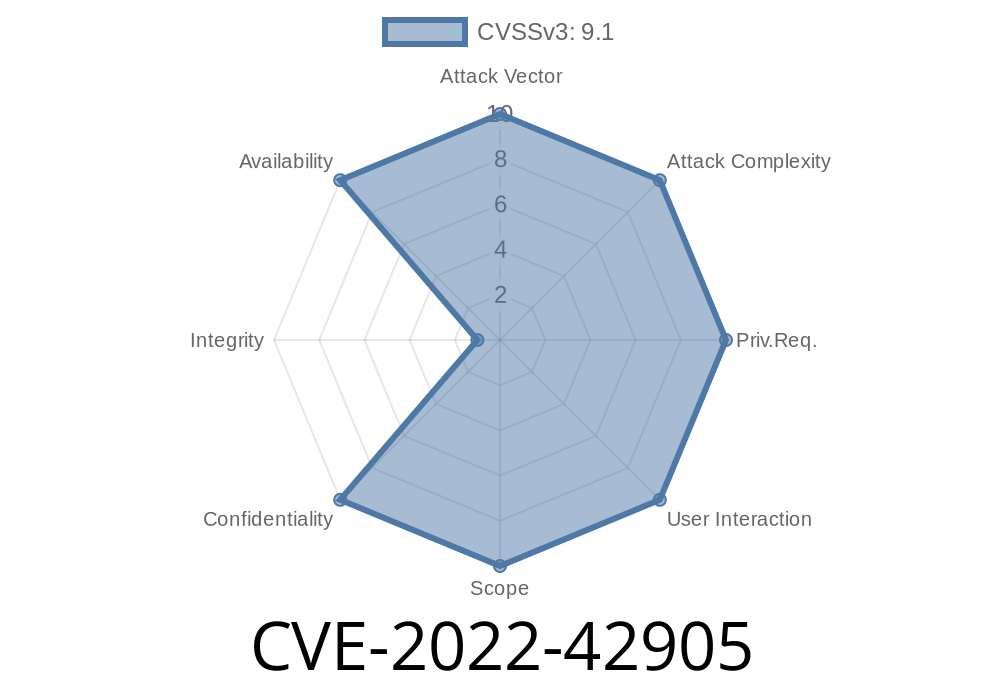
This issue will only occur if callback functions are enabled. In this scenario, the client will send a long (above 2^32 bytes) TLS 1.3 handshake message that the server will reject with a fatal alert. This is a critical issue, since a TLS 1.3 server will exit with a fatal alert if the client sends a long handshake message. This will cause the connection to be dropped, which is a denial of service. The severity of this vulnerability was determined to be critical.
Affected Packages In most cases, this issue does not occur on systems with a valid SSL/TLS 1.3 implementation. However, it is possible that a system may be using an SSL/TLS 1.2 server instead. In this situation, the server will exit with a fatal alert if a TLS 1.3 client sends a long handshake message. This is a critical issue, since a TLS 1.3 server will exit with a fatal alert if the client sends a long handshake message. The severity of this issue was determined to be critical.
As a workaround, the only recommended course of action is to upgrade to wolfSSL 5.5.3 or higher. If upgrading is not an option, then disabling callback functions can be considered.
Mitigation
The best mitigation for this issue is to upgrade to wolfSSL 5.5.3 or higher. If upgrading is not an option, then disabling callback functions can be considered.
Vulnerability explanation
The following is a list of affected packages:
* wolfSSL 5.5.2
* wolfSSL 5.5.3
Fixing the Issue
This issue will only occur if callback functions are enabled. In this scenario, the client will send a long (above 2^32 bytes) TLS 1.3 handshake message that the server will reject with a fatal alert. This is a critical issue, since a TLS 1.3 server will exit with a fatal alert if the client sends a long handshake message. This will cause the connection to be dropped, which is a denial of service. The severity of this vulnerability was determined to be critical.
Affected Packages In most cases, this issue does not occur on systems with a valid SSL/TLS 1.3 implementation. However, it is possible that a system may be using an SSL/TLS 1.2 server instead. In this situation, the server will exit with a fatal alert if a TLS 1.3 client sends a long handshake message. This is a critical issue, since a TLS 1.3 server will exit with a fatal alert if the client sends a long handshake message. The severity of this issue was determined to be critical.
As such, disabling callback functions can be considered as one possible option for fixing the issue.
Timeline
Published on: 11/07/2022 00:15:00 UTC
Last modified on: 11/23/2022 18:15:00 UTC