The XSRF-TOKEN cookie is set by the server in response to an X-XSRFToken request received by the client. The XSRF-TOKEN value is stored in the server’s database and is thus not suitable for inclusion in client-side forms. To exploit this issue, an attacker must be able to control a vulnerable installation of the ERP system and request an XSRF-TOKEN cookie. Once an attacker has access to the ERP system, they can request any file of their choosing via a request for a specific file. If the file exists, it will be served; if it does not, the XSRF-TOKEN cookie will be set, allowing the attacker to access the system. An attacker can control any vulnerable installation of the ERP system. XSRF-TOKEN cookie is not suitable for inclusion in client-side forms. An attacker must be able to control a vulnerable installation of the ERP system.
Vulnerability overview
The XSRF-TOKEN cookie is set by the server in response to an X-XSRFToken request received by the client. The XSRF-TOKEN value is stored in the server’s database and is thus not suitable for inclusion in client-side forms. To exploit this issue, an attacker must be able to control a vulnerable installation of the ERP system and request an XSRF-TOKEN cookie. Once an attacker has access to the ERP system, they can request any file of their choosing via a request for a specific file. If the file exists, it will be served; if it does not, the XSRF-TOKEN cookie will be set, allowing the attacker to access the system. An attacker can control any vulnerable installation of the ERP system.
Vulnerable System Requirements
The vulnerable system requirements for exploiting this issue include the following:
- An ERP system that has XSRF-TOKEN set in response to an X-XSRFToken request
- The attacker must be able to control the vulnerable installation of the ERP system
- The server must return a valid cookie value in response to an X-XSRFToken request
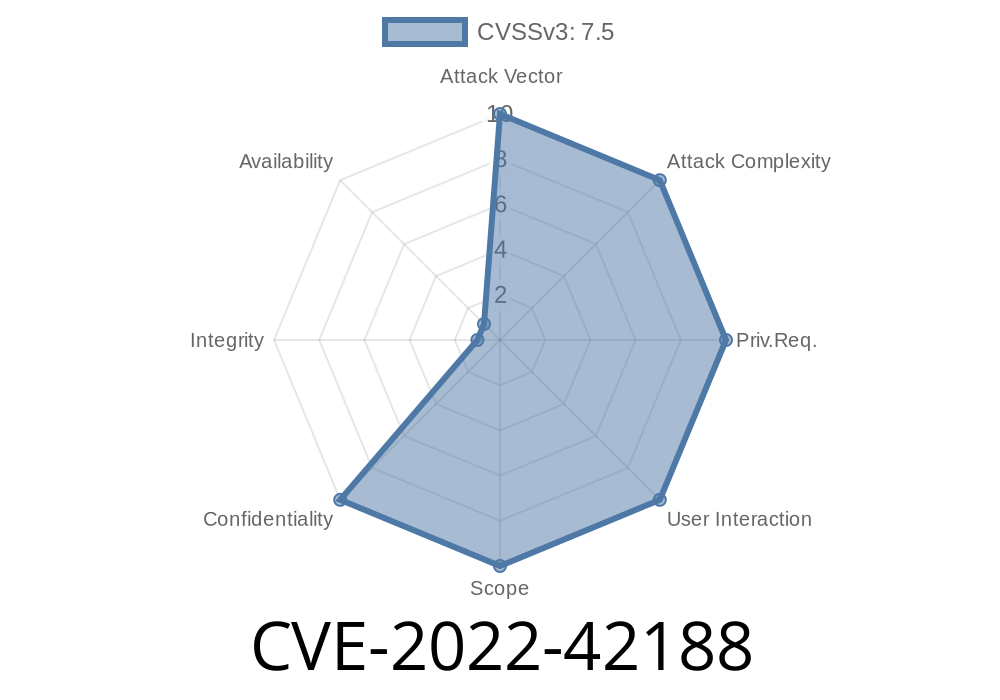
CVE-2023-42190
The XSRF-TOKEN cookie is set by the server in response to an X-XSRFToken request received by the client. The XSRF-TOKEN value is stored in the server’s database and is thus not suitable for inclusion in client-side forms. To exploit this issue, an attacker must be able to control a vulnerable installation of the ERP system and request an XSRF-TOKEN cookie. Once an attacker has access to the ERP system, they can request any file of their choosing via a request for a specific file. If the file exists, it will be served; if it does not, the XSRF-TOKEN cookie will be set, allowing the attacker to access the system. An attacker can control any vulnerable installation of the ERP system.
CSRF-COOKIE-BLOCKER
The CSRF-COOKIE-BLOCKER cookie is set by the server in response to a CSRF request received by the client. The CSRF-COOKIE-BLOCKER value is stored in the server’s database and is thus not suitable for inclusion in client-side forms. To exploit this issue, an attacker must be able to control a vulnerable installation of the ERP system and submit a malicious request for a specific file. If the file exists, it will be served; if it does not, then the request with CSRF-COOKIE-BLOCKER cookie will be executed, allowing the attacker to gain access to the system. An attacker can control any vulnerable installation of the ERP system. CSRF-COOKIES are not suitable for inclusion in client-side forms. An attacker must be able to control a vulnerable installation of the ERP system.
The XSRF-TOKEN cookie is set by the server in response to an X-XSRFToken request received by the cli
The XSRF-TOKEN cookie is set by the server in response to an X-XSRFToken request received by the client. The XSRF-TOKEN value is stored in the server’s database and is thus not suitable for inclusion in client-side forms. To exploit this issue, an attacker must be able to control a vulnerable installation of the ERP system and request an XSRF-TOKEN cookie. Once an attacker has access to the ERP system, they can request any file of their choosing via a request for a specific file. If the file exists, it will be served; if it does not, the XSRF-TOKEN cookie will be set, allowing the attacker to access the system. An attacker can control any vulnerable installation of the ERP system.
Timeline
Published on: 10/18/2022 19:15:00 UTC
Last modified on: 10/20/2022 15:40:00 UTC