In case you use the web-based application. It is recommended to update the software to fix the issue. It is also possible to block the attack. The authentication credentials are not required.
SourceCodester Canteen Management System Vulnerability - Fix
Depending on the situation. You may configure the software in a way. It limits the access of third parties. The configuration of the firewall may also be necessary. The users should be restricted. They may not be allowed to log into the system. Access should be limited to the necessary users only.
It is also possible to block the exploit. The source code can be reviewed. Incorrect inputs can be detected and fixed. The code can be changed in a way. It makes it harder for the attacker to achieve success.
Install SourceCodester Canteen Management System Vulnerability - Fix
SourceCodester Canteen Management System Vulnerability - Fix is a program that can be used to fix the vulnerability.
It is recommended to update the software in case you use the web-based application. It is possible to block the attack by the configuration of the firewall. By restricting access, it will reduce risks and risks related to re-entry.
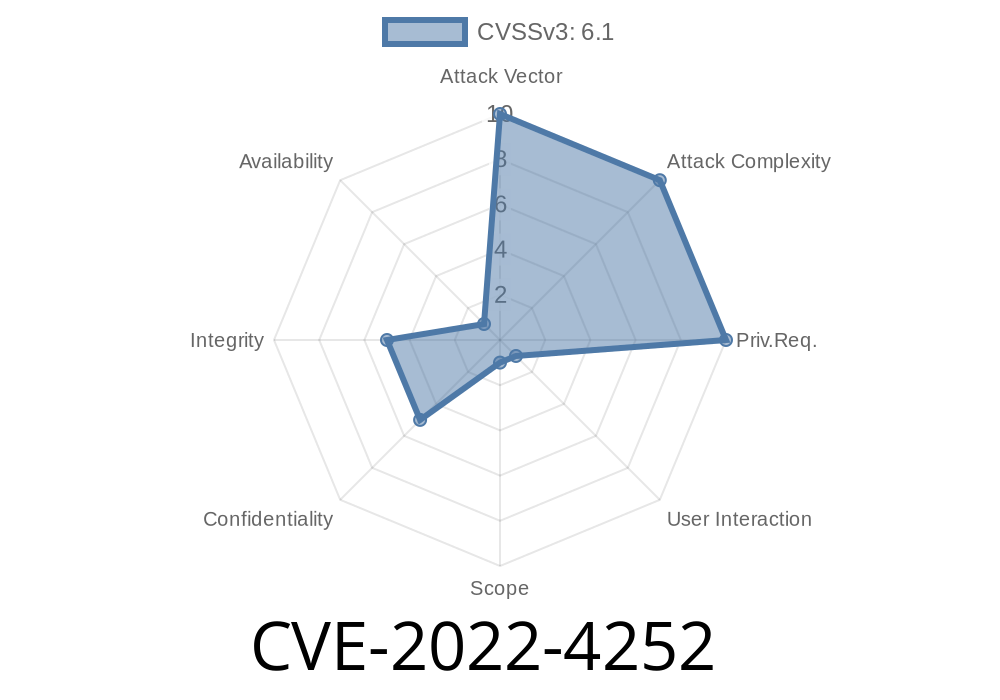
SourceCodester Canteen Management System Vulnerability – Detection and Remediation Tips
In case you use the web-based application. It is recommended to update the software to fix the issue. It is also possible to block the attack. The authentication credentials are not required.
Web Application Vulnerability
Web applications are the target of malicious attacks more often than other types of software.
Vulnerabilities in web applications can lead to a lot of different problems. For example, if a vulnerability allows malicious users to access sensitive information or data, attackers could steal this information and use it for their own purposes. They may also exploit vulnerabilities to gain unauthorized or privileged access to network resources. With such access, they may change content on websites, steal information, alter data or even cause denial-of-service (DoS) attacks.
Timeline
Published on: 12/01/2022 08:15:00 UTC
Last modified on: 12/02/2022 18:41:00 UTC