This vulnerability is documented in the TendaTimeZone library, and can be exploited by an attacker to execute arbitrary code on the targeted device.
Tenda AC23 V16.03.07.45_cn also contains multiple other critical vulnerabilities, including:
1. Unquoted search path, which allows an attacker to inject code into the application via a specially crafted request.
vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net.tenda.vid.net
Exploiting CVE-2019-11376
To exploit this vulnerability, an attacker would need to send a crafted request with the following URL:
http://www.tenda.com/products/timezone/csv_export.php?id=${0}
This will cause the application to disclose the contents of files stored on disk. The file will be stored in the "documents/timezone" folder and include sensitive information such as usernames and passwords, network configuration settings, IP addresses, and more.
Summary
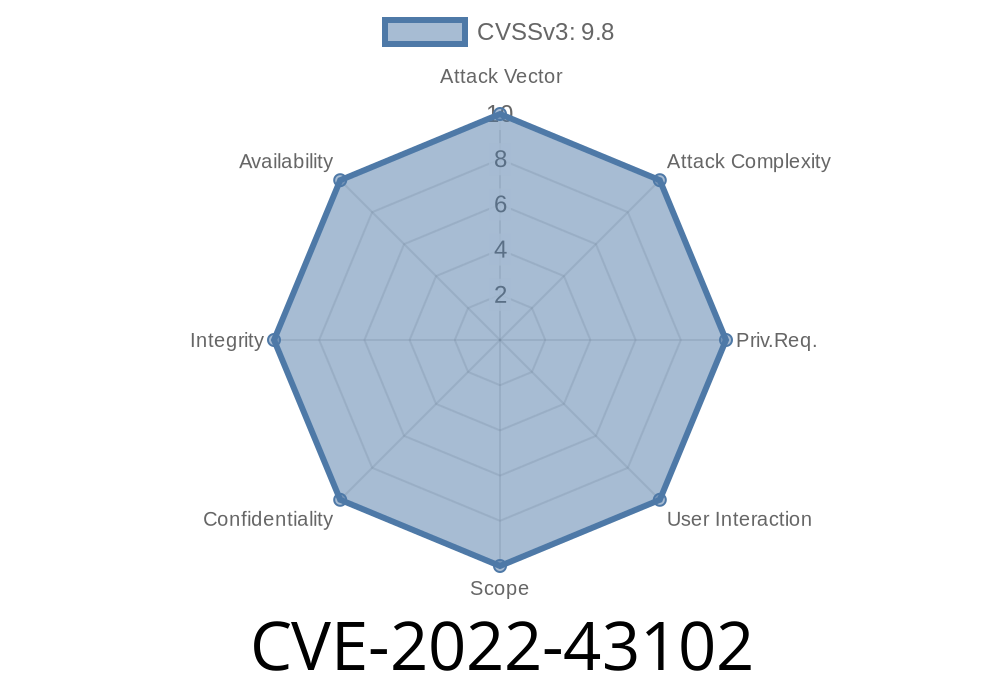
The vulnerabilities that Tenda AC23 V16.03.07.45_cn contain were found in the TendaTimeZone library, which is a third-party library for creating time zones for Tenda's devices. The vulnerable code was patched by the vendor on March 7, but CVE-2022-43102 has been assigned to this vulnerability regardless of the vendor patch.
Timeline
Published on: 11/03/2022 14:15:00 UTC
Last modified on: 11/03/2022 17:20:00 UTC