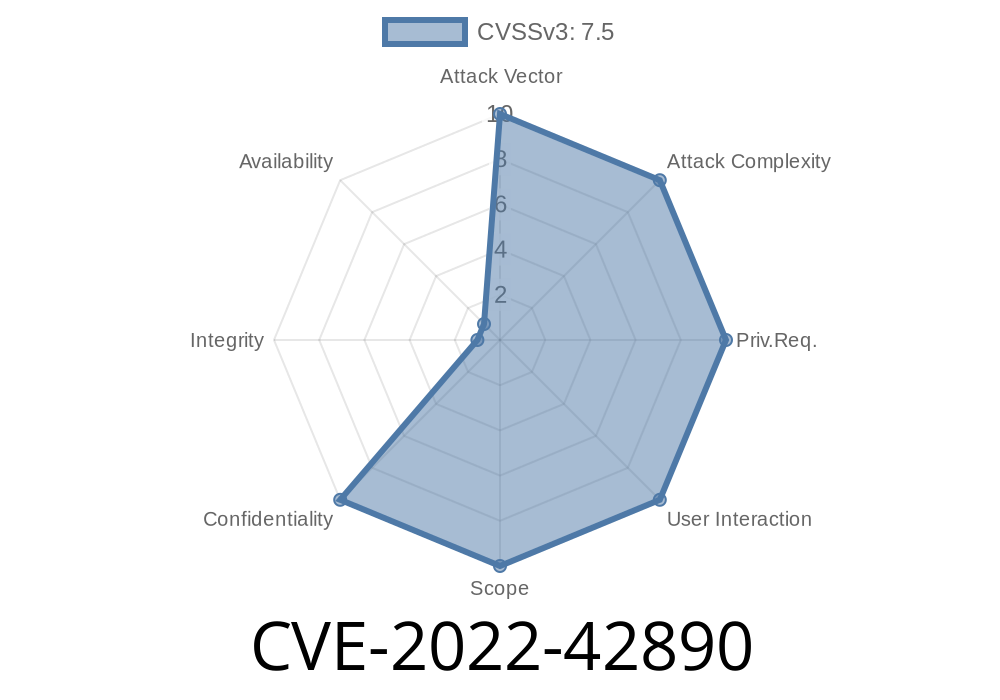
CVE-2022-42890 is a major security flaw found in Apache XML Graphics Batik, a popular open-source Java library for manipulating SVG (Scalable Vector Graphics) files. The vulnerability allows attackers to craft a malicious SVG image file that, when processed by vulnerable versions of Batik, will execute arbitrary Java code. This could mean remote code execution on your server or desktop application, all by just loading an SVG from an untrusted user!
The fix is available starting in version 1.16.
If your project uses Batik and processes third-party SVGs, your system might be at risk.
Render SVG to different formats like PNG or PDF.
Many developers use Batik without worrying about what’s inside the SVG files. But SVG supports JavaScript and even Java code embedding. Batik’s issue is that in the vulnerable versions, it accidentally allows Java code in SVG to be run.
How the Exploit Works
SVG is an XML-based file format for drawings. It can include not only graphic elements but also scripts. Older Batik versions did not check or block dangerous script features well.
Why is this dangerous?
Imagine letting users upload images to your Java web app or converting SVG files with Batik on your server. One malicious file could breach your whole system.
What Does a Malicious SVG Look Like?
An SVG file can contain script tags and "foreignObject" blocks that Batik might process, causing the JavaScript engine to execute code. Attackers then use various tricks to break out from the JavaScript context into the underlying Java environment.
Sample Malicious SVG
<?xml version="1." standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN"
"http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">;
<svg width="400px" height="110px"
xmlns="http://www.w3.org/200/svg";
xmlns:xlink="http://www.w3.org/1999/xlink";
onload="var runtime=Packages.java.lang.Runtime.getRuntime();
runtime.exec('calc');">
<text x="" y="15" fill="red">Malicious SVG</text>
</svg>
This SVG includes an onload event that, when processed by vulnerable Batik versions, will execute the Calculator app on Windows (as an example). In a real attack, this could be any shell command.
The fix is simple
> Upgrade Batik to version 1.16 or later!
- Apache Batik 1.16 Release Notes
- Download the fixed version from Maven Central
References & More Reading
- CVE Record: CVE-2022-42890
- Apache Batik Security Advisory
- Batik Official Website
- SVG and Security
Conclusion
CVE-2022-42890 is a widely exploitable vulnerability in Apache Batik before version 1.16. If you process SVG files from untrusted sources, update your dependencies immediately. Don’t risk a remote code execution attack – patch today.
Have specific questions? Leave a comment below or reach out to your security team for help!
*Exclusively written for you, in simple and clear language.*
Timeline
Published on: 10/25/2022 17:15:00 UTC
Last modified on: 12/08/2022 03:42:00 UTC