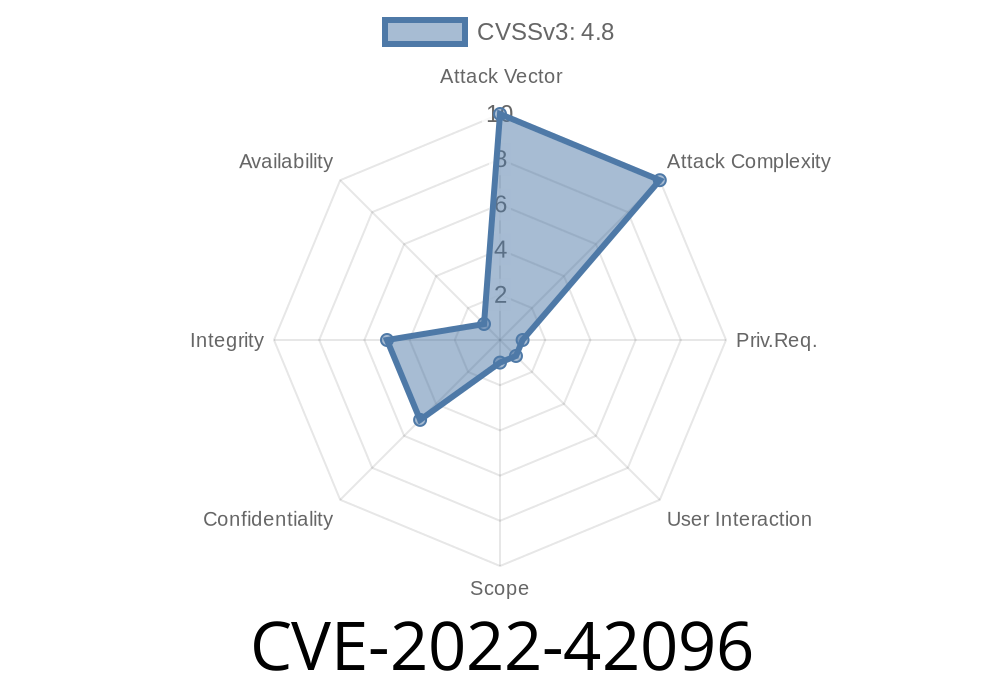
Backdrop CMS is an open-source content management platform, forked from Drupal, and is widely used due to its flexibility and powerful features. However, in version 1.23., a critical security issue—CVE-2022-42096—was uncovered. This vulnerability allows attackers to leverage Stored Cross-Site Scripting (XSS) via the regular content/post creation interface. In this post, we break down how this bug works, how you can test for it, and what you should do to keep your site safe.
What Is Stored XSS?
Stored XSS occurs when an attacker can inject malicious scripts that are later served to other users. Unlike reflected XSS (which bounces the attack through a URL), stored XSS gets "saved" in the database and executed whenever someone views the infected page.
How Does CVE-2022-42096 Happen in Backdrop CMS?
In Backdrop CMS 1.23., insufficient content sanitization allows arbitrary JavaScript to be injected into post content. Any user with access to create a post—like a trusted author or someone with escalated privileges—can abuse this.
Typical XSS vectors like <script>, <img onerror=...>, or <svg> tags will get stored in the database and then rendered verbatim in the browser of anyone visiting the infected page.
In the Body field, insert a malicious XSS payload, like so
<img src="x" onerror="alert('XSS by CVE-2022-42096');">
What Happens?
When any user (even an admin!) views this post, their browser triggers the JavaScript alert(), showing that arbitrary scripts can run. More dangerous payloads could steal cookies or session data.
Example screenshot of a vulnerable post
<!-- Snippet as shown in HTML source -->
<img src="x" onerror="alert('Gotcha! This is a stored XSS');">
Animated Demo
// JavaScript triggered by the XSS payload
alert('XSS by CVE-2022-42096');
Impact
- Attackers who gain access to post content can execute custom JavaScript in the browser of anyone viewing the crafted content.
- Credible phishing, session hijacking, or browser exploit attacks are possible once a payload is stored.
Insert an XSS payload as post content.
3. Save/Publish the post.
Remediation
- Upgrade immediately to a patched Backdrop CMS version. (See latest release)
Responsible Disclosure and References
The issue was responsibly reported and fixed by the Backdrop security team.
- NVD Entry for CVE-2022-42096
- Backdrop CMS Security Advisories
- Backdrop Project Page
- OWASP XSS Prevention Cheat Sheet
TL;DR
CVE-2022-42096 affects Backdrop CMS 1.23. and enables anyone with post privileges to plant persistent, stored XSS attacks via post content. Patch your CMS as soon as possible, and check your site for suspicious or unfamiliar content.
If you're running Backdrop CMS and aren’t sure about your current version, check and update promptly—stored XSS is a silent, but extremely powerful, attacker vector.
Stay safe, and always keep your CMS updated. If you suspect you’ve been targeted by this or a related attack, seek help from a professional security expert.
Timeline
Published on: 11/21/2022 21:15:00 UTC
Last modified on: 11/23/2022 15:01:00 UTC