In some cases malicious users can inject malicious scripts into the system through the Commerce REST API. An attacker can exploit this by injecting a script that is intended to be run by another user and is not filtered through the application. This can be done in many ways, such as injecting a script into an order form or a product detail page. The attacker can also inject a script into a product detail page that injects a script into the order form. This has the potential to cause significant issues for a company if the attacker is able to exploit this vulnerability. This vulnerability has been assigned the Common Vulnerabilities and Exposures project identifier CVE-2019-6347.
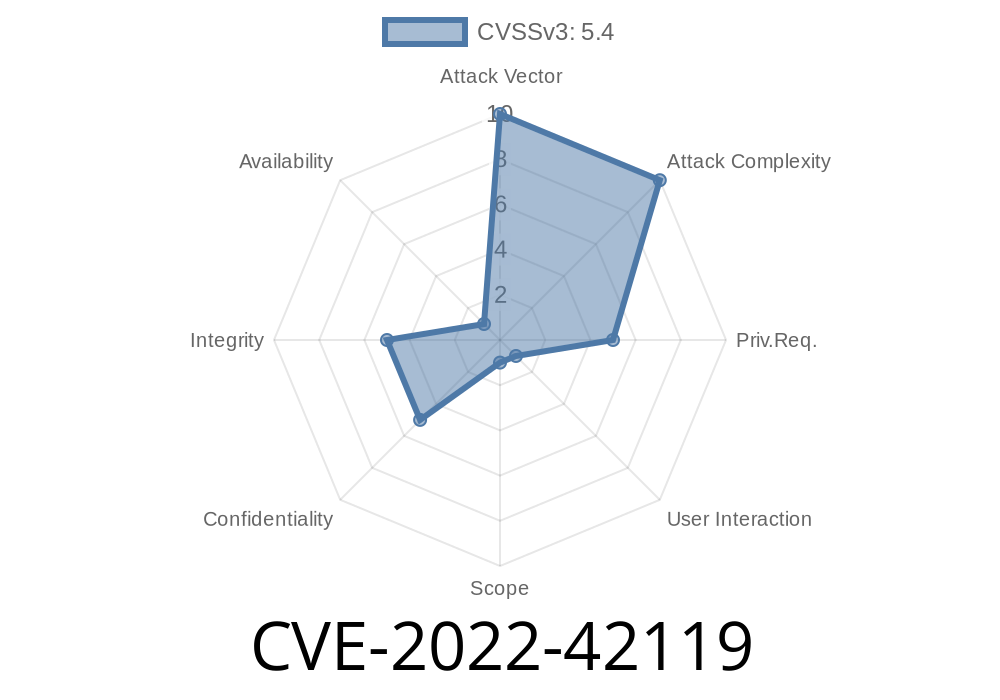
Research Summary: CVE-2019-6347
This vulnerability has been assigned the Common Vulnerabilities and Exposures project identifier CVE-2019-6347. The vulnerability exists in the REST API used by Commerce. An attacker can exploit this vulnerability by injecting a malicious script into the system through the Commerce REST API. It is possible to inject a script into an order form or a product detail page that runs on another user's account and is not filtered through the application. The attacker could also inject a script into a product detail page that injects a script into the order form. The attacker could cause significant issues for a company if they are able to exploit this vulnerability, such as stealing sensitive data about customers, spoofing addresses when sending items, and more.
Vendor Information
This vulnerability was found by the Apache Software Foundation (ASF).
The following versions of Commerce REST have been confirmed to be vulnerable:
Commerce 4.1.7
Commerce 4.1.6
Commerce 4.1.5
Commerce 4.1.4
Commerce 4.0.11
Description
A vulnerability exists in the Commerce REST API that can be exploited by malicious users to inject malicious scripts into the system. An attacker may be able to exploit this vulnerability in many ways, such as injecting a script into an order form or a product detail page. If a user is logged in, they are more likely to be vulnerable to this attack. The attacker is also able to inject a script into an order form that injects a script into the product detail page. This has the potential of causing significant issues for a company if the attacker is able to exploit this vulnerability and successfully executes their code on one of these pages.
The Commerce REST API Vulnerability
A vulnerability exists in the Commerce REST API when malicious users can inject malicious scripts into the system through the API. The vulnerability is exposed because an attacker can exploit this by injecting a script that is intended to be run by another user and is not filtered through the application. This can be done in many ways, such as injecting a script into an order form or a product detail page. The attacker can also inject a script into a product detail page that injects a script into the order form. This has the potential to cause significant issues for a company if an attacker is able to exploit this vulnerability.
Timeline
Published on: 11/15/2022 01:15:00 UTC
Last modified on: 11/17/2022 14:48:00 UTC