Unrestricted File Upload vulnerability is a serious issue, because it allows attackers to upload malicious files on the server, and execute malicious code, which can lead to data theft, or worse, an attack on the server.
As a best practice, it is recommended to restrict the upload of files (images, videos, etc) on your website, or at least to require user to select the type of file they are uploading. However, this may not be possible in all cases.
In such cases, it is recommended to setup file permission rules to restrict upload of files based on the user’s permission level.
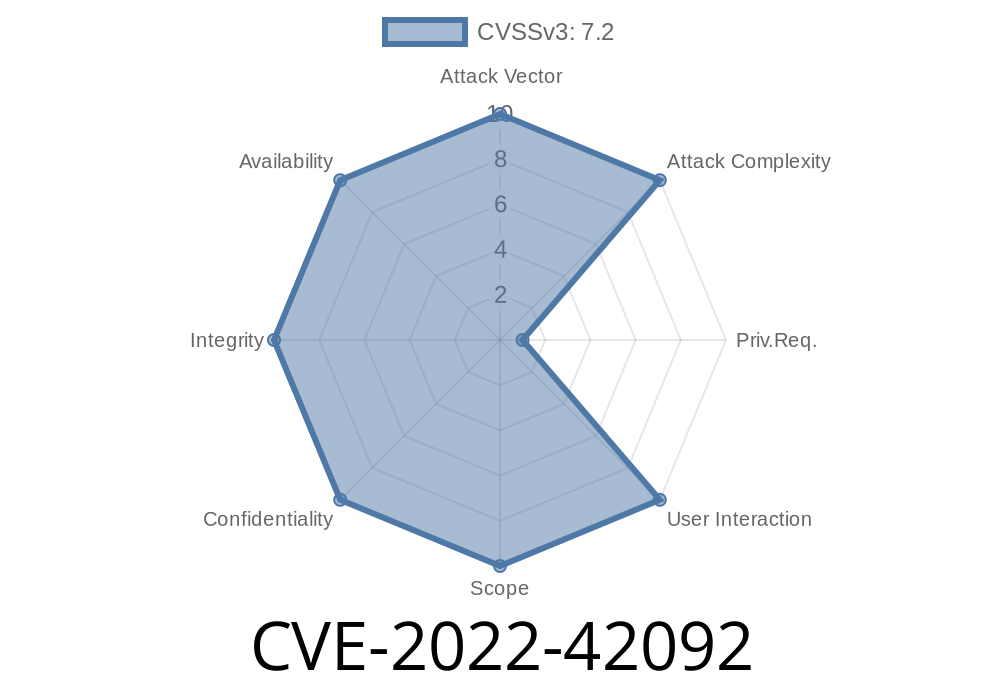
Backdrop CMS 1.22.0 has Unrestricted File Upload vulnerability via 'themes' that allows attackers to Remote Code Execution.
Steps to reproduce the vulnerability in Backdrop CMS
1.Create a new theme in Backdrop CMS and upload any file to it.
2.Go to the 'Themes' of your website, click on the newly created theme and upload any file to it
3.Upload a php file with ‘test’ in its name
How to Bypass File Permission Rules?
If the attacker has access to a user account, or the administrator is not properly securing the website, the attacker can configure their browser to use an anonymizing proxy.
In order to bypass file permission rules, attackers can upload files with special file names that are executed by PHP scripts. Such names include "index.php", "test.php", and "test2.php" (no quotes). This allows attackers to execute code in order to steal data from your website's database or perform other malicious activities on it.
The best way to prevent this is by limiting upload functionality in Backdrop CMS 1.22.0, or by using File Permission Rules which restrict upload of files based on the user’s permission level (READ_WRITE_EXECUTE).
Summary of the Unrestricted File Upload Vulnerability
When uploading a new theme to your website, it is possible for an attacker to upload a malicious file via 'themes' without any input validation.
This vulnerability allows attackers to execute Remote Code Execution on the server, which can lead to data theft or worse, an attack on the server.
Timeline
Published on: 10/07/2022 18:15:00 UTC
Last modified on: 10/09/2022 02:53:00 UTC