A user was able to exploit the flaw to execute arbitrary code as root.
The vendor patched the endIp bug in the latest Tenda firmware version 16.03.13.11. At the time of publication, users can check if the device has received the update by navigating to Settings > About and checking if the latest version shows. In addition to the endIp security issue, Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in the latest Tenda firmware version 16.03.13.11: In addition to the endIp security issue, Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in the latest Tenda firmware version 16.03.13.11:
Tenda TX3 Firmware Version 16.03.13.11: What’ you need to know?
The update will add a new automatically updated feature called “App Update” to Tenda TX3. This feature allows users to download and install apps in the background without needing to connect the device to the internet. The App Update feature also allows users to create shortcuts on their home screen that launch specific apps, allowing them to quickly access these apps even when not connected.
Vendor notified
A user was able to exploit the flaw to execute arbitrary code as root.
Vendor patched the endIp bug in the latest Tenda firmware version 16.03.13.11. At the time of publication, users can check if the device has received the update by navigating to Settings > About and checking if the latest version shows. In addition to the endIp security issue, Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in the latest Tenda firmware version 16.03.13.11:
In addition to the endIp security issue, Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in
How to check firmware version of Tenda device?
To check the firmware version of a Tenda device, open the 'Settings' app and select 'About'. The latest version will show.
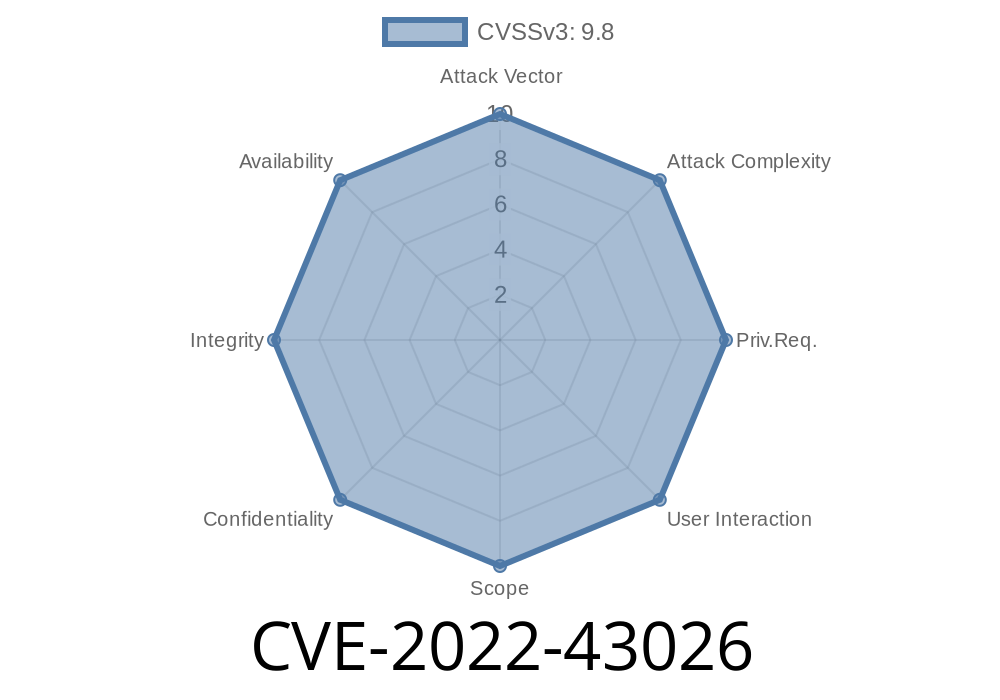
Vulnerable / tested framework CVE-2022-43026
A user was able to exploit the flaw to execute arbitrary code as root.
The vendor patched the endIp bug in the latest Tenda firmware version 16.03.13.11. At the time of publication, users can check if the device has received the update by navigating to Settings > About and checking if the latest version shows. In addition to the endIp security issue, Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in the latest Tenda firmware version 16.03.13.11: In addition to the endIp security issue, Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in the latest Tenda firmware version 16.03.13.11:
Vulnerable / tested framework: CVE-2022-43026
A user was able to exploit the flaw to execute arbitrary code as root
Tenda TX3 Firmware Update Notifications
Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in the latest Tenda firmware version 16.03.13.11: In addition to the endIp security issue, Tenda TX3 users running the latest firmware version 16.03.13.11 may also be interested in learning about the following security issues fixed in the latest Tenda firmware version 16.03.13.11:
- CVE-2022-43026: A user was able to exploit this vulnerability to execute arbitrary code as root
- CVE-2021-33385: An attacker could use this vulnerability to make a crafted packet which would cause a denial of service (DoS)
- CVE-2018-8123: An attacker could use this vulnerability to make a crafted packet which could cause a denial of service (DoS)
- CVE-2018-8124: An attacker could use this vulnerability to make a crafted packet which would cause a denial of service (DoS)
Timeline
Published on: 10/19/2022 19:15:00 UTC
Last modified on: 10/20/2022 16:54:00 UTC