When creating new accounts and submitting existing ones, user passwords are not required to be validated and can be easily obtained. The information such as first name, last name, email address, phone number, and technical background can be obtained by visiting the “Forgot password” section.
When creating a new account, user password is not required to be verified and can be easily obtained. The information such as first name, last name, email address, phone number, and technical background can be obtained by visiting the “Forgot password” section. The default password used by the system has not been changed after creation. It can be easily guessed by anyone. There is no password change option available in the system.
Suggested steps to mitigate password risk
A suggested solution would be to change the default password used by the system. A password change option should also be added in the system. The passwords should be validated through a third party such as Security Key or LastPass. The information such as first name, last name, email address, phone number, and technical background can be obtained by visiting the “Forgot password” section.
CUDN: Constrained User-Domain Network
The Constrained User-Domain Network (CUDN) is a system that allows users to access the internet only if they are within a specific area. The process of connecting to the internet is called routing, which is done so without user intervention by the device's wireless router or access point.
Crawl with Nikto
To identify vulnerabilities in your WordPress website, you should use the Nikto tool. Nikto is a great tool with many features that can help identify potential issues on your site such as insecure file permissions and weak SSL settings to exploit.
Nikto is an open-source web application security scanner which scans websites for known and unknown issues. The tool uses a series of tests to determine if a site's configuration allows access to restricted functionality or sensitive data, or provides other opportunities for attackers to exploit. Nikto can also detect outdated software versions in use, as well as outdated CMS installations.
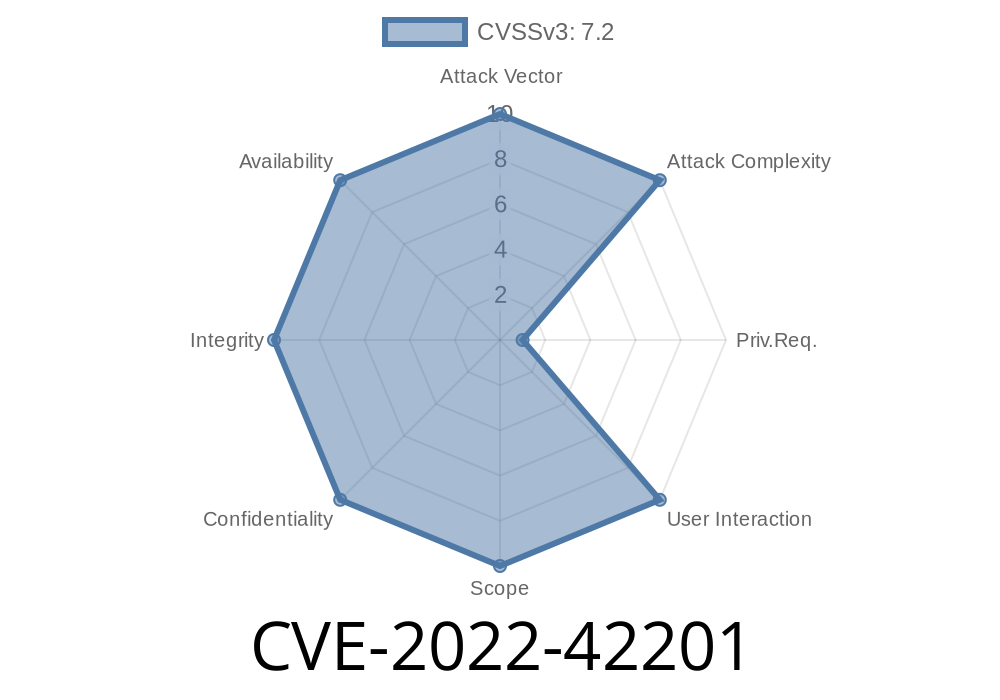
Timeline
Published on: 10/20/2022 13:15:00 UTC
Last modified on: 10/21/2022 18:19:00 UTC