CSRF is a type of attack where an attacker tricks a website into executing unwanted actions on the user's behalf. This can be anything from changing a password to executing arbitrary SQL queries. You can prevent these types of attacks by implementing a few best practices. First, do not allow users to login directly. Instead, give them their own profile which can then be assigned to a role that requires authentication.
Another important best practice is to have a ' lockout ' option for your users. What this does is prevent them from authenticating to the system if they are in the process of attempting to exploit the CSRF vulnerability.
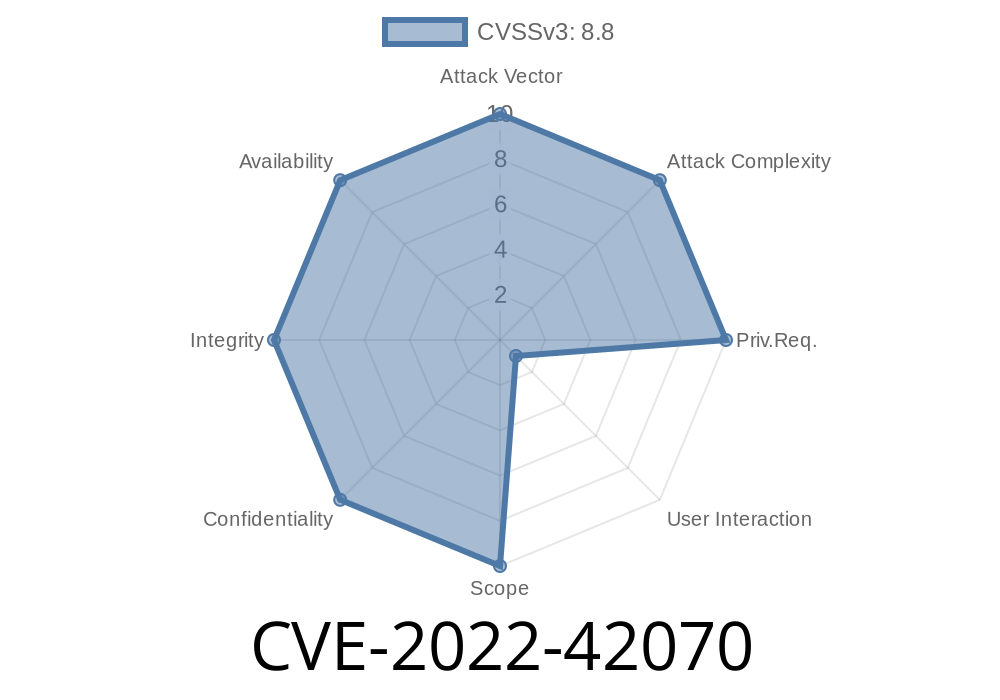
Prevent Cross-Site Request Forgery (CSRF)
The most obvious way to protect your website against CSRF attacks is to make sure your code stays out of the user's session. It's best practice to keep all sensitive data in a cookie or password-protected field, never including it in the markup. When you do this, you should also encode any sensitive data that is passed from the server to the client with a non-standard character set like Base64 .
If this technique doesn't work for your app, you may want to consider using HTTP response splitting or content encoding for CSRF protection. There are other techniques that can help too, such as using "remember me" features on your site and using secure cookies for authentication.
Another important step is implementing a " lockout " option for users who have attempted a CSRF attack. This ensures that if they are logged into the system and doing something nefarious, they will not be able to authenticate further.
How to prevent Cross Site Request Forgery attacks
This is true for all websites that are vulnerable to CSRF attacks.
To prevent these types of attacks, the first thing you should do is use a " role-based authentication " system. This allows you to assign different roles to users, and then only allow certain actions to be performed by those in that role. You should also implement a lockout option for your users. A good way to do this is through the use of Javascript. In order to take advantage of this technique, you need a third party application such as twitter bootstrap or jquery-cookie-jar installed on your site. These can come in handy when you have numerous pages on your site with user profiles and have a lot of them in one cookie which needs to be updated accordingly.
The last recommendation is to make sure that you are using HTTPS . When users are connected over HTTPS , it's harder for attackers because they need an SSL certificate (you can buy one from Amazon) and the browser will not allow for unauthorized certificates unless it's been activated by the user themselves or someone with administrator privileges has done so. When choosing between HTTP and HTTPS , remember that if some part of your website requires authentication, then there's no reason why you shouldn't go with HTTPS as it offers more security than HTTP does
How Does CSRF Work?
When a user authenticates to your site with a CSRF vulnerability, the attacker can send them a malicious link which then triggers an action that does not actually require authentication. For example, if the attacker wants to change their password, they would send them a link which when clicked by the victim changes their password. This attack is often done by exploiting social features on websites like Facebook and Twitter.
Prevention
By following these steps, you can prevent CSRF attacks.
1) Ensure that a 'Lockout' option is included in your system.
2) Do not allow users to login directly. Instead, give them their own profile which can then be assigned to a role that requires authentication.
Timeline
Published on: 10/14/2022 15:16:00 UTC
Last modified on: 10/17/2022 17:59:00 UTC