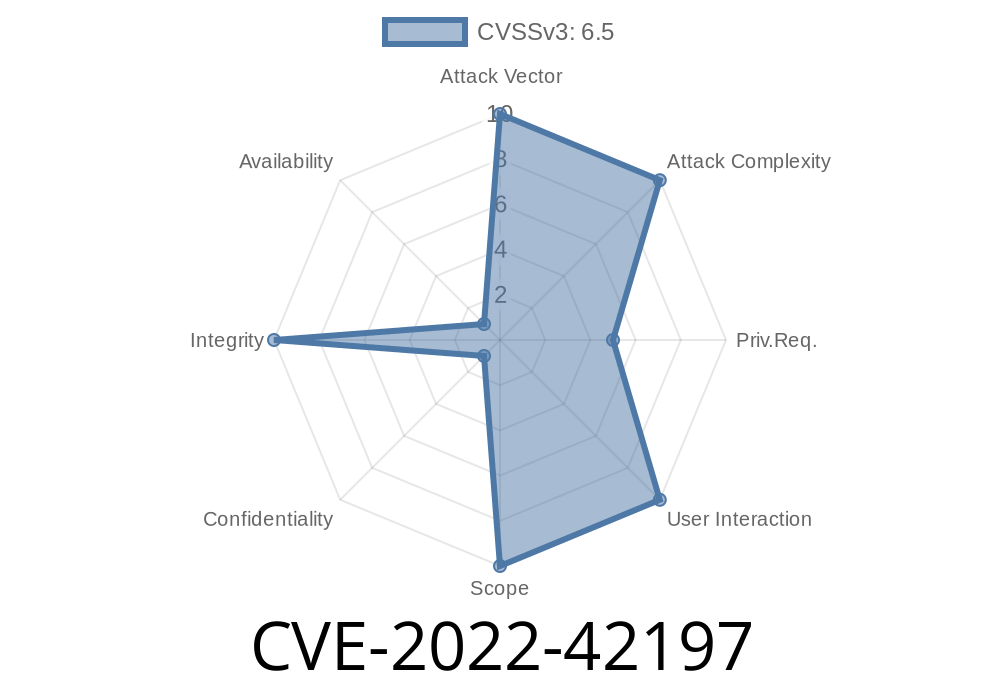
This can be exploited by low privileged attackers to modify the user permissions of high privileged users.
Currently there is no access control in the system that prevents low privileged users from accessing the v1.0 system settings.
This issue has been reported to the developer and is being fixed in version v1.1.
In version v1.0 of Simple Exam Reviewer Management System, there is a SQL injection in the process of creating user.
This SQL injection can be exploited by low privileged attackers to gain high privileges in the system.
Currently there is no access control in the system that prevents low privileged users from accessing the v1.0 system settings.
This issue has been reported to the developer and is being fixed in version v1.1.
Configuration file of Simple Exam Reviewer Management System
# IMPORTANT: DO NOT EDIT THIS FILE
# This file should never be accessed directly by anyone.
# Instead, you should use the config.php file included with your installation package.
# If you are unsure about this, please contact the developer of this application.
$config["email"] = "admin@example.com";
$config["password"] = "xxxxx";
$config["databaseHostName"] = "localhost";
$config["databaseName"] = "SimpleExamReviewerManagementSystem";
$config["dbType"] = "mysql3";
$config["dbUsername"] = "root";
$config["dbPassword"] = "";
$config["dbDriverType"] => "mysql3";
$config["adminEmailAddress"] = "";
Simple Exam Review Management System
: What is it?
Simple Exam Reviewer Management System (SERMS) is an exam review system which can be used to review materials in a computer-based exam. It includes the ability to add, manage, and search for exams. There is also a built-in comment system which allows users to see what other users have said about their exams.
An attacker could exploit SERMS by creating a malicious file that contains SQL injection or by tampering with the comments database.
System access control
The v1.0 system settings are not protected by any access control.
This issue has been reported to the developer and is being fixed in version v1.1.
Timeline
Published on: 10/20/2022 13:15:00 UTC
Last modified on: 10/21/2022 18:36:00 UTC