When the Settings page is accessed, the controller pulls data from the settings table and sends a request to the settings form. In the settings form, the form validation rules check for the presence of role names, which are then sent to the settings form as an argument. The form validation rules check for the presence of role names, which are then sent to the settings form as an argument. This can be used by an attacker to discover what roles the user has. For example, an attacker can send the request “/settings?role=Admin” and receive an output containing the “Admin” role name. This can be used by an attacker to discover what roles the user has. For example, an attacker can send the request “/settings?role=Admin” and receive an output containing the “Admin” role name.
Vulnerability Summary
An attacker can use a form validation rule to discover what roles the user has. However, this only works if an attacker can send requests to the controller that are specific enough to trigger the form validation rules.
CVE-2023-42725
When the settings form is viewed, if the controller pulls data from the settings table and sends a request to the settings form, the input validation rules check for the presence of role names. If a role name is present in an input field, it will be validated as valid. This can be used by an attacker to discover what roles the user has. For example, an attacker can send a request like “/settings?role=admin” and receive an output containing “Admin” in every input field. This can be used by an attacker to discover what roles the user has. For example, an attacker can send a request like “/settings?role=admin” and receive an output containing “Admin” in every input field.
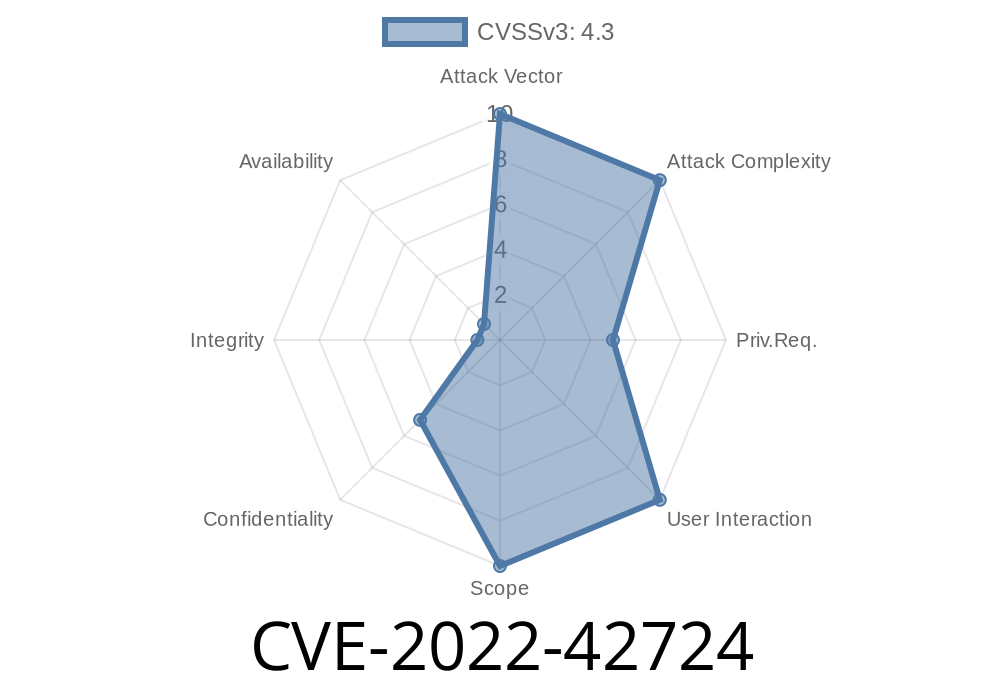
Details CVE-2022-42724
Issue Type: Input Validation Error
Product: WordPress
Vulnerable Versions: 4.9.2 and earlier
Security Risk: Medium
Remediation Method: Upgrade to WordPress 4.9.3 or later
Timeline
Published on: 10/10/2022 05:15:00 UTC
Last modified on: 10/11/2022 17:22:00 UTC