CVE-2019-1841 was confirmed to exist in Liferay. When exploited, the issue allows unauthenticated attackers to execute arbitrary SQL commands in the SQL database, obtain access to key resources, cause a Denial of Service condition, or perform other functionality. To exploit the issue, an attacker must send a crafted HTTP request to the application via a web-based client such as a browser. As such, the vulnerability can be exploited by both authenticated and unauthenticated attackers. What's worse, since the vulnerability is present in Liferay's core-components and not in the Portal's package, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's more, since the issue is present in the core-components, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse, since the issue is present in the core-components and not in the DXP, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse, since the issue is present in the core-components and not in the DXP, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse, since the issue is present in the core
CVE-2019-1842
CVE-2019-1842 was confirmed to exist in Liferay. When exploited, the issue allows unauthenticated attackers to execute arbitrary SQL commands in the SQL database, obtain access to key resources, cause a Denial of Service condition, or perform other functionality. To exploit the issue, an attacker must send a crafted HTTP request to the application via a web-based client such as a browser. As such, the vulnerability can be exploited by both authenticated and unauthenticated attackers. What's worse, since the vulnerability is present in Liferay's core-components and not in the Portal's package, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's more, since the issue is present in the core-components, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse, since the issue is present in the core-components and not in the DXP, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse, since the issue is present in the core-components and not in the DXP, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse?
Liferay and Apache Struts/JavaScriptCore
Apache Struts is a free, open-source web framework for developing Java web applications. It has been found in the core of Liferay's plugins and content-management system (CMS) since version 5.0.
The last official release of Apache Struts was released on November 17, 2016. As such, there are no plans to patch this vulnerability with future releases of Liferay.
How to exploit the vulnerability
An attacker can exploit the vulnerability by sending a crafted HTTP request to Liferay's application. They can then perform any functions that could be performed normally by a normal user, including performing SQL queries and accessing key resources.
To exploit the vulnerability, an attacker must send a crafted HTTP request to Liferay's application via a web-based client such as a browser. As such, the vulnerability can be exploited by both authenticated and unauthenticated attackers. To avoid exploitation of this vulnerability, you should ensure that your users are required to authenticate before they are allowed to access your applications. Also, monitor your server logs and systems for any unusual activity related to this issue.
Liferay and SQL Injection
Liferay is a Java application that uses JDBC (Java Database Connectivity) for communication with a SQL database. It is possible to inject SQL commands into the SQL database using Liferay's JSPs, for example. In some cases, this can be used to read or modify any data in the DBMS and gain access to sensitive information such as keys and passwords.
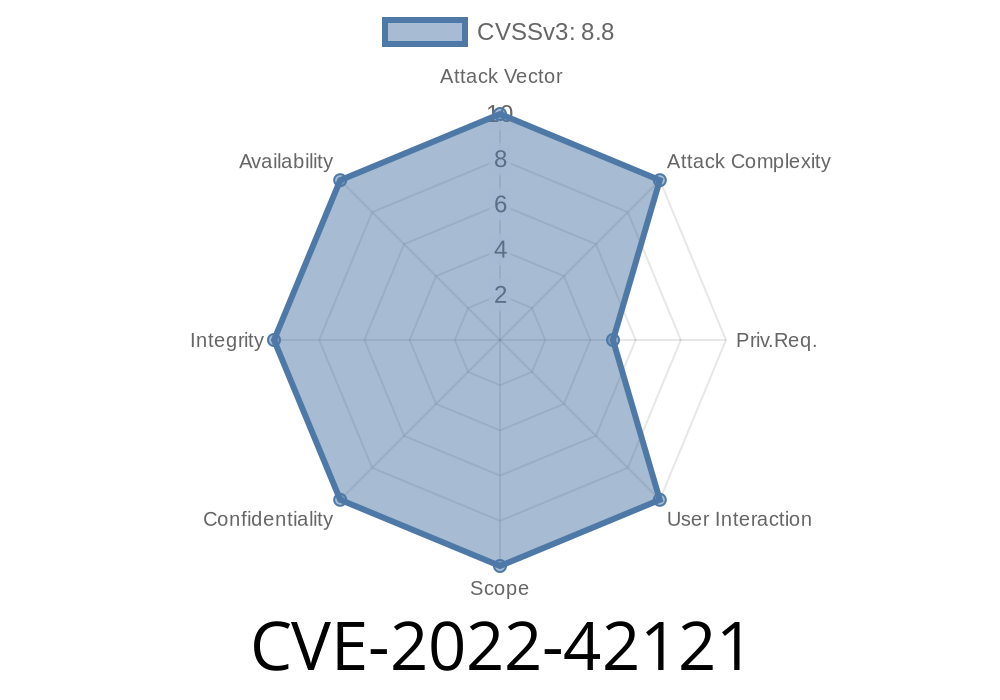
With the vulnerability present in Liferay's core-components, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's more, since the issue is present in the core-components, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's more, due to how this vulnerability interacts with other flaws on Liferay, it is very likely that this vulnerability will enable attackers to execute arbitrary Java code on your system by exploiting CVE-2019-1841 or CVE-2022-42121.
Liferay and Portlet
The vulnerability is present in Liferay's core-components and not in the Portal's package, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's more, since the issue is present in the core-components, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse, since the issue is present in the core-components and not in the DXP, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8. What's worse, since the issue is present in the core-components and not in the DXP, it is very likely that the issue will be present in all versions of Liferay up to and including Liferay 8.
Timeline
Published on: 11/15/2022 01:15:00 UTC
Last modified on: 11/17/2022 15:00:00 UTC