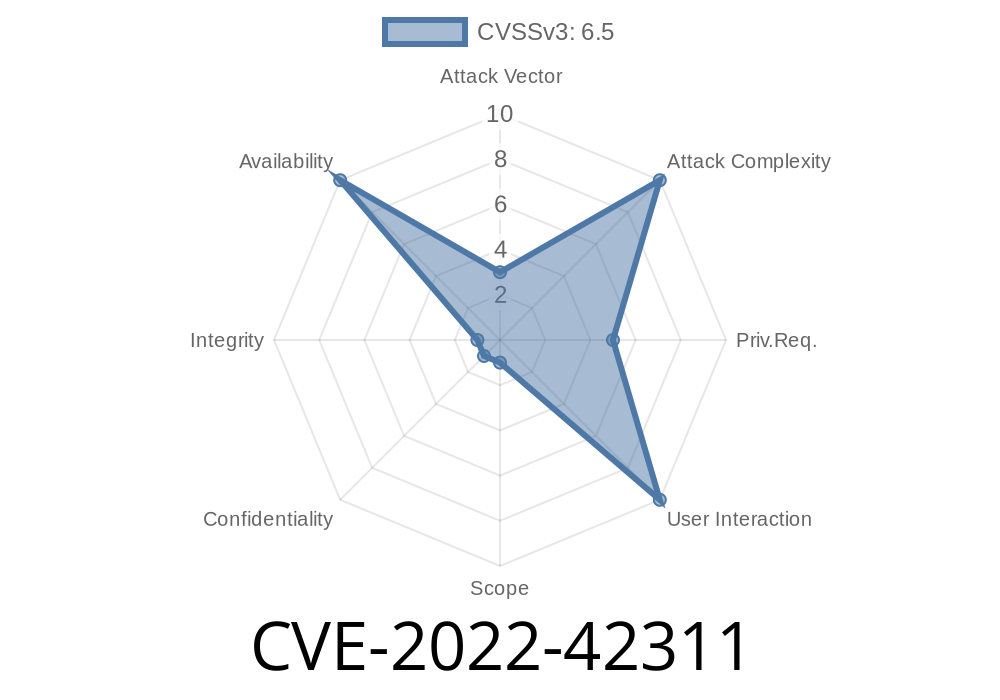
together with the debug option enabled in which case the debugger will be attached to the request/response which can lead to DoS due to long response times. The last two cause the most critical issue where an attacker can create non-trivial requests which can cause huge memory consumption when executed by a malicious guest. When the malicious guest does not have the ability to run large amounts of requests (e.g. due to insufficient memory) then it can still cause large memory consumption by doing many watches and deleting many xenstore nodes at once. The last scenario can be handled by restricting the maximum allowed path length or maximum allowed size in each transaction. When limiting the path length, the maximum allowed path length should be set to a value high enough to avoid being reached in the future. When limiting the size, the maximum allowed size should be set to avoid being reached in the future. The limit can be set in the configuration file or can be changed dynamically via the --max-path-length or --max-size command line options. A script can be used to automate the setting of these limits.
Limiting maximum path length
The maximum allowed path length can be set in the configuration file or can be changed dynamically via the --max-path-length or --max-size command line options. A script can be used to automate the setting of these limits.
Limiting Path Length
The path length is set in the configuration file. The default value of the path length is 2048. When increasing the maximum allowed path length, the path lengths for watched nodes cannot be changed.
Timeline
Published on: 11/01/2022 13:15:00 UTC
Last modified on: 12/03/2022 02:05:00 UTC
References
- https://xenbits.xenproject.org/xsa/advisory-326.txt
- http://xenbits.xen.org/xsa/advisory-326.html
- https://www.debian.org/security/2022/dsa-5272
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ZLI2NPNEH7CNJO3VZGQNOI4M4EWLNKPZ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/YZVXG7OOOXCX6VIPEMLFDPIPUTFAYWPE/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/YTMITQBGC23MSDHUCAPCVGLMVXIBXQTQ/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-42311