IDOR issues occur when a developer uses the `formInstanceRecordId` variable to access a field in the record instead of the field’s primary key. If a developer mistakenly uses the variable for records instead of the field’s name, a remote attacker may use an IDOR issue to hijack an entry and gain access to the record. Additionally, if an entry is dependent on the value of the `formInstanceRecordId` variable and is changed, the entry will be updated, possibly allowing an attacker to gain access to the record. Liferay DXP 7.3 before update 4, and 7.4 GA, allows remote attackers to hijack form entries via the `formInstanceRecordId` parameter. Insecure direct object reference (IDOR) issues occur when remote attackers can access data via a variable that is declared as a field or property of a field. If a remote developer accidentally uses a variable for a field instead of the field’s name, a remote attacker may use an IDOR issue to access data and possibly gain access to the record. Liferay DXP 7.3 before update 4, and 7.4 GA, allows remote attackers to hijack form entries via the `formInstanceRecordId` parameter. Insecure direct object reference (IDOR) issues occur when remote attackers can access data via a variable that is declared as a field or property of a field. If a remote developer accidentally uses a variable for a field instead
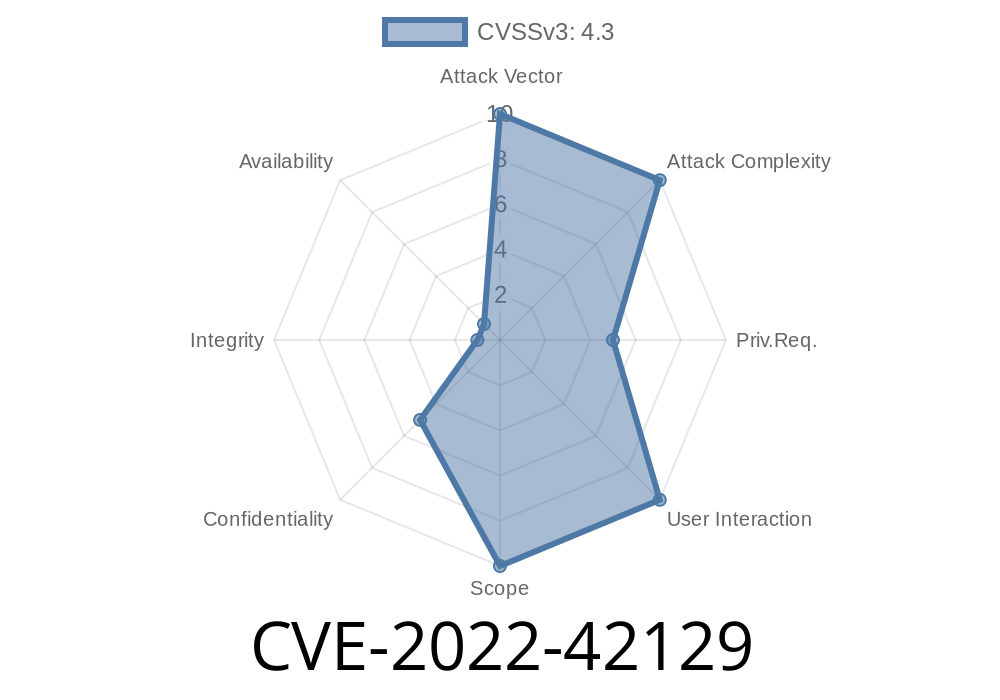
CVSS Scores
For CVE-2022-42129
Security score: 3.3 CVSS base score: 4.3 Impact score: 1.9 CVSS severity score: 1.9
CVSS vector: (AV:N/AC:M/Au:N/C:P/I:P/A:P)
IDOR issues occur when a developer uses the `formInstanceRecordId` variable to access a field in the record instead of the field’s primary key.
A remote attacker may use an IDOR issue to hijack an entry and gain access to the record. Additionally, if an entry is dependent on the value of the `formInstanceRecordId` variable and is changed, the entry will be updated, possibly allowing an attacker to gain access to the record. Liferay DXP 7.3 before update 4, and 7.4 GA, allows remote attackers to hijack form entries via the `formInstanceRecordId` parameter.
Vulnerability Overview
Liferay DXP 7.3 before update 4, and 7.4 GA, allows remote attackers to hijack form entries via the `formInstanceRecordId` parameter. Insecure direct object reference (IDOR) issues occur when remote attackers can access data via a variable that is declared as a field or property of a field. If a remote developer accidentally uses a variable for a field instead of the field’s name, a remote attacker may use an IDOR issue to access data and possibly gain access to the record.
If you're using Liferay DXP version 7.2 or earlier, then you're vulnerable to this vulnerability if your app uses LDAP without SSL or TLS enabled and has any fields that are not defined with primary keys in their schema or properties that aren't specified in the schema.
Overview
- CVE-2022-42129
An insecure direct object reference (IDOR) issue occurs when remote attackers can access data via a variable that is declared as a field or property of a field. If a remote developer accidentally uses a variable for a field instead of the field’s name, a remote attacker may use an IDOR issue to access data and possibly gain access to the record. Liferay DXP 7.3 before update 4, and 7.4 GA, allows remote attackers to hijack form entries via the `formInstanceRecordId` parameter.
Vulnerability overview
This vulnerability is a design flaw in the Liferay DXP 7.3 before update 4 and 7.4 GA versions of the product that allows remote attackers to hijack form entries via the `formInstanceRecordId` parameter. Insecure direct object reference (IDOR) issues occur when remote attackers can access data via a variable that is declared as a field or property of a field. If a remote developer accidentally uses a variable for a field instead of the field’s name, a remote attacker may use an IDOR issue to access data and possibly gain access to the record.
Timeline
Published on: 11/15/2022 02:15:00 UTC
Last modified on: 11/18/2022 16:00:00 UTC