OpenCATS is a popular open-source Applicant Tracking System (ATS) used by many organizations for recruitment management. In October 2022, a security issue surfaced in version .9.6 that affects the entriesPerPage parameter – allowing attackers to inject scripts via Reflected Cross-Site Scripting (XSS). In this post, we'll break down what happened, show you a working exploit, and discuss how to protect against it.
What is Reflected XSS?
Reflected XSS occurs when user-supplied data in a request is immediately used by the application to create a response page, but without proper sanitization or escaping. If that data includes malicious JavaScript code, the victim’s browser will execute it, potentially giving attackers the ability to steal cookies, session information, or perform actions as the user.
The Vulnerability
Product: OpenCATS
Affected Version: .9.6
Vulnerability: Reflected Cross-Site Scripting (XSS)
Parameter: entriesPerPage
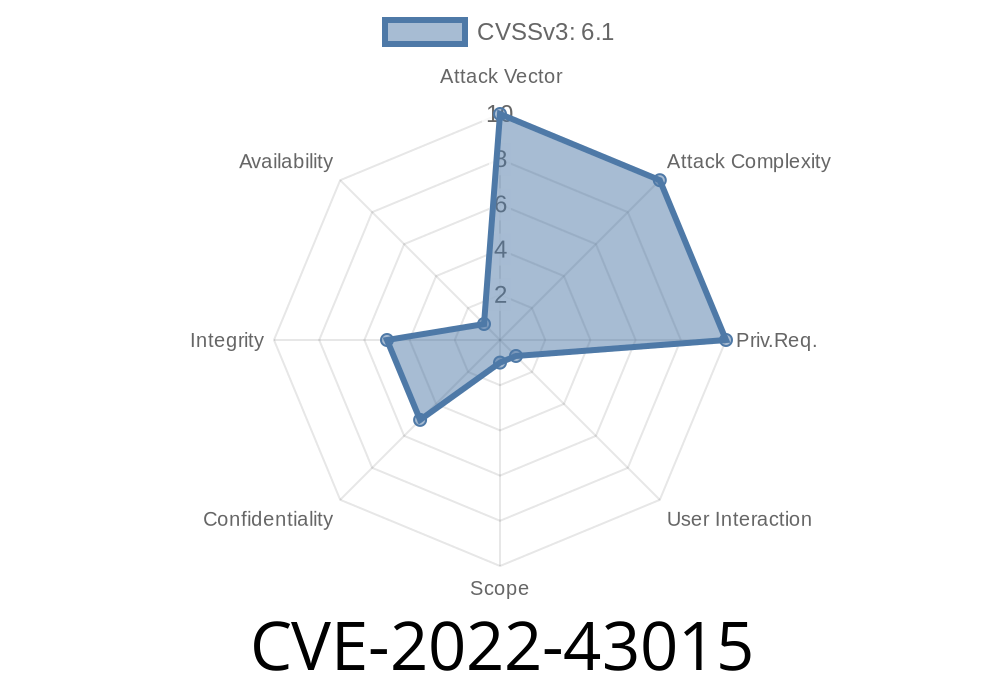
CVE ID: CVE-2022-43015
This bug exists because the application does not properly sanitize the input of the entriesPerPage parameter within URLs, and outputs it directly into the HTML content.
Here is a simplified version to illustrate the issue (the real code will be slightly different)
// search.php or related component
$entriesPerPage = $_GET['entriesPerPage'] ?? 10;
// ... usage in the HTML below ...
echo "<input type='hidden' name='entriesPerPage' value='" . $entriesPerPage . "' />";
If the parameter is not properly sanitized, passing a value like <script>alert(1)</script> will result in this being injected into the page's source and executed by browsers.
An attacker can craft a malicious URL like
http://victim-site.com/search.php?entriesPerPage=<script>alert('XSS')</script>;
When a victim clicks this link, their browser receives a page with the following HTML snippet
<input type='hidden' name='entriesPerPage' value='<script>alert("XSS")</script>' />
This causes the payload <script>alert("XSS")</script> to execute immediately, displaying an alert box. In a real attack, the payload could steal the user’s session cookies or perform more harmful actions.
You can try the following URL (replace the domain with your own testing OpenCATS instance)
http://localhost/OpenCATS/search.php?entriesPerPage=<script>alert(document.cookie)</script>;
Warning: Never test this on a live or production site. Only use safe, local, or authorized environments for testing.
Sanitize all user inputs before including them in the page. In PHP, you can use htmlspecialchars()
echo "<input type='hidden' name='entriesPerPage' value='" . htmlspecialchars($entriesPerPage, ENT_QUOTES, 'UTF-8') . "' />";
Only accept valid integers for entriesPerPage
$entriesPerPage = isset($_GET['entriesPerPage']) ? (int) $_GET['entriesPerPage'] : 10;
3. Update OpenCATS
Check the official OpenCATS GitHub for patches and update to the latest version as soon as possible.
References
- NVD Entry: CVE-2022-43015
- Exploit Database (if available)
- OpenCATS GitHub
- OWASP XSS Guide
Conclusion
CVE-2022-43015 exposes how even small oversights in input handling can lead to significant vulnerabilities. If you run OpenCATS or similar web applications, be sure to validate and escape all user data, and stay on top of security advisories and updates. Cross-site scripting is a common pitfall – but with a little effort, it’s also easily preventable.
Timeline
Published on: 10/19/2022 18:15:00 UTC
Last modified on: 10/20/2022 05:46:00 UTC