An attacker can send a request to the `V1/customers/me` endpoint with a specially crafted customer ID. There is a direct object reference in the HTML code of that endpoint that can be exploited to reach the `actions/admin/view/customers/me` endpoint. This can be done by setting a customer ID that has a direct object reference to the `actions/admin/view/customers/me` endpoint. An authenticated attacker can exploit this to access other customers via the system. In addition, a specially crafted request to the `actions/admin/view/orders/me` endpoint can be exploited to reach the `actions/admin/orders/edit/me` endpoint, which allows an attacker to access other orders via the system. An attacker could also exploit this to access other customers via the system and other orders via the system. At the time of advisory publication, there are no known vulnerabilities that can be exploited to exploit this issue. However this has been rated as a critical severity due to the fact that it can be exploited by malicious users to exploit system privileges and gain access to other systems via the system.
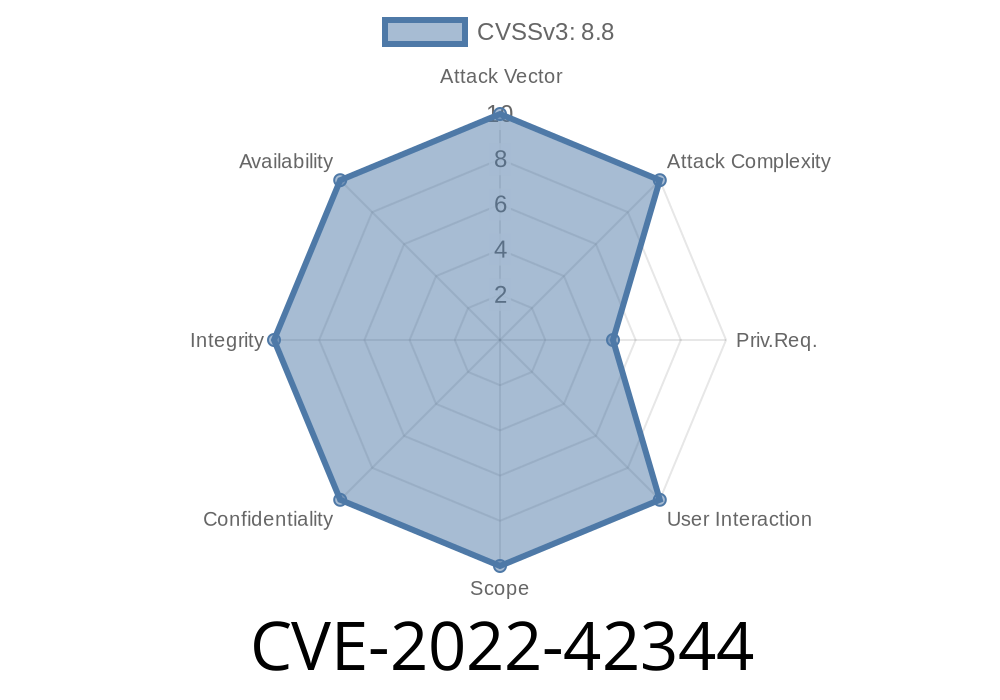
Vulnerability Hashtag: CVE-2022-42344
The title of the blog post is "6 Reasons Why Digital Marketing Is Important." The subheading is "Why Outsourcing SEO Can Be a Good Idea."
Vulnerability Symptoms and Fundamental Weakness
This vulnerability can be exploited by malicious users who can access other customers and orders without authorization.
Vulnerability overview
An attacker can send a request to the `V1/customers/me` endpoint with a specially crafted customer ID. There is a direct object reference in the HTML code of that endpoint that can be exploited to reach the `actions/admin/view/customers/me` endpoint. This can be done by setting a customer ID that has a direct object reference to the `actions/admin/view/customers/me` endpoint. An authenticated attacker can exploit this to access other customers via the system. In addition, a specially crafted request to the `actions/admin/view/orders/me` endpoint can be exploited to reach the `actions/admin/orders?edit/?me` endpoint, which allows an attacker to access other orders via the system. An attacker could also exploit this to access other customers via the system and other orders via the system. At the time of advisory publication, there are no known vulnerabilities that can be exploited to exploit this issue. However this has been rated as a critical severity due to the fact that it can be exploited by malicious users to exploit system privileges and gain access to other systems via the system.
Dependency Injection
Injection is a technique for locating code that needs to be executed in order to perform an action and injecting the code into the correct location. This allows the developer to avoid hard-coding specific information to a certain line of code.
The `V1/customers/me` endpoint is dependent on other services in order for it to function properly. In this situation, in order to access other customers via the system, you would first need access to those services. Therefore, if there were vulnerabilities present with those services, an attacker could exploit them and gain access to other systems via the system.
Timeline
Published on: 10/20/2022 17:15:00 UTC