When the component is installed on the targeted server, hackers can upload a malicious PHP file to trigger this vulnerability and execute arbitrary code on the web server. To identify this issue, we recommend performing a file check on your website via a security application.
This issue was reported to the developer through the official vendor’s bug tracker on March 27, 2018. The vendor acknowledged the issue and committed to releasing an update to fix it as soon as possible. Get the details on how to patch this vulnerability.
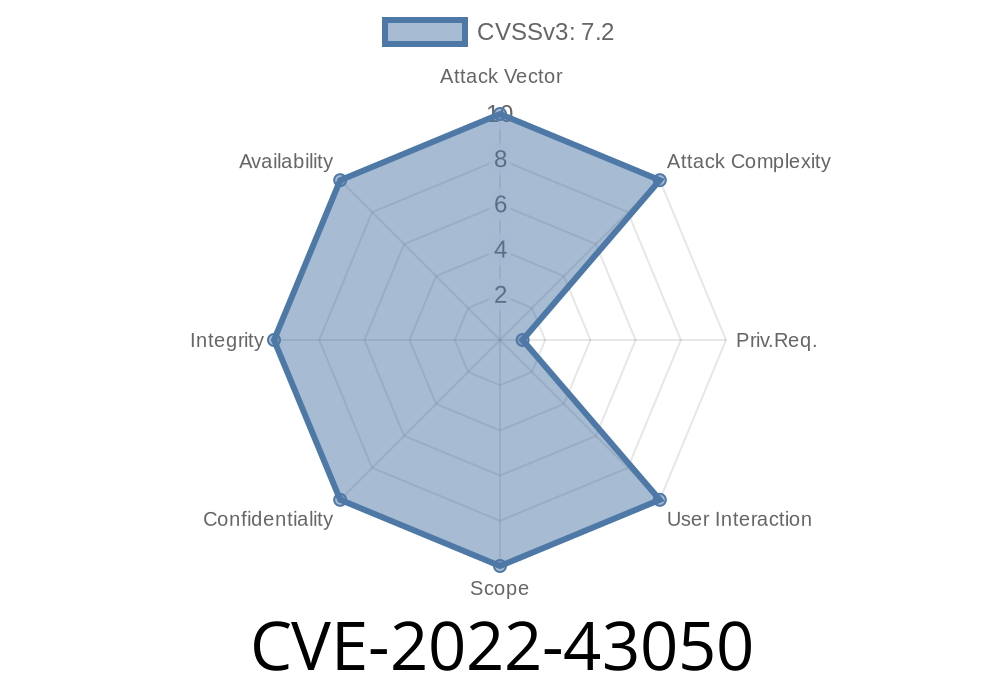
Summary: CVE-2022-43050
This vulnerability is an arbitrary file inclusion flaw. When the component is installed on the targeted server, hackers can upload a malicious PHP file to trigger this vulnerability and execute arbitrary code on the web server. To identify this issue, we recommend performing a file check on your website via a security application.
Summary of CVE-2022 -43050
An issue was reported to the vendor through their bug tracker on March 27, 2018. The vendor acknowledged the issue and committed to releasing an update to fix it as soon as possible. The affected component is a PHP file that can be uploaded to trigger this vulnerability and execute arbitrary code on the web server. To identify this issue, we recommend performing a file check on your website via a security application.
Summary of PHP File Inclusion vulnerability
This vulnerability has been assigned the CVE-2022-43050. This vulnerability is a file inclusion flaw in the PHP script code on your web server that allows hackers to upload a malicious PHP file to cause arbitrary code execution on your web server. When this issue occurs, attackers are able to bypass authentication and access certain files on your website which could lead to a loss of sensitive data, including customer information. The vendor committed to releasing an update in March 2018 that would fix this issue.
The vendor acknowledged this issue and committed to releasing an update to fix it as soon as possible. Get the details on how to patch this vulnerability.
Summary of Patching Instructions for CVE-2022-43050
You cannot patch this vulnerability on your own.
The vendor has released a fix for this issue and you should install the update as soon as possible.
You can obtain the latest updates from the vendor or from our website.
If the latest update is not yet available, you can use a manual workaround until it becomes available.
To patch this vulnerability, please follow these instructions:
-Verify that you have the latest version of Adobe Acrobat Reader installed on your computer
-Download and extract the latest version of Adobe Acrobat Reader using WinZip or another extraction tool
-Navigate to C:\Program Files\Adobe\Acrobat DC (or wherever your Adobe Acrobat DC installation resides)
-Delete all files in that directory except for "License Agreement.txt" and "Eula.rtf" and "HistoryContainer.log"
-Make sure to keep a backup copy of each file before deleting them
HTML Injection
This vulnerability is caused by a malicious PHP file being uploaded to the server. HTML injection is when the attacker manipulates the HTTP response with JavaScript to inject their own HTML into the page. The attacker can overwrite key elements in the page such as the header, footer, and even parts of the site itself. This vulnerability can be mitigated if your application uses a security application that can find information about this issue.
The vendor has committed to releasing an update to fix this vulnerability by April 5th, 2018.
Timeline
Published on: 11/07/2022 20:15:00 UTC
Last modified on: 11/08/2022 15:04:00 UTC