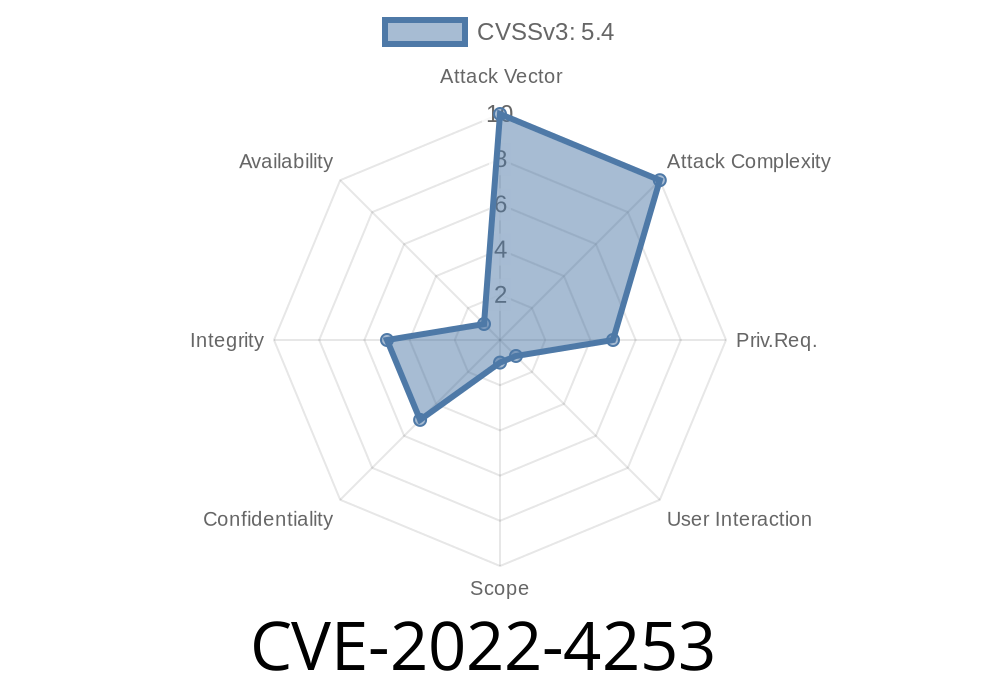
In late 2022, security researchers discovered a vulnerability in the popular SourceCodester Canteen Management System. This vulnerability, tracked as CVE-2022-4253 and referenced as VDB-214630, drew attention because it can be easily exploited from a remote location to run malicious scripts in the browser of other users. Let’s break down what happened, how it works, and what you can do about it. We’ll include code snippets and easy steps so you can see exactly what’s at risk.
1. What is CVE-2022-4253?
CVE-2022-4253 is a Cross-Site Scripting (XSS) vulnerability found in the *SourceCodester Canteen Management System*. Attackers can inject malicious JavaScript into specific pages, which will execute every time another user visits those pages. This type of bug is common but very dangerous, especially in software used to manage sensitive data.
The vulnerability is located in the customer.php file and is linked to the use of the builtin_echo function, which doesn’t properly filter user input.
2. Where’s the Vulnerability?
The problematic function is builtin_echo in customer.php. This is how a snippet of the code might look like (simplified for clarity):
<?php
// customer.php
function builtin_echo($data) {
echo $data;
}
...
if (isset($_GET['name'])) {
$name = $_GET['name'];
builtin_echo($name); // Vulnerable usage
}
?>
In this code, the value received from the user's name parameter is displayed on the webpage without any sanitization.
3. How Does the Exploit Work?
An attacker can craft a URL containing JavaScript code in the name parameter. When another user or even the administrator clicks the link, the script will execute in their browser.
A typical attack URL might look like
http://victim-site/customer.php?name=<script>alert('XSS');</script>;
The script inside the name field is *directly inserted* into the page's HTML and executed.
- This can lead to stolen cookies, session hijacking, redirecting users, or delivering more complex attacks.
Exploit URL
http://localhost/canteen/customer.php?name=<script>alert('Hacked')</script>;
Resulting Page Source (relevant part)
<html>
<head> ... </head>
<body>
<script>alert('Hacked')</script>
<!-- Rest of the page -->
</body>
</html>
When any user visits this URL, a popup with "Hacked" appears — clear proof of XSS.
6. Links & References
- NVD Official CVE Entry
- VulDB Reference: VDB-214630
- SourceCodester Canteen Management System
- Sanitize User Input: Always use functions like htmlspecialchars() or filter_var() in PHP
function builtin_echo($data) {
echo htmlspecialchars($data, ENT_QUOTES, 'UTF-8');
}
Summary
CVE-2022-4253 shows how even simple web applications can contain risky bugs with big impacts. The issue lies in trusting user input and displaying it without checks. Protect your users and your reputation by validating and escaping all input — always.
Stay secure. Stay smart.
*This guide was written exclusively to help users, students, and security enthusiasts understand the real-world implications of CVE-2022-4253 with practical, actionable advice. For more information, always check the official references.*
Timeline
Published on: 12/01/2022 08:15:00 UTC
Last modified on: 12/02/2022 18:43:00 UTC