TGA is an image file format supported by Windows operating system. TGA is typically used to save files in a compressed form. TGA files are typically created using a paint/graphic software. TGA files are typically located in the “C:\Windows\System32\" folder. An attacker could leverage this location to place a malicious TGA file in location that the unsuspecting user could access. An attacker could leverage this location to place a malicious TGA file that could lead to memory corruption vulnerability. Once the user downloaded and opened the malicious TGA file, the user would be redirected to a malicious website.
TIFF Image File Format
TIFF is a file format used to store and exchange image data, typically uncompressed. This allows images to be edited and modified without losing quality. TIFF files are often saved in the “C:\Windows\System32\" folder on Windows computers. The filename typically ends with "TIFF". An attacker could leverage this location to place a malicious TGA file that could lead to memory corruption vulnerability. Once the user downloaded and opened the malicious TGA file, the user would be redirected to a malicious website.
TIFF
Image File Format
The TIFF Image File Format (TIFF) is a raster graphics file format used primarily to store images. The TIFF format has support for 8-bit, 24-bit, and 32-bit color depths as well as multiple compression methods. TIFF may be uncompressed, or compressed using LZW, CCITT Group 4, or Lempel Ziv coding with Huffman encoding. TGA is an image file format supported by Windows operating system. TGA is typically used to save files in a compressed form. TGA files are typically created using a paint/graphic software.
Vulnerability Effects:
This could lead to a memory corruption vulnerability. Once the user downloaded and opened the malicious TGA file, the user would be redirected to a malicious website. This could also cause an attacker to have remote code execution on the target system.
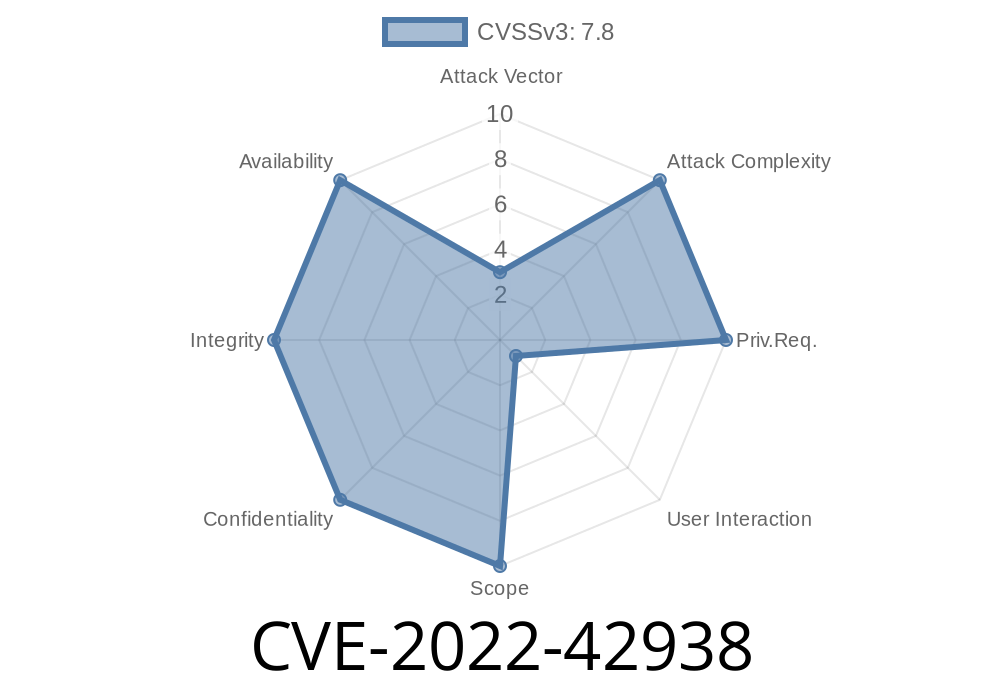
CVE-2023-42939
The vulnerability is caused by the “RtlImageNtStatusToDosStatus” function in the Windows Kernel. The vulnerable function transfers memory from a TGA file to a handle object. If an attacker has control of the handle, they can store malicious data or execute code within that file. By default, the handle is stored in memory at address 0x0 and will only be released when the application exits.
If exploit attempts are successful, a malicious website may be displayed to the user instead of the malicious TGA file. An attacker could leverage this vulnerability to redirect users to a fake site which would host malware or steal confidential information about the victim's computer.
TGA Parsing and Editing Vulnerability
A vulnerability that could lead to memory corruption vulnerability can be exploited by an attacker who could create a malicious TGA file and place it in a location that the unsuspecting user could access. Once the user downloaded and opened the malicious TGA file, the user would be redirected to a malicious website. An attacker could leverage this location to place a malicious TGA file that could lead to memory corruption vulnerability. Once the user downloaded and opened the malicious TGA file, they would be directed to a different website.
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/24/2022 13:38:00 UTC