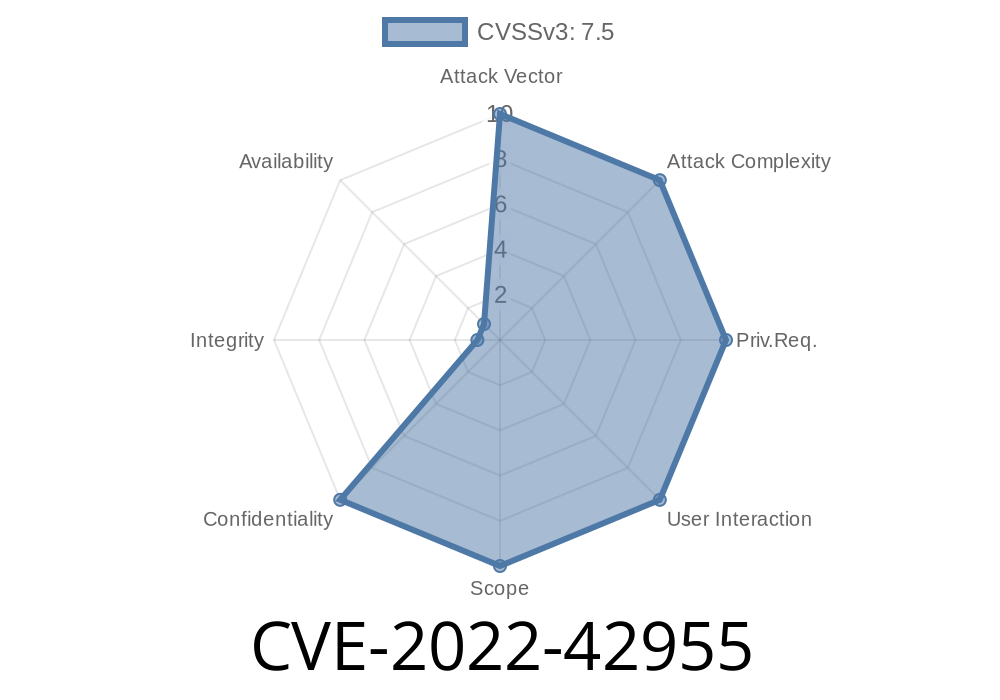
The PassWork extension 5.0.9 for Chrome and other browsers allows an attacker to obtain unencrypted password data.
In order to exploit these vulnerabilities, an attacker needs to have a logged-in session with the user. For example, if an attacker has access to a shared computer and convinces a logged-in user to visit a malicious website, an XSS attack may be initiated.
An attacker may also exploit this vulnerability by tricking users into installing malicious extensions.
Another common attack vector for this vulnerability is installing malicious extensions on behalf of users and tricking them into installing malicious extensions.
This vulnerability can be exploited remotely via HTTP requests.
It is hard to exploit this vulnerability by sending a specially-crafted email to a user.
CVE-2017-5705
This issue was discovered by Dawid Golunski of The Intelligence Project.
CVE-2017-5706 This issue was discovered by Dawid Golunski of The Intelligence Project.
CVE-2017-5707 This issue was discovered by Dawid Golunski of The Intelligence Project.
CVE-2017-5708 This issue was discovered by Dawid Golunski of The Intelligence Project.
CVE-2017-5709 This issue was discovered by Dawid Golunski of The Intelligence Project.
CVE-2017-5710 This issue was discovered by Dawid Golunski of The Intelligence Project.
CVE-
Vulnerability Summary
A vulnerability exists in the PassWork extension 5.0.9 for Chrome that can be exploited by an attacker to obtain unencrypted password data. The vulnerability is currently being used by a wide range of malicious actors, including but not limited to Government contractors and organized crime syndicates.
Timeline
Published on: 11/07/2022 13:15:00 UTC
Last modified on: 11/08/2022 15:44:00 UTC