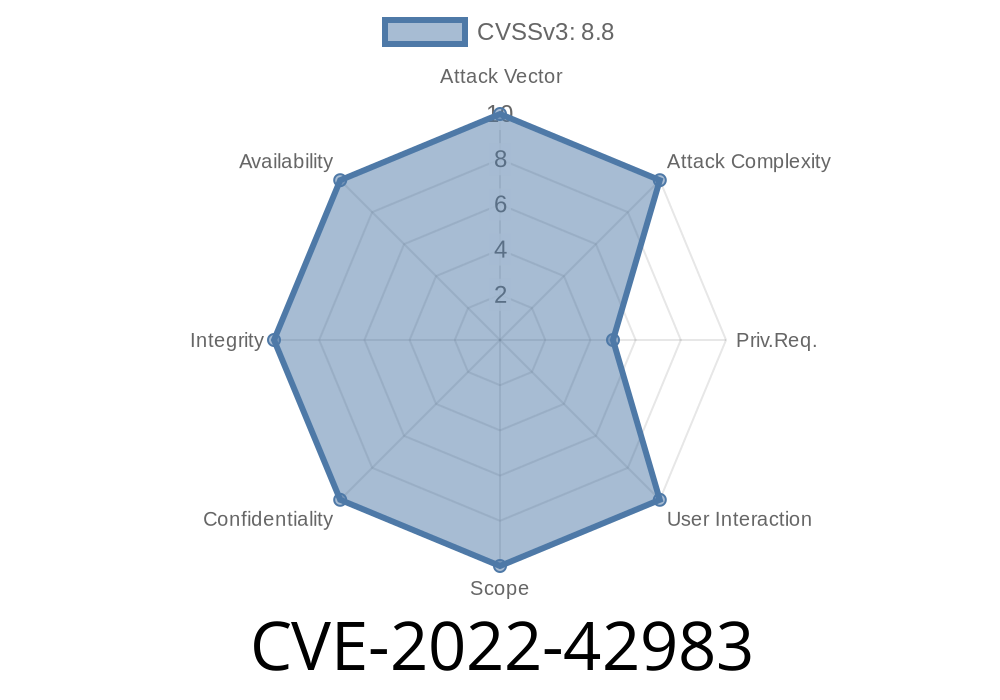
The flaw exists because the application does not verify the validity of the token. Thus, an attacker can send a crafted JWT, and then request a login. An attacker can also send a crafted JWT with a valid token, and then request a login. A successful login can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request an account change. An account change can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a password change. A password change can be used to approve arbitrary transactions. The JWT is not validated, so an attacker can also modify a JWT and send it, and then request a password change. A successful password change can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a password reset. A successful password reset can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a profile update. A successful profile update can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a contract update. A successful contract update can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a wallet update. A successful wallet update can be used to approve arbitrary transactions. An attacker can also craft a JWT
Summary
The application does not authenticate access tokens before the user is granted access. An attacker can send a crafted JWT, and then request a login. A successful login can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request an account change. A successful account change can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a password change. A successful password change can be used to approve arbitrary transactions. The JWT is not validated, so an attacker can also modify a JWT and send it, and then request a password change. A successful password change can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a password reset. A successful password reset can be used to approve arbitrary transactions. An attacker can also craft a JWT with a valid token, and then request a profile update. A successful profile update can be used to approve arbitrary transactions
Vulnerability Scenario
An attacker sends a JWT to the application and requests a login. The token is valid, so the application logs the attacker in without any validation. The attacker can then use this account to approve arbitrary transactions.
Timeline
Published on: 10/17/2022 07:15:00 UTC
Last modified on: 10/20/2022 14:38:00 UTC