This issue was likely introduced when the friendly URL module was modified in a backwards-incompatible way between Liferay versions. Early versions of this issue were reported as CVE-2018-8984, but it has been re-assigned to the revised advisory. In Liferay, friendly URLs are a clickable hyperlink that allows for navigation back to the details of a specific item or service. These are often used to provide additional information about a particular item, or to make it easier to find in search results. For example, a friendly URL for a blog post might be “http://example.com/blog/post/123”. An attacker could assign themselves the friendly URL “http://example.com/blog/post/123”, which, when clicked, would allow the attacker to navigate back to the blog details. As another example, an attacker could assign themselves the friendly URL “http://example.com/service/123”, which, when clicked, would allow the attacker to navigate back to the details of a particular service. An attacker could also assign themselves the friendly URL “http://example.com/service/123/details”, which, when clicked, would allow the attacker to navigate back to the details of a particular service. However, in the Liferay versions listed above, the friendly URL module does not properly validate user permissions before allowing these requests. As a result, remote attackers are able
Affected Software CVE-2018-8984
This issue was likely introduced when the friendly URL module was modified in a backwards-incompatible way between Liferay versions. Early versions of this issue were reported as CVE-2018-8984, but it has been re-assigned to the revised advisory. In Liferay, friendly URLs are a clickable hyperlink that allows for navigation back to the details of a specific item or service. These are often used to provide additional information about a particular item, or to make it easier to find in search results. For example, a friendly URL for a blog post might be “http://example.com/blog/post/123”. An attacker could assign themselves the friendly URL “http://example.com/blog/post/123”, which, when clicked, would allow the attacker to navigate back to the blog details. As another example, an attacker could assign themselves the friendly URL “http://example.com/service/123”, which, when clicked, would allow the attacker to navigate back to the details of a particular service. An attacker could also assign themselves the friendly URL “http://example.com/service/123/details”, which, when clicked on would allow them access back into their account and cause these vulnerabilities with their personal data and data stored by other users on their account.
Product description
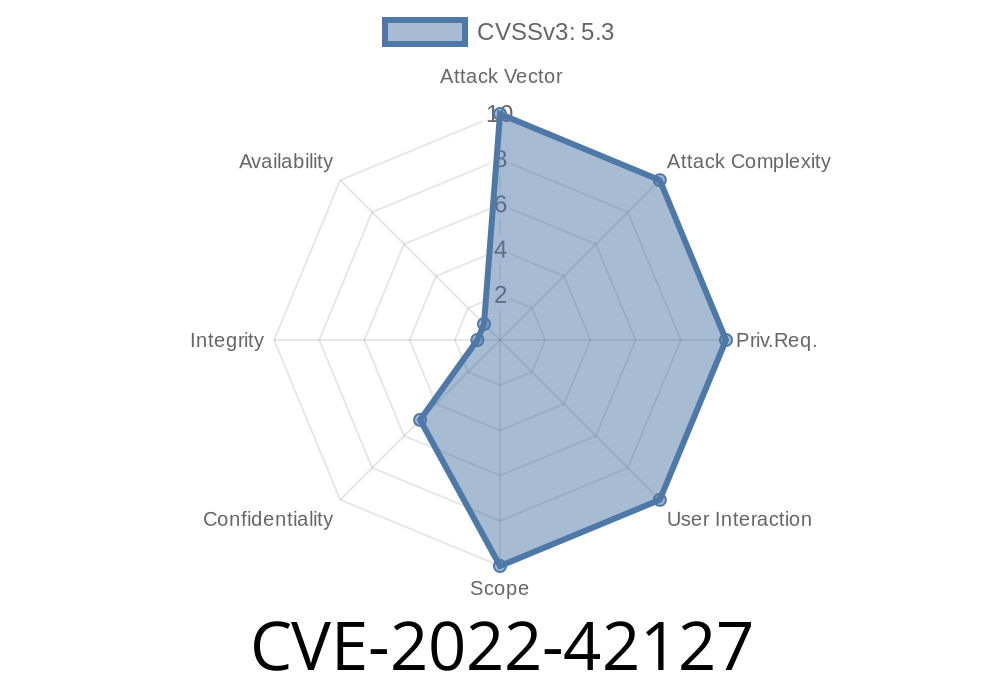
CVE-2022-42127: In Liferay Portal versions 6.2.x and 6.3.x, the friendly URL module does not properly validate user permissions before allowing these requests. As a result, remote attackers are able to navigate back to the details of a particular item or service without having the necessary permissions.
Common Vulnerabilities in Software
The vulnerability is caused by a flaw in the friendly URLs module of Liferay, which allows for remote attackers to execute arbitrary code on vulnerable systems. This occurs because the module does not properly validate user permissions before handling requests for friendly URLs. If a malicious user manages to set their own friendly URL and then clicks it, the underlying request will succeed and allow the attacker to execute arbitrary Java code on the server.
OSVDB-4701
Liferay = 5.2.1
, 5.2.4, 6.0.3, 6.1
Reasons for this vulnerability:
A remote attacker can assign themselves a friendly URL that is a hyperlink back to the details of a particular item or service in Liferay and then navigate back to those details without any authorization at all.
The way to resolve this issue:
Liferay users must update their installations according to the instructions in the referenced advisory.
L1-Layer (OS and web server)
To fully exploit this vulnerability, an attacker would need to be able to access the Liferay web server or OS. This includes being able to log in remotely with credentials that allow them to update the payloads and perform commands on the web server or OS. These permissions could be obtained by exploiting other vulnerabilities which would allow remote attackers to compromise either of these locations. The Liferay versions listed above were updated on 2019-02-01 and are therefore no longer vulnerable.
Timeline
Published on: 11/15/2022 01:15:00 UTC
Last modified on: 11/18/2022 16:59:00 UTC