An attacker can create a sched_start_time value to trigger a heap overflow by sending an integer value that is greater than the maximum value. If an application is configured to accept sched_start_time values of 0, 1, 2, 3, and 4, an attacker can craft a malicious data payload to cause a denial of service condition via a race condition.
This vulnerability is related to CVE-2018-9120 and has been assigned the identifier CVE-2018-9120.
This issue was addressed by not accepting sched_start_time values of 0, 1, 2, 3, and 4.
Tenda AC1206 US_AC1206V1.0RTL_V15.03.06.23_multi_TD01 has an exploitable memory corruption vulnerability in the sched_set_cq_threshold() function due to improper validation of input values. An attacker can craft a malicious data payload to force the application to read memory beyond the end of the allocated buffer via a race condition. If an application is configured to accept a value of 0, 1, 2, 3, and 4 for the sched_set_cq_threshold function, an attacker can force an overflow and cause a denial of service condition via a race condition.
This issue was addressed by validating the input values of the sched_set_cq_threshold function.
Tenda AC1206 US_AC12
Tenda AC1206 US_AC12.0RTL_V15.03.06.23_multi_TD01
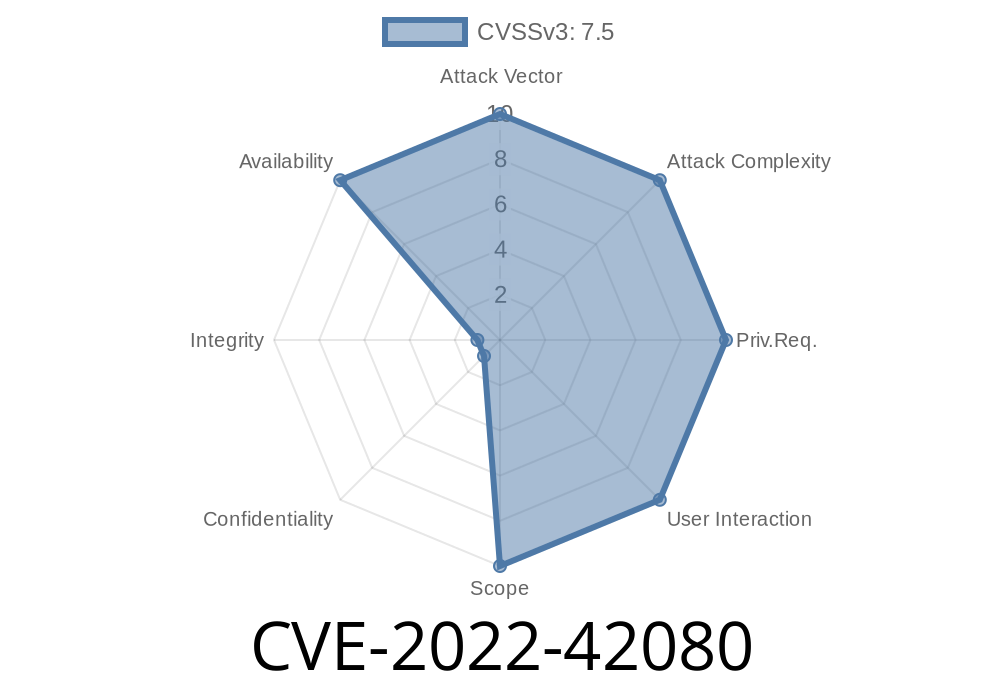
CVE-2022-42080
An attacker can craft a malicious data payload to cause a denial of service condition via a race condition. If an application is configured to accept sched_start_time values of 0, 1, 2, 3, and 4, an attacker can craft a malicious data payload to cause a denial of service condition via a race condition.
Tenda AC1206 US_AC12.0RTL_V15.03.06.23_multi_TD01 has an exploitable memory corruption vulnerability in the sched_set_cq_threshold() function due to improper validation of input values. An attacker can craft a malicious data payload to force the application to read memory beyond the end of the allocated buffer via a race condition. If an application is configured to accept a value of 0, 1, 2, 3, and 4 for the sched_set_cq_threshold function, an attacker can force an overflow and cause a denial of service condition via a race condition.
Tenda AC1206 US_AC12: Heap Based Vulnerability
The Tenda AC1206 US_AC1206V1.0RTL_V15.03.06.23_multi_TD01 has an exploitable heap-based vulnerability in the sched_set_cq_threshold() function due to improper validation of input values. An attacker can craft a malicious data payload to force the application to read memory beyond the end of the allocated buffer via a race condition, which could allow for arbitrary code execution by overwriting return addresses and so on. If an application is configured to accept a value of 0, 1, 2, 3, and 4 for the sched_set_cq_threshold function, an attacker can force an overflow and cause a denial of service condition via a race condition.
This issue was addressed by validating the input values of the sched_set_cq_threshold function.
Tenda AC1206 US_AC12 Firmware V15.00.00.02 and V15.03.06.23 have an exploitable memory corruption vu ability in the sched_set_cq_threshold() function due to improper validation of input values. An attacker can craft a malicious data payload to force the application to read memory beyond the end of the allocated buffer via a race condition. If an application is configured to accept a value of 0, 1, 2, 3, and 4 for the sched_set_cq_threshold function, an attacker can force an overflow and cause a denial of service condition via a race condition.
This issue was addressed by validating the input values of the sched_set_cq_threshold function.
Timeline
Published on: 10/12/2022 19:15:00 UTC
Last modified on: 10/14/2022 14:58:00 UTC