TGA is an image file format supported by Windows operating system. TGA is typically used to save files in a compressed form. TGA files are typically created using a paint/graphic software. TGA files are typically located in the “C:\Windows\System32\" folder. An attacker could leverage this location to place a malicious TGA file in location that the unsuspecting user could access. An attacker could leverage this location to place a malicious TGA file that could lead to memory corruption vulnerability. Once the user downloaded and opened the malicious TGA file, the user would be redirected to a malicious website.
TIFF
Files: TGA, TIFF and RLE
TGA files are typically saved in a compressed form, but TIFF files are not. TIFF is the dominant image file format for Windows operating system. In contrast to other image formats, the compression mechanism used by TIFF does not rely on lossy compression. The popular RLE compression algorithm is used for all types of images in this format and it does not use any type of lossless compression techniques. Therefore, when confronted with a malicious binary file that is named as a .TGA file - users should be cautious. Additionally, users should exercise caution when receiving an email containing a .TGA attachment from an unknown sender.
An attacker could leverage this location to place a malicious TGA file that could lead to memory corruption vulnerability. Once the user downloaded and opened the malicious TGA file, the user would be redirected to a malicious website.
TGA Chunker
TGA Chunker is a software that allows users to extract the contents of TGA files. Once extracted, the user can view the contents of TGA files and extract them. This software supports extracting TGA, PNG, JPEG, BMP, and ICO images. Additionally, it supports extracting multiple files in batch mode.
It is also possible for an attacker to use this software to create a malicious TGA file containing a malicious payload with the intent to gain unauthorized access or cause harm into an unsuspecting user’s system.
An attacker could leverage this software by creating a malicious .TGA file that contains a malicious payload with the intent to gain unauthorized access or cause harm into an unsuspecting user’s system.
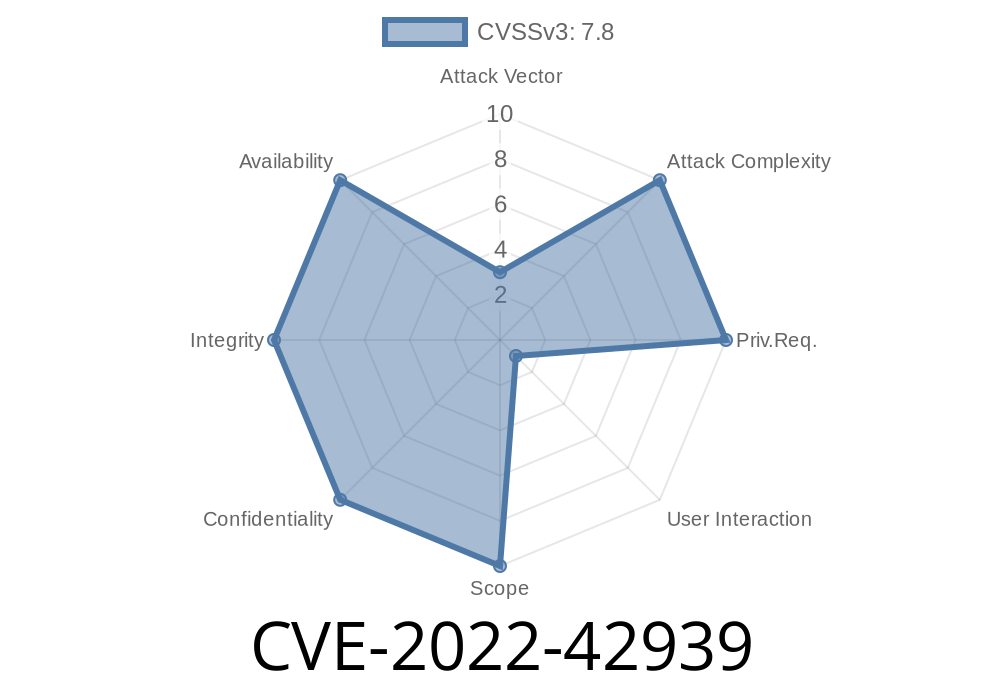
Vulnerability details
An attacker could leverage this vulnerability with exploit code. The exploit code would typically download a malicious payload and then run the payload on the target system. This would lead to memory corruption vulnerability in Windows operating system. Once the user downloaded and opened the malicious TGA file, the user would be redirected to a malicious website.
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/24/2022 13:40:00 UTC