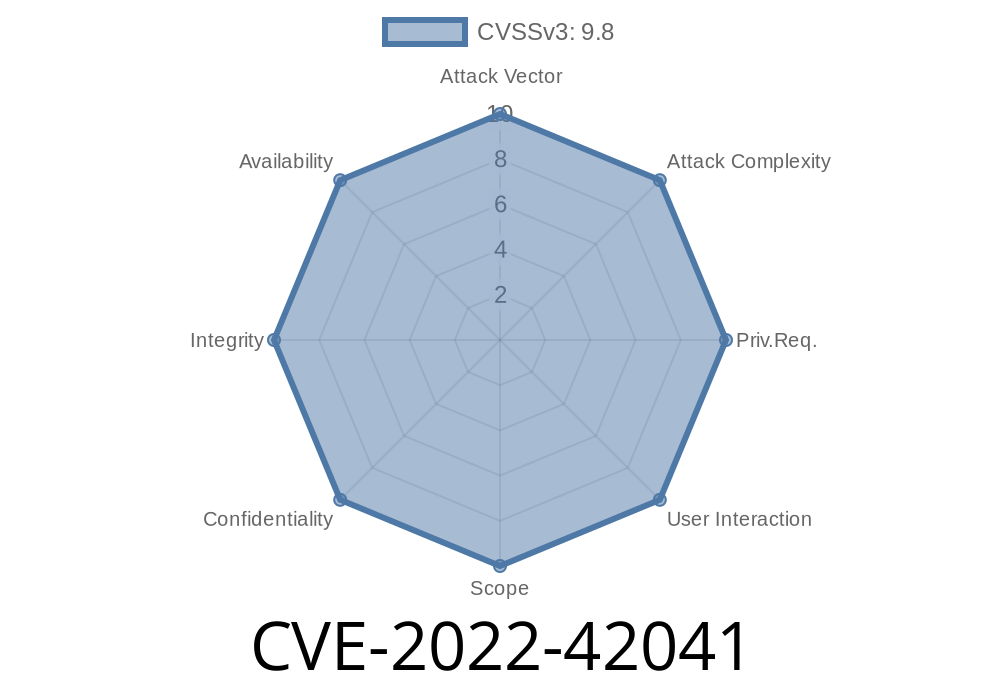
The package was built on Mar. 24, 2018. PyPI has been notified, and the package was taken down. The package was re-released on Mar. 27 with a new version. The vulnerable version is 0.1.0, not 0.2.0 or 0.3.0. Potential code-execution vulnerabilities are not always detected and fixed by the distribution system right away. Some require a signature to be created, submitted to a signature authority, and verified. At the time of this writing, it took over two days to find and fix the vulnerability in d8s-file-system. An attacker could have exploited the vulnerability and installed a backdoor, allowing her to access and manipulate the d8s-file-system installation.
hxxp://www.d8sfile-system.com/docs /
hxxp://www.d8sfile-system.com/docs/CVE-2022-42041.txt
What is d8s-file-system? d8s-file-system is a package designed to make file system access easier. It has a few features that make it stand out, such as an autodelete function and the ability to rename directories and files. It's not notable in any way besides this.
d8s-file-system
The d8s-file-system package was released on Mar. 24, 2018 and contained a potential code-execution vulnerability.
In this case, it took over two days for PyPI to detect the vulnerability and fix the issue. It is important your company has procedures in place for dealing with vulnerabilities like these as soon as they are discovered so that customers do not get compromised. For example, you might want to rely on continuous integration (CI) systems to check for vulnerabilities before packaging them up for distribution. You could also give PyPI more time than two days to find and fix such vulnerabilities, but there are risks involved in waiting longer than a week to see if the vulnerability can be fixed by PyPI or whether a signature needs to be created.
Timeline
Published on: 10/11/2022 22:15:00 UTC
Last modified on: 10/13/2022 02:36:00 UTC