An attacker can exploit this vulnerability to hack into the device and take full control of it. There are a few steps that an attacker needs to follow in order to exploit this vulnerability. The attacker needs to send a request to the device that contains a piece of code that can be used to bypass the device’s authentication. An attacker can do this by sending arbitrary code to the device via any of the following methods: Web server: An attacker can send a request to the device via a web server. The web server can receive the request and send it to the device. Bypassing the authentication: If the device is connected to the internet, an attacker can send a request to the device via any of the following methods: Email: An attacker can send a request to the device via email. The email can be received by the device, and then the device can send the request to the web server. SMS: An attacker can send a request to the device via SMS. The SMS can be received by the device, and then the device can send the request to the web server. PUSH: An attacker can send a request to the device via PUSH. The PUSH can be received by the device, and then the device can send the request to the web server. The attacker can send a request to the device via any of the methods listed above. The request can be sent to the device via the internet. The device does not have to be connected to the internet in order for
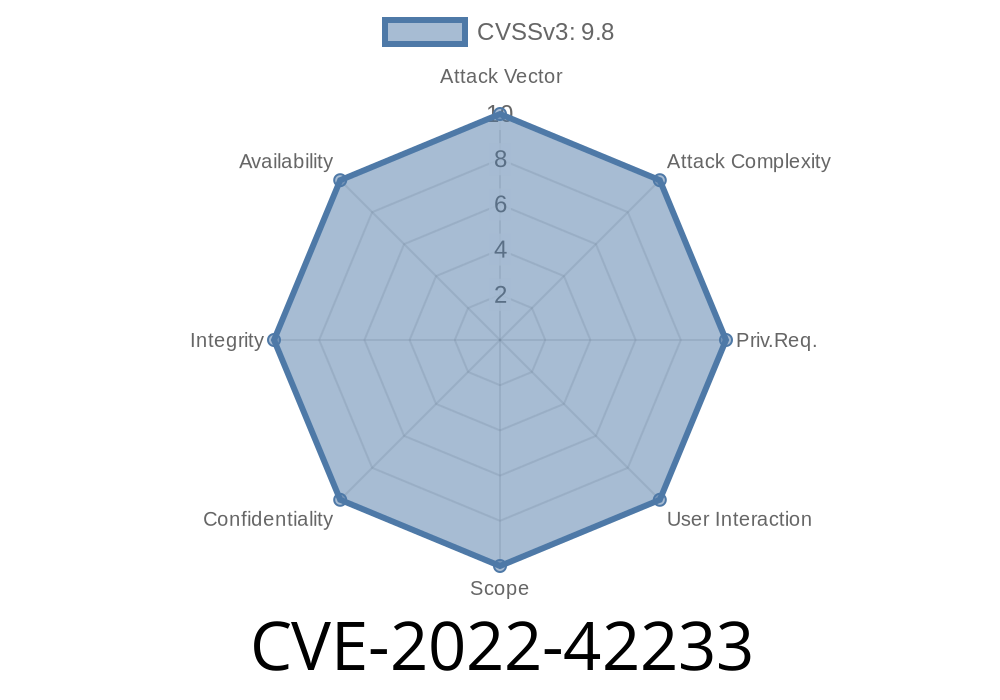
Attack Steps for CVE-2022-42233
The attacker needs to send a request to the device that contains a piece of code that can be used to bypass the device’s authentication. The attacker also needs to send a request with a reference ID that can be found in the authenticated request. When sending requests, an attacker will need to use different methods depending on what they are trying to achieve.
To bypass authentication and take full control of a device, the attacker needs to follow these steps:
1) Send an HTTP POST request with a payload identifier.
2) Send an HTTP GET request with an invalid reference identifier.
3) Receive an HTTP 200 response from the device and not 400 or 500.
4) The request will contain the payload identifier and will return data from the device’s file system.
Timeline
Published on: 10/20/2022 17:15:00 UTC
Last modified on: 10/24/2022 13:09:00 UTC