An attacker can exploit this to execute arbitrary SQL commands with the privileges of the user that installed the application. OpenCATS version 0.9.6 was confirmed to be vulnerable to SQL injection. The vulnerable code was identified in the /admin/settings/preferences/entry_types_values.py file. The entry_types_values.py file was found to have the following vulnerable code: An attacker can inject malicious SQL code into the 'preferences.entry_types' table to run unauthorized SQL commands. The entry_types_values.py file was found to have the following vulnerable code: -------------- 1. A user with the 'admin' role can add, edit, or delete any entry type. An attacker with the 'admin' role can exploit this to add, edit, or delete arbitrary entries to the 'preferences.entry_types' table, then run unauthorized SQL commands. An attacker with the 'admin' role can exploit this to inject malicious SQL code into the 'preferences.entry_types' table to run unauthorized SQL commands. -------------- End users are encouraged to update to version 0.9.7 of OpenCATS as soon as possible.
Vulnerability details
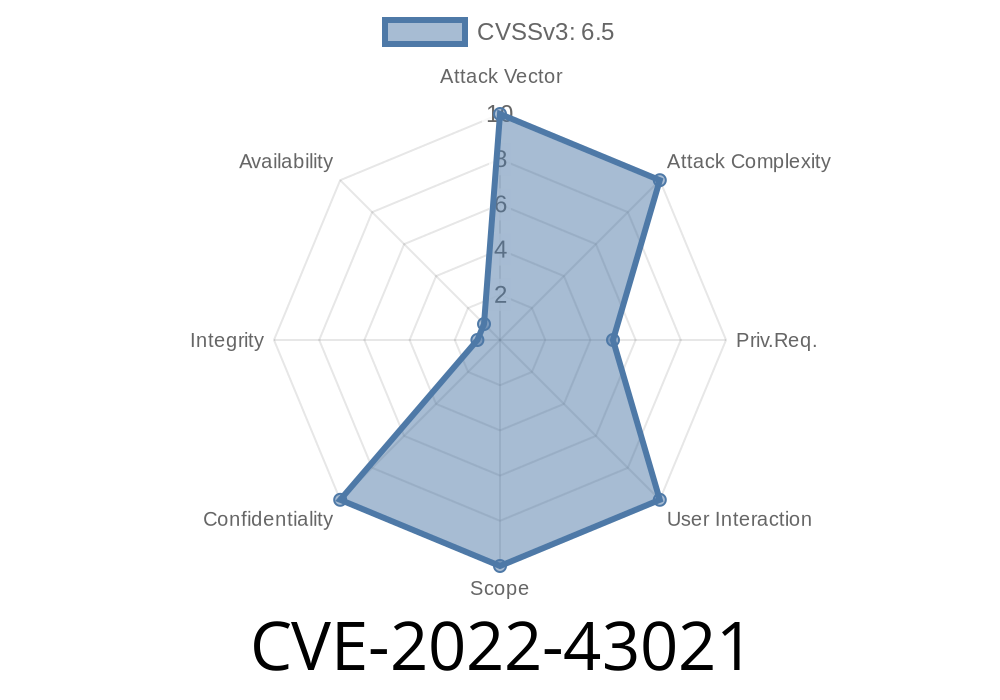
In order to exploit CVE-2022-43021, an attacker needed to be in the "admin" role. The vulnerability was confirmed in OpenCATS version 0.9.6, and a patch was released shortly after.
Timeline
Published on: 10/19/2022 18:15:00 UTC
Last modified on: 10/20/2022 05:47:00 UTC