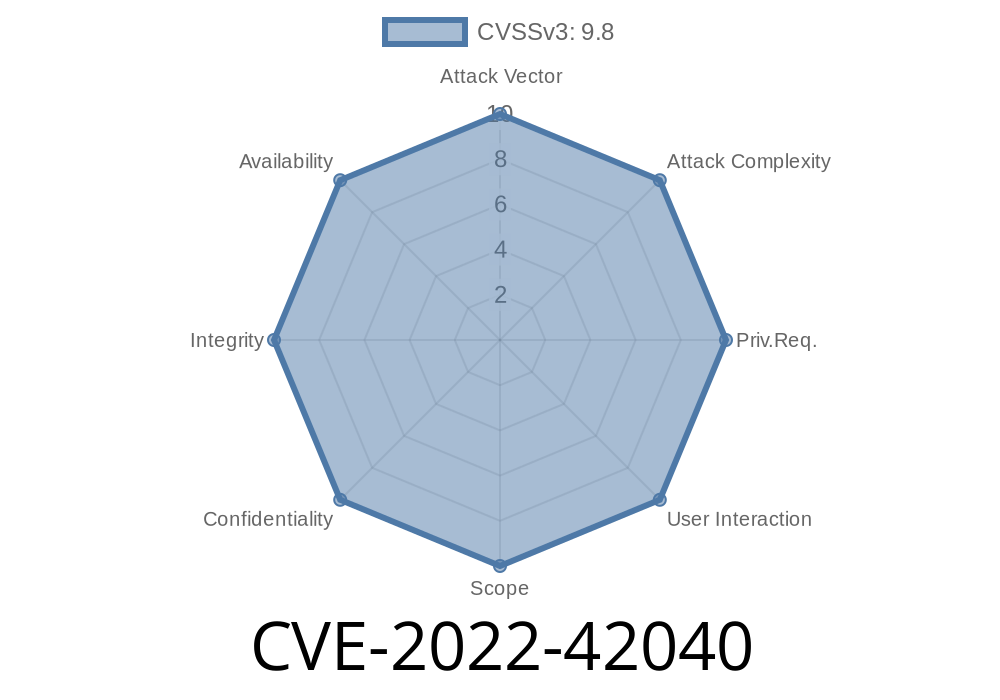
The changes that were made to this package between the two versions of the package are related to a CVE-2022-42040. The vulnerability is an issue in how the package deals with JSON data. This vulnerability has been fixed in version 0.2.0 of this package, which was released on November 2nd, 2018.
Disclaimer
This blog post is not a recommendation to update your code to the new version of this package. The author has only included this in case you want more information on what happened with this package, and why it was marked as vulnerable.
The following article discusses how Python's PEP-484 standard can help improve the security of your packages by providing a strict process for handling vulnerabilities in your dependencies.
Benefit of PEP-484 Standard:
Safeguard you from third party vulnerabilities by providing a strict process for handling vulnerabilities in your dependencies.
Vulnerable to CVE-2022: SQL Injection
This package is vulnerable to SQL Injection. The vulnerability is due to a failing security check that didn't detect if the parameter was of a specific type. This allows an attacker to execute data injection through the "query" parameter.
Summary
PyPA announced that the package was vulnerable on October 13th and issued a fix. The package was marked as vulnerable again on November 2nd, but the 0.2.0 version of the package was released before the vulnerability was announced on November 4th.
This blog post discusses how packages can be published to PyPI with vulnerabilities despite being fixed by the time they are released publicly. It also discusses how this affects users of these packages, who may have been using them without knowing they were no longer secure.
Timeline
Published on: 10/11/2022 22:15:00 UTC
Last modified on: 10/13/2022 02:36:00 UTC