D-Link DIR-816 A2 1.10 B05 was found to be vulnerable to cross-site request forgery (CSRF) flaws due to the lack of a properly implemented CSRF protection header. The issues were discovered during internal testing. D-Link DIR-816 A2 1.10 B05 was also found to be vulnerable to information leak flaws due to the lack of input sanitization. The issues were discovered during internal testing. Finally, D-Link DIR-816 A2 1.10 B05 was found to suffer from a command injection vulnerability due to the lack of any sort of non-persistent session token. The issue was discovered during internal testing.
D-Link DIR-816 A2 1.10 B05 users should update the firmware to mitigate the issues. https://vulnerability alerts. D-Link DIR-816 A2 1.10 B05 users are advised to exercise caution when inputting data into the config form for administrative purposes.
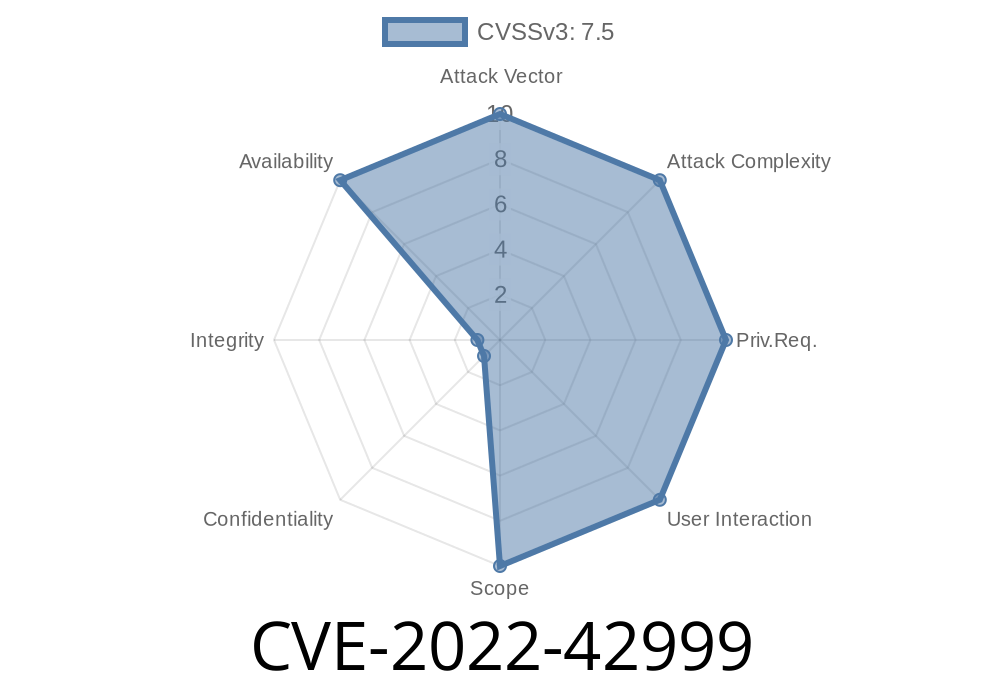
D-Link DIR-816 A2 1.10 B05 Software Vulnerabilities
D-Link DIR-816 A2 1.10 B05 suffers from multiple software vulnerabilities, which may lead to a remote code execution vulnerability or information leak vulnerability if exploited. Other issues include command injection vulnerabilities and lack of proper CSRF protection.
The following is the list of vulnerabilities found in D-Link DIR-816 A2 1.10 B05 software:
1) Cross-domain request forgery (CSRF) - An attacker would need to entice the victim to click on a malicious link for this exploit to work. The victim would then be redirected to a web page controlled by the attacker without the knowledge of the user.
2) Information leak vulnerabilities - There are two separate flaws here that affect server-side scripts and client-side scripts respectively. If an attacker were able to exploit these flaws, they would have access to some confidential data on the system such as authentication tokens and authorization codes.
3) Command injection vulnerabilities - This type of vulnerability allows an attacker to execute arbitrary commands at a specific point in time. An attacker could use this flaw to read or delete sensitive information or even run arbitrary commands with elevated privileges on the system.
4) Non-persistent session token vulnerability - Normally, when you log into your device, you will receive a non-persistent session token that can be used across different sessions on your device without being reissued, but with DIR-816 A2 1.10
D-Link DIR-816 A2 1.10 B05 Software Overview
The D-Link DIR-816 A2 1.10 B05 is an 802.11ac Wi-Fi router that supports MU-MIMO technology. It features a 1GHz dual core processor and 512MB of RAM, as well as eight external antennas. The router also supports a USB 2.0 port for hard drive sharing or printer sharing. In addition to its Wi-Fi capabilities, the device also contains four Gigabit Ethernet ports for wired connections. The device's firmware can be upgraded via the web interface or by connecting directly to the system using a computer running DDNS or Telnet access.
The software is designed with ease of use in mind, which means it has been optimized for both novice and advanced users alike. Some of these features include pre-defined SSIDs, channel surfing and band selection, parental controls, guest networks and more!
D-Link DIR-816 A2 1.10 B05 Software Vulnerability Details
1) D-Link DIR-816 A2 1.10 B05 suffers from a CSRF vulnerability due to the lack of a properly implemented CSRF protection header. 2) D-Link DIR-816 A2 1.10 B05 is vulnerable to information leak flaws due to the lack of input sanitization. 3) Finally, D-Link DIR-816 A2 1.10 B05 is vulnerable to command injection due to the lack of any sort of non-persistent session token.
D-Link DIR-816 A2 1.10 B05 users should update the firmware to mitigate the issues. https://vulnerability alerts.
CSRF Protection Header Issue
D-Link DIR-816 A2 1.10 B05 suffers from a CSRF flaw due to the lack of a properly implemented CSRF protection header. This issue was discovered during internal testing.
Timeline
Published on: 10/26/2022 19:15:00 UTC
Last modified on: 10/28/2022 14:31:00 UTC