This CSRF vulnerability can be exploited when a user access a malicious website. When the user logged into the system, the “Create system administrator” permission can be granted to a remote attacker.
In order to exploit this vulnerability, the attacker needs to trick the user to visit malicious website. For example, the attacker can send an email with a malicious link or social media messages with malicious links. When the user click on the link, the user’s browser will redirect to the malicious website, then the attacker can exploit this vulnerability. This vulnerability can be exploited when the user having system administrator role. It means that if you are having system administrator role in the remote server, then you can exploit this vulnerability. This vulnerability can be exploited by remote attackers to add system administrator account.
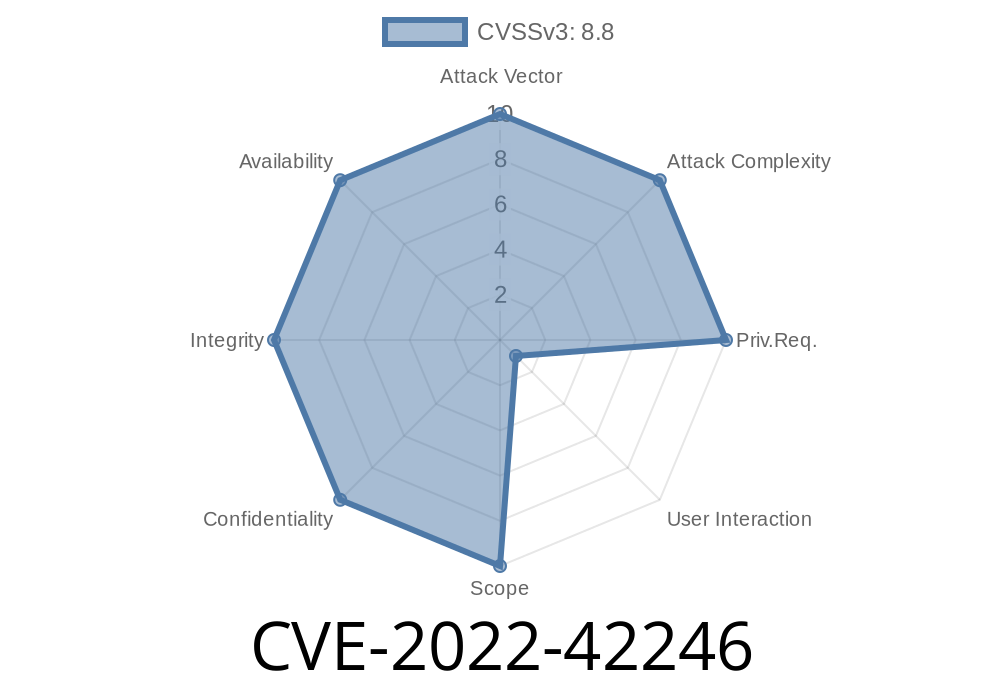
Vulnerability Details
This vulnerability allows remote attackers to add system administrator account.
Vulnerability Details:
The vulnerability exists due to insufficient input validation on a privileged context.
1. When the user logged into the system, the "Create system administrator" permission can be granted to a remote attacker.
2. For exploitation, the attacker needs to trick the user to visit malicious website. For example, the attacker sends an email with a malicious link or social media messages with malicious links.
Vulnerability overview
This vulnerability is CSRF vulnerability. The vulnerability occurs when a user access a malicious website and the website redirects the browser to another website. The attacker can exploit this vulnerability by tricking the user to visit malicious website, then the attacker can add system administrator account in the remote server. It means that if you are having system administrator role in remote server, then you can exploit this vulnerability.
In order to exploit this vulnerability, the attacker needs to trick the users into visiting malicious website by sending email with malicious link or social media messages with malicious links.
Authentication and Session Management
Authentication and session management are two important processes in web applications. Authentication determines whether a user should be allowed to access the application, while session management keeps track of information about that user’s interaction with the application. When vulnerabilities like CSRF are exploited, these processes can be tricked as well.
If a vulnerability like this is exploited, malicious users can be given unauthorized access to certain parts of your system through your website. This could be done by exploiting vulnerabilities such as SQL injection or Cross-site scripting (XSS).
In order to prevent against exploitation of CSRF, it is crucial for developers to implement secure authentication and session management when developing web applications. These vulnerabilities should also be taken into consideration when designing the architecture of your application.
Timeline
Published on: 11/17/2022 04:15:00 UTC
Last modified on: 11/17/2022 23:27:00 UTC