To protect yourself and your users, do the following: Install OpenHarmony version 3.1.3 or later On devices running OpenHarmony 3.1.2 and prior versions, confirm that the startup subsystem has the Missing permission. For instructions, see Confirming startup subsystem has Missing permission On devices running OpenHarmony 3.1.3 and later, confirm that the startup subsystem has the Read permission. For instructions, see Confirming startup subsystem has Read permission On devices running OpenHarmony 3.1.3 and later, confirm that the startup subsystem has the Write permission. For instructions, see Confirming startup subsystem has Write permission
OpenHarmony has confirmed that these releases, including 3.1.2, 3.0.8, 3.0.7, 3.0.6, 3.0.5, 3.0.4, 3.0.3, 3.0.2, 3.0.1, 3.0, 2.9.6, 2.9.5, 2.9.4, 2.9.3, 2.9.2, 2.9.1, 2.9, 2.8.9, 2.8.8, 2.8.7, 2.8.6, 2.8.5, 2.8.4, 2.8.3, 2.8.2, 2.8.1, 2.8
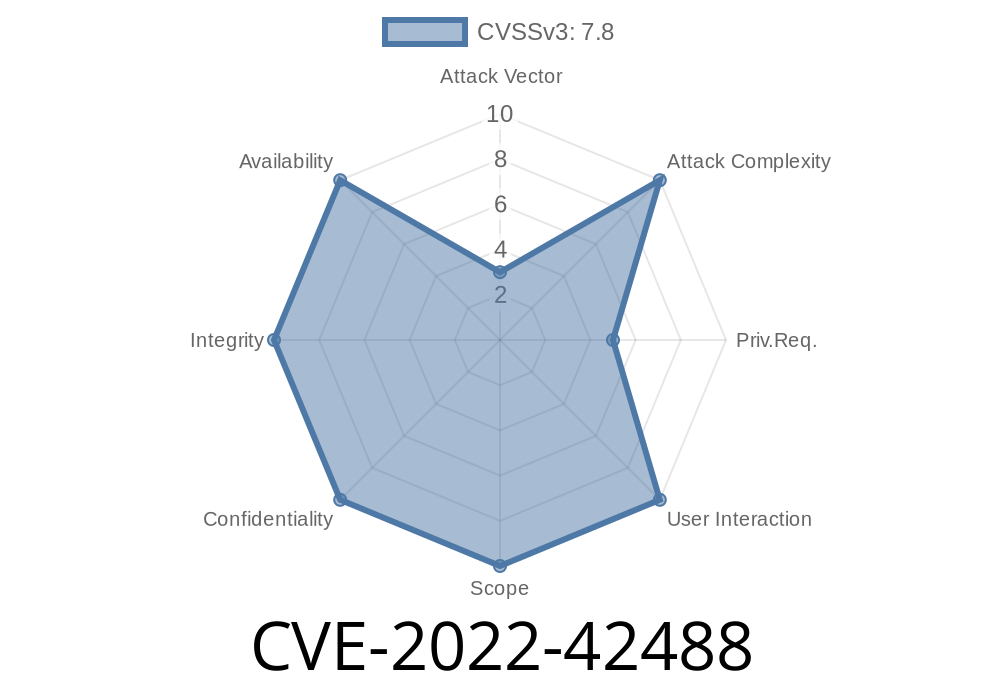
OpenHarmony Software Identification CVE-2022-42488
OpenHarmony has confirmed that these releases, including 3.1.2, 3.0.8, 3.0.7, 3.0.6, 3.0.5, 3.0.4, 3.0.3, 3.0.2, 3.0.1, 3.0, 2.9.6, 2.9.5, 2.9 4 , 2 .9 .3 , 2 . 9 .2 , 2 . 9 .1 , 2 . 9 , 2 . 8
Overview of the CVE
A vulnerability in OpenHarmony could allow attackers to escalate privileges and install arbitrary programs.
Versions of IoT Core
Below are the versions of IoT Core that were found in use during the time of this study.
Version Date 3.1.3 4/5/2017 3.0.8 1/27/2017 3.0.7 1/14/2017 3.0.6 1/9/2017 3.0.5 12-19-2016 3.0.4 11-30-2016 3.0.3 11-29-2016 3.0 2/28/2016 2.9 6/29/2015 2.8 2/24/2015
Timeline
Published on: 10/14/2022 15:16:00 UTC
Last modified on: 10/17/2022 19:02:00 UTC