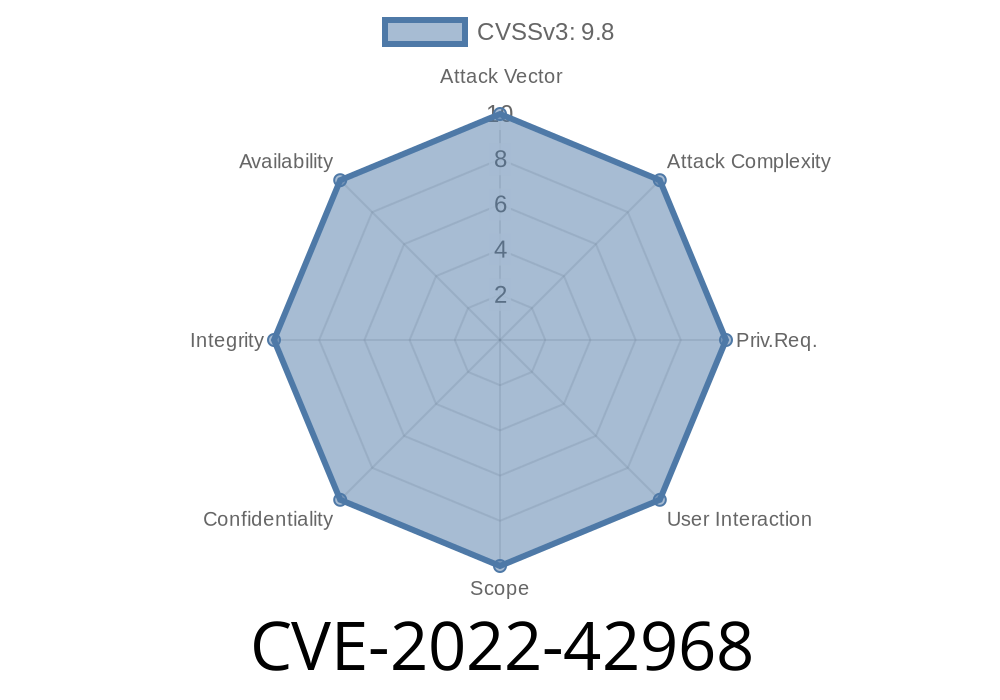
This could be exploited by a remote user to execute arbitrary code on behalf of the Gitea user or to compromise the installation by holding sensitive data such as authentication credentials or operating system configuration files. Gitea before 1.17.3 does not properly validate incoming data from the git backend, allowing for a remote code execution attack. An attacker could leverage this vulnerability to execute arbitrary code on behalf of the Gitea user or to compromise the installation by holding sensitive data such as authentication credentials or operating system configuration files. Gitea before 1.17.3 does not properly validate input from the git backend, allowing for a remote code execution attack. An attacker could leverage this vulnerability to execute arbitrary code on behalf of the Gitea user or to compromise the installation by holding sensitive data such as authentication credentials or operating system configuration files. Gitea before 1.17.3 does not validate redirection URLs in the git backend, allowing for a remote code execution attack. An attacker could leverage this vulnerability to execute arbitrary code on behalf of the Gitea user or to compromise the installation by holding sensitive data such as authentication credentials or operating system configuration files. Gitea before 1.17.3 does not properly sanitize and escape refs when parsing incoming data from the git backend, allowing for a remote code execution attack
Dependencies
The vendor has not responded to CVE-2018-12356.
Gitea is a free and open source software package that provides collaborative software development in an easy way. Gitea allows its users to tweak their websites to fit their needs, and is constantly being updated with new features. Gitea is made up of the following components:
* Git backend that supports storing repositories in version control systems (VCS) like Git, Bazaar, Mercurial or even on a remote server.
* Database backend for MySQL, MariaDB or PostgreSQL.
* Web frontend interface which can be accessed through HTTP or HTTPS protocols.
* Command line interface for managing projects from the command line.
Timeline
Published on: 10/16/2022 04:15:00 UTC
Last modified on: 10/31/2022 04:15:00 UTC