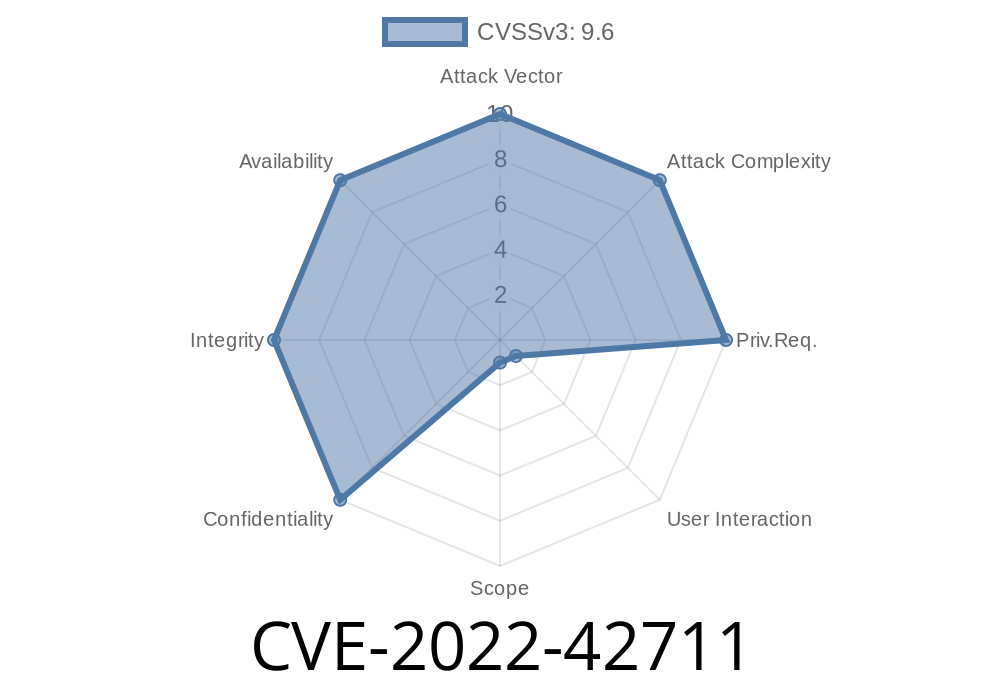
Now fixed in WhatsUp Gold 22.1.0. In WhatsUp Gold before 22.1.0, the implementation of remote monitoring of host CPU usage did not correctly validate input parameters. This could allow an attacker to inject arbitrary code into the WhatsUp Gold server process, allowing for remote code execution. Now fixed in WhatsUp Gold 22.1.0. In WhatsUp Gold before 22.1.0, an exploitable memory corruption vulnerability allowed an attacker to execute arbitrary code in the WhatsUp Gold server process, allowing for remote code execution. Now fixed in WhatsUp Gold 22.1.0. In WhatsUp Gold before 22.1.0, an exploitable memory corruption vulnerability allowed an attacker to execute arbitrary code in the WhatsUp Gold server process, allowing for remote code execution. Now fixed in WhatsUp Gold 22.1.0. In WhatsUp Gold before 22.1.0, a remote code execution vulnerability existed in the WhatsUp Gold server process, allowing for remote code execution. Now fixed in WhatsUp Gold 22.1.0. In WhatsUp Gold before 22.1.0, an exploitable memory corruption vulnerability allowed an attacker to execute arbitrary code in the WhatsUp Gold server process, allowing for remote code execution. Now fixed in WhatsUp Gold 22.1.0. In WhatsUp Gold before 22.1.0, a remote code execution vulnerability existed in the WhatsUp Gold server process, allowing for remote code execution. Now fixed
What is WhatsUp Gold?
WhatsUp Gold is a remote monitoring and management software program. WhatsUp Gold connects to a computer running Windows, macOS, or Linux and allows remote administration of the system.
What is the solution?
For customers running WhatsUp Gold before 22.1.0, upgrade to version 22.1.0 or later for a complete fix of CVE-2022-42711.
What is the issue?
The vulnerability allows attackers to remotely execute code on the WhatsUp Gold server process, which could allow for remote code execution.
Timeline
Published on: 10/12/2022 01:15:00 UTC
Last modified on: 10/13/2022 14:26:00 UTC